
Data Driven Decision Making using Analytics
- 138 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Data Driven Decision Making using Analytics
About this book
This book aims to explain Data Analytics towards decision making in terms of models and algorithms, theoretical concepts, applications, experiments in relevant domains or focused on specific issues. It explores the concepts of database technology, machine learning, knowledge-based system, high performance computing, information retrieval, finding patterns hidden in large datasets and data visualization. Also, it presents various paradigms including pattern mining, clustering, classification, and data analysis. Overall aim is to provide technical solutions in the field of data analytics and data mining.
Features:
- Covers descriptive statistics with respect to predictive analytics and business analytics.
- Discusses different data analytics platforms for real-time applications.
- Explain SMART business models.
- Includes algorithms in data sciences alongwith automated methods and models.
- Explores varied challenges encountered by researchers and businesses in the realm of real-time analytics.
This book aims at researchers and graduate students in data analytics, data sciences, data mining, and signal processing.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1Securing Big Data Using Big Data Mining
- 1.1Big Data
- 1.1.1Big Data V’s
- 1.1.1.1Volume
- 1.1.1.2Variety
- 1.1.1.3Velocity
- 1.1.1.4Veracity
- 1.1.1.5Validity
- 1.1.1.6Visualization of Big Data
- 1.1.1.7Value
- 1.1.1.8Big Data Hiding
- 1.1.2Challenges with Big Data
- 1.1.3Analytics of Big Data
- 1.1.3.1Use Cases Used in Big Data Analytics
- 1.1.3.1.1Amazon’s “360-Degree View”
- 1.1.3.1.2Amazon – Improving User Experience
- 1.1.4Social Media Analysis and Response
- 1.1.4.1IoT – Preventive Maintenance and Support
- 1.1.4.2Healthcare
- 1.1.4.3Insurance Fraud
- 1.1.5Big Data Analytics Tools
- 1.1.5.1Hadoop
- 1.1.5.2MapReduce Optimize
- 1.1.5.3HBase Hadoop Structure
- 1.1.5.4Hive Warehousing Tool
- 1.1.5.5Pig Programming
- 1.1.5.6Mahout Sub-Project Apache
- 1.1.5.7Non-Structured Query Language
- 1.1.5.8Bigtable
- 1.1.6Security Threats for Big Data
- 1.1.7Big Data Mining Algorithms
- 1.1.8Big Data Mining for Big Data Security
- 1.1.8.1Securing Big Data
- 1.1.8.2Real-Time Predictive and Active Intrusion Detection Systems
- 1.1.8.3Securing Valuable Information Using Data Science
- 1.1.8.4Pattern Discovery
- 1.1.8.5Automated Detection and Response Using Data Science
- 1.1.9Conclusions
1.1 Big Data
- Interception or corruption of data in transit.
- Data in storage which can be held internee by malicious parties or hackers.
- Output data can also be a point of malicious attack.
- Low or no encryption mechanism over the variety of data sources.
- Incompatibility resulting from the various forms of data implementation from different sources.
