DATA-DRIVEN SECURITY
What cannot be measured cannot be managed. This is a commonly accepted business paradigm, yet its acceptance within the security industry is not as far reaching as in other industries. Simply put, data-driven security refers to using measurable factors to drive a security program. While not all elements of a security program lend themselves to measurement, many components can be measured effectively. For example, physical protection systems are measured via penetration times, and barriers are measured using delay and defeat times. Other security components can be measured, though not mathematically, including the morale of protection forces.
Some would argue that the security is more of an art than a science. While they are correct, the business of security is not an art. The security department is a business unit, not unlike other business units within a company that must justify their existence. The higher security moves up the corporate ladder, the more challenges the security director will face and the more business acumen will be required. Given the security industry’s growth out of public law enforcement, it is no surprise that it has taken the industry significant time to develop into a full-fledged corporate entity. With this growth comes the need to depart from the police mentality. Thirty years ago, most security directors were retired law enforcement agents who made the jump to private security as a way to supplement their retirement income. This has proven to slow the growth of security within the corporate hierarchy, but was probably a necessary step in the history of the industry. This is not to say that retired law enforcement personnel do not have a place in the security industry. To the contrary, many have proven to be exemplary business leaders who have made significant leaps for the security departments in their companies.
As the security industry grows to not only include physical security but also information/cyber security, it is incumbent upon today’s security directors to focus more on the business side of security rather than the operational side. This is best summarized by the world’s leading security association, ASIS – International, in their Chief Security Officer Guideline:
Today’s business risk environments have become increasingly more severe, complex, and interdependent, both domestically and globally. The effective management of these environments is a fundamental requirement of business. Boards of Directors, shareholders, key stakeholders, and the public correctly expect organizations to identify and anticipate areas of risk and set in place a cohesive strategy across all functions to mitigate or reduce those risks. In addition, there is an expectation that management will respond in a highly effective manner to those events and incidents that threaten the assets of the organization. A proactive strategy for mitigation of the risk of loss ultimately provides a positive impact to profitability and is an organizational governance responsibility of senior management and governing boards.
The guideline goes on to discuss the role of the Chief Security Officer (CSO) as a business leader, a problem solver, as well as an expert in security for their company. Interestingly, the guideline also suggests that the CSO’s background includes business, not law enforcement, since their key responsibility “is to develop and implement a strategy that demonstrates the processes in understanding the nature and probability of catastrophic and significant security risk events.” As the company security departments grow and begin to encompass more responsibility for the protection of people, property, and information, so too must the ability to fall back on empirical data to support our position. No longer can security professionals rely solely on gut instincts.
Too often recommendations from the security department are presented with little or no thought to why certain procedures or security equipment should be used. Often, the reason for deploying a security measure is because other companies are doing it (benchmarking). It is all too common in the security industry for there to be a propensity for using certain security measures without complete understanding of the problem or a thorough analysis of the security measures’ ability to be effective given the specific situation. Data-driven security can help security directors overcome this problem by identifying key concerns, the ability for specific security measures to solve the problem, and the anticipated cost.
How can security professionals justify to senior executives a sizable and usually growing annual security budget? By now, most security directors are keenly aware that a security program’s success depends on the commitment and support of senior executives. Using anecdotal evidence to justify spending on physical security measures and costly protection personnel no longer suffices. A data-driven security program helps management understand that security is more than a must-have expense; it justifies costs to management by showing the proof of success that, when presented effectively, can garner the necessary buy-in from upper management and demonstrate a convincing return on investment. Security expenditures, just like other departmental budgets, need to be justified with empirical data and supplemented with cost-benefit analyses and comparisons.
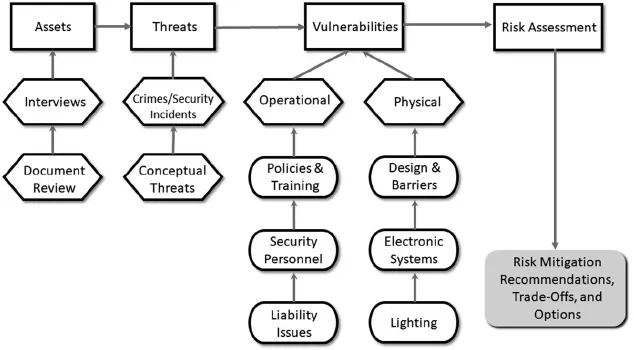
Throughout the first part of this book, various assessments used in the security industry are discussed, including threat, vulnerability, and risk assessments along with specific types of assessments like crime analysis. Common to each of these is a quantitative approach to establish a baseline from which security effectiveness can be measured. Assessments are the foundation upon which a security program is built by establishing a baseline of risks that companies face. Assessments guide the strategic planning and design of countermeasures intended to mitigate the identified security risks.
