
Hands-On Web Penetration Testing with Metasploit
The subtle art of using Metasploit 5.0 for web application exploitation
Harpreet Singh, Himanshu Sharma
- 544 páginas
- English
- ePUB (apto para móviles)
- Disponible en iOS y Android
Hands-On Web Penetration Testing with Metasploit
The subtle art of using Metasploit 5.0 for web application exploitation
Harpreet Singh, Himanshu Sharma
Información del libro
Identify, exploit, and test web application security with ease
Key Features
- Get up to speed with Metasploit and discover how to use it for pentesting
- Understand how to exploit and protect your web environment effectively
- Learn how an exploit works and what causes vulnerabilities
Book Description
Metasploit has been a crucial security tool for many years. However, there are only a few modules that Metasploit has made available to the public for pentesting web applications. In this book, you'll explore another aspect of the framework – web applications – which is not commonly used. You'll also discover how Metasploit, when used with its inbuilt GUI, simplifies web application penetration testing.
The book starts by focusing on the Metasploit setup, along with covering the life cycle of the penetration testing process. Then, you will explore Metasploit terminology and the web GUI, which is available in the Metasploit Community Edition. Next, the book will take you through pentesting popular content management systems such as Drupal, WordPress, and Joomla, which will also include studying the latest CVEs and understanding the root cause of vulnerability in detail. Later, you'll gain insights into the vulnerability assessment and exploitation of technological platforms such as JBoss, Jenkins, and Tomcat. Finally, you'll learn how to fuzz web applications to find logical security vulnerabilities using third-party tools.
By the end of this book, you'll have a solid understanding of how to exploit and validate vulnerabilities by working with various tools and techniques.
What you will learn
- Get up to speed with setting up and installing the Metasploit framework
- Gain first-hand experience of the Metasploit web interface
- Use Metasploit for web-application reconnaissance
- Understand how to pentest various content management systems
- Pentest platforms such as JBoss, Tomcat, and Jenkins
- Become well-versed with fuzzing web applications
- Write and automate penetration testing reports
Who this book is for
This book is for web security analysts, bug bounty hunters, security professionals, or any stakeholder in the security sector who wants to delve into web application security testing. Professionals who are not experts with command line tools or Kali Linux and prefer Metasploit's graphical user interface (GUI) will also find this book useful. No experience with Metasploit is required, but basic knowledge of Linux and web application pentesting will be helpful.
Preguntas frecuentes
Información
Penetration Testing on Technological Platforms - JBoss
- An introduction to JBoss
- Performing reconnaissance on a JBoss - based application server using Metasploit
- Vulnerability assessments on JBoss
- Carrying out JBoss exploitation with the help of Metasploit modules
Technical requirements
- A JBoss Application Server (AS) instance (https://jbossas.jboss.org/)
- The Metasploit Framework (https://www.metasploit.com/)
- JexBoss, which is a third-party tool (https://github.com/joaomatosf/jexboss)
An introduction to JBoss
- Flexibility due to plugin-based architecture
- Ease of installation and setup
- Provides the full Java EE stack, including Enterprise JavaBeans (EJB), Java Messaging Service (JMS), Java Management Extension (JMX), and Java Naming and Directory Interface (JNDI)
- Can run an Enterprise Application (EA)
- Is cost-efficient
The JBoss architecture (JBoss 5)
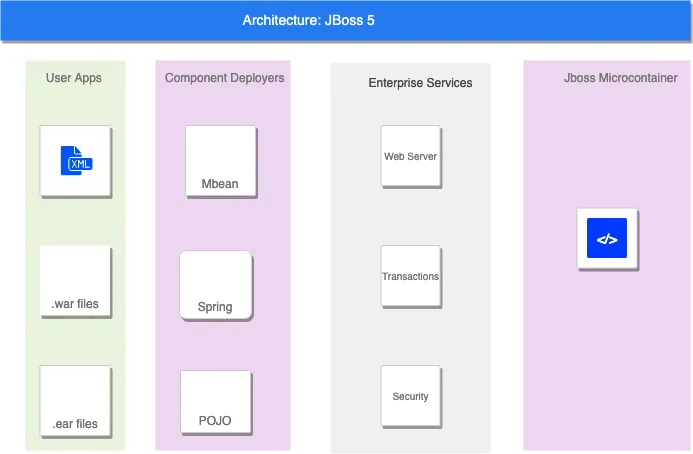
- User applications: As the name suggests, this component handles user applications and contains the XML config files, Web Application Resource (WAR) files, and so on. This is where user applications are deployed.
- Component deployers: Deployers are used in JBoss to deploy components. MainDeployer, JARDeployer, and SARDeployer are hardcoded deployers in the JBoss server core. All other deployers are Managed Bean (MBean) services that register themselves as deployers with MainDeployer.
- Enterprise services: This component is responsible for handling multiple things, such as transactions, security, and the web server.
- The JBoss microcontainer: This can be used as a standalone container outside of JBoss AS. It is designed to provide an environment to configure and manage Plain Old Java Objects (POJOs).