Java EE 8 Design Patterns and Best Practices
Build enterprise-ready scalable applications with architectural design patterns
Rhuan Rocha, João Purificação
- 314 páginas
- English
- ePUB (apto para móviles)
- Disponible en iOS y Android
Java EE 8 Design Patterns and Best Practices
Build enterprise-ready scalable applications with architectural design patterns
Rhuan Rocha, João Purificação
Información del libro
Get the deep insights you need to master efficient architectural design considerations and solve common design problems in your enterprise applications.
Key Features
- The benefits and applicability of using different design patterns in JAVA EE
- Learn best practices to solve common design and architectural challenges
- Choose the right patterns to improve the efficiency of your programs
Book Description
Patterns are essential design tools for Java developers. Java EE Design Patterns and Best Practices helps developers attain better code quality and progress to higher levels of architectural creativity by examining the purpose of each available pattern and demonstrating its implementation with various code examples. This book will take you through a number of patterns and their Java EE-specific implementations.
In the beginning, you will learn the foundation for, and importance of, design patterns in Java EE, and then will move on to implement various patterns on the presentation tier, business tier, and integration tier. Further, you will explore the patterns involved in Aspect-Oriented Programming (AOP) and take a closer look at reactive patterns. Moving on, you will be introduced to modern architectural patterns involved in composing microservices and cloud-native applications. You will get acquainted with security patterns and operational patterns involved in scaling and monitoring, along with some patterns involved in deployment.
By the end of the book, you will be able to efficiently address common problems faced when developing applications and will be comfortable working on scalable and maintainable projects of any size.
What you will learn
- Implement presentation layers, such as the front controller pattern
- Understand the business tier and implement the business delegate pattern
- Master the implementation of AOP
- Get involved with asynchronous EJB methods and REST services
- Involve key patterns in the adoption of microservices architecture
- Manage performance and scalability for enterprise-level applications
Who this book is for
Java developers who are comfortable with programming in Java and now want to learn how to implement design patterns to create robust, reusable and easily maintainable apps.
Preguntas frecuentes
Información
Security Patterns
- Explaining the concept of security patterns
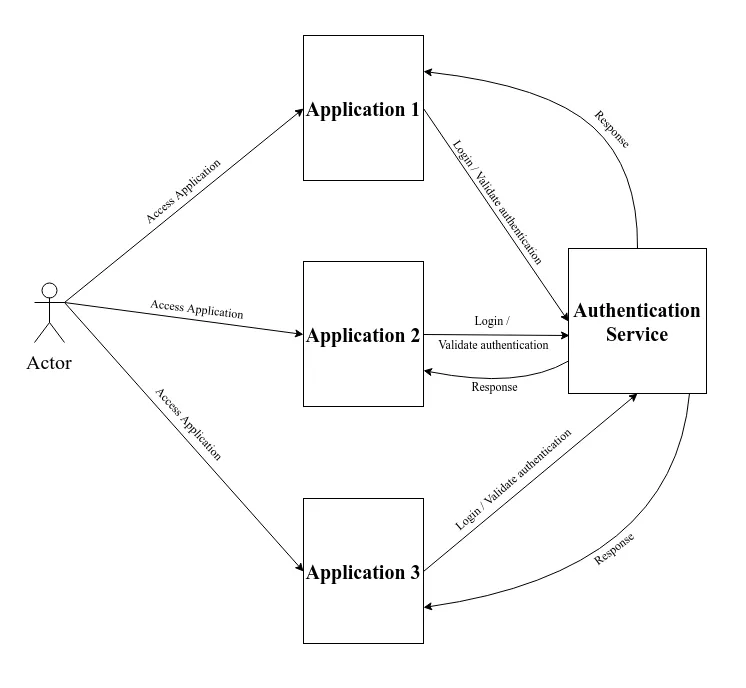
- Explaining the concept of the single-sign-on pattern
- Implementing the single-sign-on pattern
- Explaining the authentication mechanism
- Implementing the authentication mechanism
- Explaining the authentication interceptor
- Implementing the authentication interceptor
Explaining the concept of security patterns
- Confidentiality: The data should not be accessible to non-authorized users or to any entities that request access to the data.
- Integrity: The data cannot be updated or modified in a non-authorized manner.
- Availability: The data should be available when it is needed.
- Non-repudiation: Users cannot repudiate or deny the relation using data or any other process.
Explaining the concept of the single-sign-on pattern