
CompTIA Security+ Study Guide
Exam SY0-601
Mike Chapple, David Seidl
- English
- ePUB (apto para móviles)
- Disponible en iOS y Android
CompTIA Security+ Study Guide
Exam SY0-601
Mike Chapple, David Seidl
Información del libro
Learn the key objectives and most crucial concepts covered by the Security+ Exam SY0-601 with this comprehensive and practical study guide! An online test bank offers 650 practice questions and flashcards!
The Eighth Edition of the CompTIA Security+ Study Guide Exam SY0-601 efficiently and comprehensively prepares you for the SY0-601 Exam. Accomplished authors and security experts Mike Chapple and David Seidl walk you through the fundamentals of crucial security topics, including the five domains covered by the SY0-601 Exam:
- Attacks, Threats, and Vulnerabilities
- Architecture and Design
- Implementation
- Operations and Incident Response
- Governance, Risk, and Compliance
The study guide comes with the Sybex online, interactive learning environment offering 650 practice questions! Includes a pre-assessment test, hundreds of review questions, practice exams, flashcards, and a glossary of key terms, all supported by Wiley's support agents who are available 24x7 via email or live chat to assist with access and login questions.
The book is written in a practical and straightforward manner, ensuring you can easily learn and retain the material. Perfect for everyone planning to take the SY0-601 Exam—as well as those who hope to secure a high-level certification like the CASP+, CISSP, or CISA—the study guide also belongs on the bookshelves of everyone who has ever wondered if the field of IT security is right for them. It's a must-have reference!
Preguntas frecuentes
Información
Chapter 1
Today's Security Professional
- Domain 1.0: Threats, Attacks, and Vulnerabilities
- 1.6. Explain the security concerns associated with various types of vulnerabilities.
- Domain 2.0: Architecture and Design
- 2.1. Explain the importance of security concepts in an enterprise environment.
- Domain 5.0: Governance, Risk, and Compliance
- 5.1. Compare and contrast various types of controls.
Cybersecurity Objectives
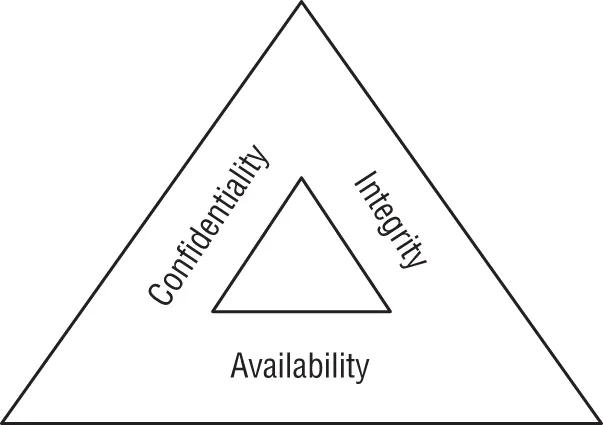
Data Breach Risks
The DAD Triad
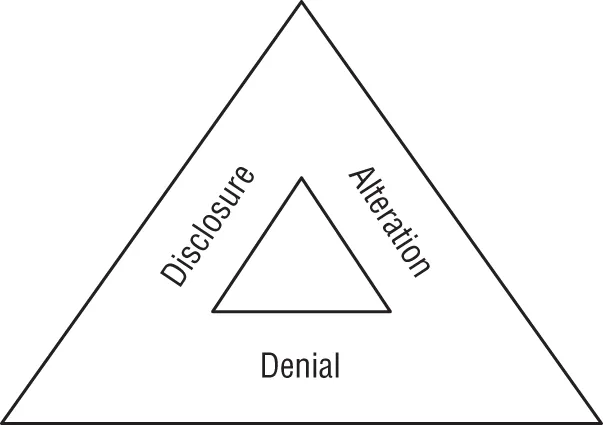
- Disclosure is the exposure of sensitive information to unauthorized individuals, otherwise known as data loss. Disclosure is a violation of the principle of confidentiality. Attackers who gain access to sensitive information and remove it from the organization are said to be performing data exfiltration. Disclosure may also occur accidentally, such as when an administrator misconfigures access controls or an employee loses a device.
- Alteration is the unauthorized modification of information and is a violation of the principle of integrity. Attackers may seek to modify records contained in a system for financial gain, such as adding fraudulent transactions to a financial account. Alteration may occur as the result of natural activity, such as a power surge causing a “bit flip” that modifies stored data. Accidental alteration is also a possibility, if users unintentionally modify information stored in a critical system as the result of a typo or other unintended activity.
- Denial is the disruption of an authorized user's legitimate access to information. Denial events violate the principle of availability. This availability loss may be intentional, such as when an attacker launches a distributed denial-of-service (DDoS) attack against a website. Denial may also occur as the result of accidental activity, such as...