Such a logical approach brings benefits which are unattainable with only qualitative assessments which are still used throughout the public and private security sectors. While qualitative assessments cannot be abandoned, their use should be limited to those instances where quantitative ones cannot be used for lack of measurable elements. Thus, physical security is, and shall remain, more of an art than a science, though science can be infused into an otherwise abstract process.
I don’t care how skilled you are as a diplomat or how brilliant you are at leading, if you are not professional about security, you are a failure.
Former U.S. Secretary of State Madeline Albright
SECURITY METRICS
Between September 2001 and the writing of the first edition of this book in April 2006, the United States suffered no major terrorist attacks. While this fact made for a great sound bite for political talking heads, it is not an accurate metric of the true threat faced by the United States as has been proven in the intervening years where we experienced numerous terrorist acts, primarily active shootings by lone wolves. A more appropriate metric would be the number of attacks thwarted since September 2001 or arrests made of known terrorists. When providing asset protection, accurate measurement of security effectiveness can have a profound impact on management’s level of support for the security department. “Near misses” are sometimes evidence of our success in mitigating risks.
As mentioned earlier, a common paradigm in business is that an activity cannot be managed if it cannot be measured. Security is one such activity. Security metrics communicate vital information about security activities and drive decision making. Metrics for various security components, such as the protection force or access control system, can be an effective tool for security professionals to understand the effectiveness of the overall security program. Metrics, as previously discussed, may also identify risk based on failures or successes of security components, and can provide solutions to security problems. Security metrics focus on the results of security decisions such as reduction in thefts after implementation of a video surveillance system, an increase in visibility or customer service ratings after a change in security officer uniforms, or a reduction in terrorist acts as a result of terrorist cell arrests.
Security metrics help define how secure and effective we are. They assist security professionals in answering basic questions posed by management, such as:
- Are company assets protected?
- Which assets need more protection?
- Can the asset protection program be improved?
- What resources should be allocated to security?
- How does our company compare to others?
- Are we reducing our liability exposure?
The National Institute of Standards and Technology (N.I.S.T.) defines metrics as tools designed to facilitate decision making and improve performance and accountability through collection, analysis, and reporting of relevant performance-related data. Thus, security metrics assist security professionals in making asset protection decisions through the measurement of performance-based characteristics of security components. Simply stated, security metrics are tools used for measuring a company’s security posture.
For the security metrics to be accurate, security professionals must have two elements in the metrics model:
- proper performance data for the specific countermeasure under evaluation; and
- an appropriate baseline from which to compare.
Baseline measurements are often difficult to obtain, especially in the business of security where companies are, out of necessity, secretive about their protection systems. In recent years, industry associations such as ASIS-International, the International Association for Professional Security Consultants, and the International Association for Healthcare Security and Safety have promulgated standards, guidelines, and best practices. Even non-security associations, such as the National Fire Protection Association, have written security guidelines. In addition to published and accepted industry standards, the courts have outlined baselines of measurement for the security industry. An example of this is a Texas Supreme Court case, Timberwalk v. Cain, which outlines the specific factors necessary for establishing foreseeability of crime in premises liability lawsuits. In Timberwalk, the court set forth five criteria for measuring the risk of crime including recency, proximity, publicity, frequency, and similarity of past crimes. An example of crime metrics legislation is the 1996 Illinois Automated Teller Machine Act. Section 20 of the Act provides procedures for evaluating the safety of ATM’s regarding “the incidence of crimes of violence in the immediate neighborhood of the ATM.” Texas has a similar ATM Safety law which requires that financial institutions collect crime metrics. Some states have also required collection and reporting of workplace violence metrics in some areas such as healthcare. Thus, the professional security practitioner will stay abreast of industry standards and the law. While laws must normally be reasonably followed, security professionals may fine-tune published industry standards to meet the needs of their company.
In addition to establishing a baseline for comparing company metrics, metrics are also used to justify budgets, provide data for decision making, and improving security practices. Metrics can be used to justify budgets and provide the basis for obtaining additional resources for the security department. Security metrics may be plugged into cost-benefit analyses to identify the need for various security components. For security decision making, metrics can unveil trends and patterns in the security program’s performance from which security decision makers can make decisions to modify the program. For example, once a physical protection system is alerted of an intruder, security force personnel may respond. By measuring time needed to respond from the security officer’s fixed post to the breached access point, the security decision maker can determine if the response time is adequate or if another post needs to be established closer to the access point. Finally, metrics assist in the development of good security practices. An example of this may be found in the use of security personnel to provide escorts for company personnel exiting the building to the parking areas. While this is a common practice in some companies, an analysis of security incidents during peak times may indicate a sharp increase in security breaches because security personnel are distracted from their primary protection duties while escorting personnel. In this instance, the value of providing escorts must be balanced with other duties when determining the company’s security practices.