1.1.1 Big Data V’s
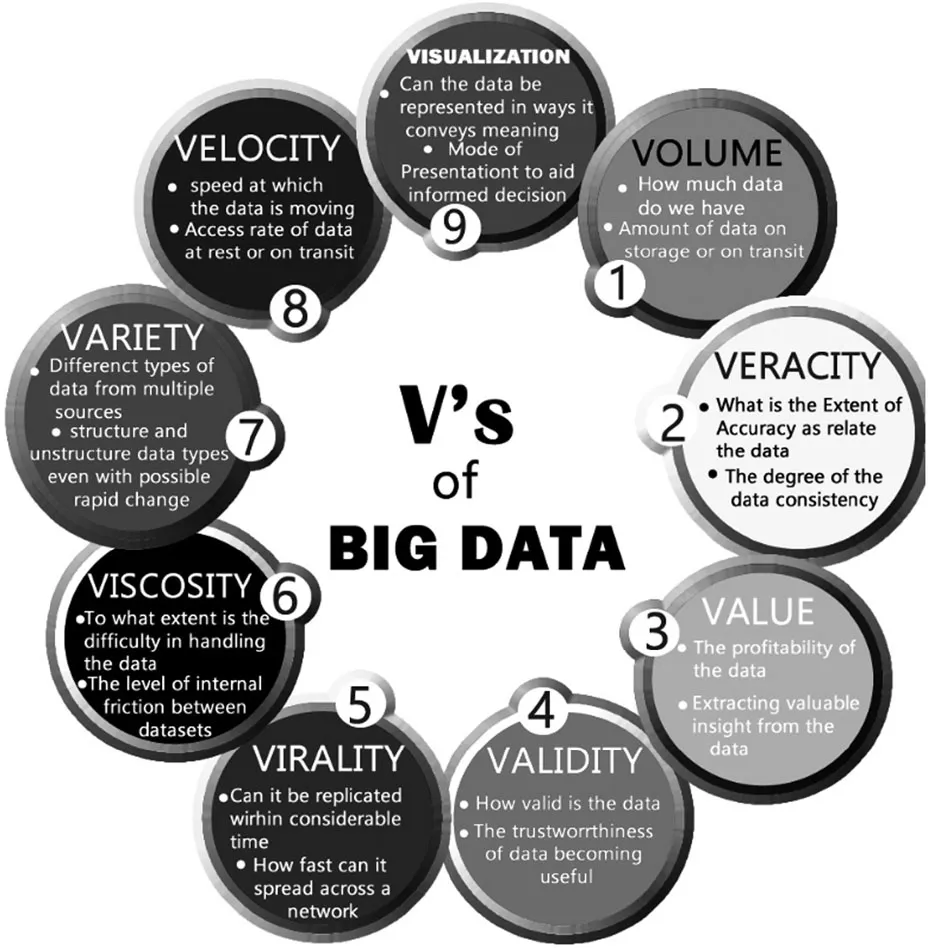
1.1.1.1 Volume
1.1.1.2 Variety
1.1.1.3 Velocity
1.1.1.4 Veracity
- Do you have faith in the data you gathered?
- Is the data enough reliable to gather insight?
1.1.1.5 Validity
1.1.1.6 Visualization of Big Data
1.1.1.7 Value
1.1.1.8 Big Data Hiding
1.1.2 Challenges with Big Data
- Storing exponentially growing huge data sets.
- Integrating disparate data sources.
- Generating insights in a timely manner.
- Data governance.
- Security issues.
1.1.3 Analytics of Big Data
1.1.3.1 Use Cases Used in Big Data Analytics
1.1.3.1.1 Amazon’s “360-Degree View”
1.1.3.1.2 Amazon – Improving User Experience
1.1.4 Social Media Analysis and Response
1.1.4.1 IoT – Preventive Maintenance and Support
1.1.4.2 Healthcare
Table of contents
- Cover
- Half-Title Page
- Series Page
- Title Page
- Copyright Page
- Table of Contents
- Preface
- List of Contributors
- Parul Gandhi
- 1 Securing Big Data Using Big Data Mining
- 2 Analytical Theory: Frequent Pattern Mining
- 3 A Journey from Big Data to Data Mining in Quality Improvement
- 4 Significance of Data Mining in the Domain of Intrusion Detection
- 5 Data Analytics and Mining: Platforms for Real-Time Applications
- 6 Analysis of Government Policies to Control Pandemic and Its Effects on Climate Change to Improve Decision Making
- 7 Data Analytics and Data Mining Strategy to Improve Quality, Performance and Decision Making
- 8 SMART Business Model: An Analytical Approach to Astute Data Mining for Successful Organization
- 9 AI and Healthcare: Praiseworthy Aspects and Shortcomings
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app