
The Psychology of Information Security
Resolving conflicts between security compliance and human behaviour
- 116 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
The Psychology of Information Security
Resolving conflicts between security compliance and human behaviour
About this book
Ensure the success of your security programme by understanding users' motivations
"This book cuts to the heart of many of the challenges in risk management, providing advice and tips from interviews as well as models that can be employed easily. Leron manages to do this without being patronising or prescriptive, making it an easy read with some very real practical takeaways."
Thom Langford, Chief Information Security Officer at Publicis Groupe
"Based on real world examples the book provides valuable insights into the relationship of information security, compliance, business economics and decision theory. Drawing on interdisciplinary studies, commentary from the field and his own research Leron gives the reader the necessary background and practical tools to drive improvements in their own information security program."
Daniel Schatz, Director for Threat & Vulnerability Management at Thomson Reuters
In today's corporations, information security professionals have a lot on their plate. In the face of constantly evolving cyber threats they must comply with numerous laws and regulations, protect their company's assets and mitigate risks to the furthest extent possible.
Security professionals can often be ignorant of the impact that implementing security policies in a vacuum can have on the end users' core business activities. These end users are, in turn, often unaware of the risk they are exposing the organisation to. They may even feel justified in finding workarounds because they believe that the organisation values productivity over security. The end result is a conflict between the security team and the rest of the business, and increased, rather than reduced, risk.
This can be addressed by factoring in an individual's perspective, knowledge and awareness, and a modern, flexible and adaptable information security approach. The aim of the security practice should be to correct employee misconceptions by understanding their motivations and working with the users rather than against them – after all, people are a company's best assets.
Product description
Based on insights gained from academic research as well as interviews with UK-based security professionals from various sectors, The Psychology of Information Security – Resolving conflicts between security compliance and human behaviour explains the importance of careful risk management and how to align a security programme with wider business objectives, providing methods and techniques to engage stakeholders and encourage buy-in.
The Psychology of Information Security redresses the balance by considering information security from both viewpoints in order to gain insight into security issues relating to human behaviour, helping security professionals understand how a security culture that puts risk into context promotes compliance.
Contents
- Chapter 1: Introduction to information security
- Chapter 2: Risk management
- Chapter 3: The complexity of risk management
- Chapter 4: Stakeholders and communication
- Chapter 5: Information security governance
- Chapter 6: Problems with policies
- Chapter 7: How security managers make decisions
- Chapter 8: How users make decisions
- Chapter 9: Security and usability
- Chapter 10: Security culture
- Chapter 11: The psychology of compliance
- Chapter 12: Conclusion - Changing the approach to security
- Appendix: Analogies
About the author
Leron Zinatullin ( zinatullin.com ) is an experienced risk consultant specialising in cyber security strategy, management and delivery. He has led large-scale, global, high-value security transformation projects with a view to improve cost performance and support business strategy.
He has extensive knowledge and practical experience in solving information security, privacy and architectural issues across multiple industry sectors.
He has an MSc in information security from University College London, where he focused on the human aspects of information security. His research was related to modelling conflicts between security compliance and human behaviour.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
CHAPTER 1: INTRODUCTION TO INFORMATION SECURITY
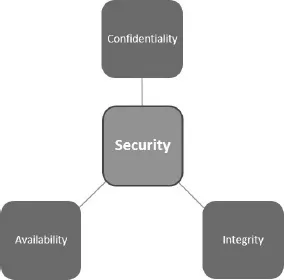
CHAPTER 2: RISK MANAGEMENT
- Opportunists: The most common type of attacker. As the category indicates, they spot and seize an ‘opportunity’ and are convinced that they will not get caught. It is easy to deter such attackers via cursory countermeasures.
- Emotional attackers: They may accept a high level of risk and usually want to make a statement through their attack. The most common motivation for them is revenge against an organisation due to actual or perceived injustice. Although emotional attackers feel powerful when causing harm, they sometimes ‘hope to get caught’ as a way of solving the issues they were unhappy with but were unable to change from the beginning.
- Cold intellectual attackers: Skilled and resourceful professionals who attack for their own gain or are employed to do so. They target information, not the system, and often use insiders to get it. Unlike opportunists, cold intellectual attackers are not discouraged by cursory countermeasures.
- Terrorists: They accept high risk to gain visibility and make a statement. Not only are they hard to deter by cursory countermeasures, but they can even see them as a thrill.
- Friends and relations: They may introduce a problem to both individuals (in the form of financial fraud, for example) and companies (by abusing authorisation credentials provided to legitimate employees). In this scenario, a victim and an attacker are sharing physical space, which makes it very easy to gain login and other sensitive information.
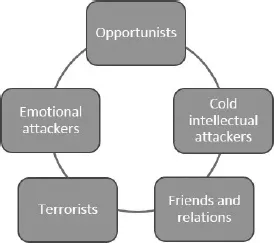
Table of contents
- Cover
- Title
- Copyright
- Foreword
- Preface
- About The Author
- Acknowledgements
- Contents
- CHAPTER 1: INTRODUCTION TO INFORMATION SECURITY
- CHAPTER 2: RISK MANAGEMENT
- CHAPTER 3: THE COMPLEXITY OF RISK MANAGEMENT
- CHAPTER 4: STAKEHOLDERS AND COMMUNICATION
- CHAPTER 5: INFORMATION SECURITY GOVERNANCE
- CHAPTER 6: PROBLEMS WITH POLICIES
- CHAPTER 7: HOW SECURITY MANAGERS MAKE DECISIONS
- CHAPTER 8: HOW USERS MAKE DECISIONS
- CHAPTER 9: SECURITY AND USABILITY
- CHAPTER 10: SECURITY CULTURE
- CHAPTER 11: THE PSYCHOLOGY OF COMPLIANCE
- CHAPTER 12: CONCLUSION - CHANGING THE APPROACH TO SECURITY
- APPENDIX: ANALOGIES
- SOURCES
- ITG RESOURCES