
Practical Mobile Forensics,
Heather Mahalik, Satish Bommisetty, Oleg Skulkin, Rohit Tamma, Igor Mikhaylov
- 402 pagine
- English
- ePUB (disponibile sull'app)
- Disponibile su iOS e Android
Practical Mobile Forensics,
Heather Mahalik, Satish Bommisetty, Oleg Skulkin, Rohit Tamma, Igor Mikhaylov
Informazioni sul libro
Investigate, analyze, and report iOS, Android, and Windows devices
Key Features
- Get hands-on experience in performing simple to complex mobile forensics techniques.
- Retrieve and analyze data stored not only on mobile devices but also through the cloud and other connected mediums.
- A practical guide to leveraging the power of mobile forensics on popular mobile platforms with lots of tips, tricks, and caveats.
Book Description
Covering up-to-date mobile platforms, this book will focuses on teaching you the most recent techniques for investigating mobile devices. We delve mobile forensics techniques in iOS 9-11, Android 7-8 devices, and Windows 10. We will demonstrate the latest open source and commercial mobile forensics tools, enabling you to analyze and retrieve data effectively. You will learn how to introspect and retrieve data from the cloud, and document and prepare reports of your investigations.
By the end of this book, you will have mastered the current operating systems and the relevant techniques to recover data from mobile devices by leveraging open source solutions.
What you will learn
- Discover the new techniques in practical mobile forensics
- Understand the architecture and security mechanisms present in iOS and Android platforms
- Identify sensitive files on the iOS and Android platforms
- Set up a forensic environment
- Extract data from the iOS and Android platforms
- Recover data on the iOS and Android platforms
- Understand the forensics of Windows devices
- Explore various third-party application techniques and data recovery techniques
Who this book is for
If you are a forensics professional and are eager to widen your forensics skill set to mobile forensics then, this book is for you. Some understanding of digital forensics practices would do wonders.
Domande frequenti
Informazioni
Android Forensic Setup and Pre-Data Extraction Techniques
- Setting up a forensic environment
- Connecting the device and accessing it from a workstation
- Screen lock bypass techniques
- Gaining root access to the device
Setting up the forensic environment for Android
- Start with a fresh or forensically sterile computer environment. This means that other data is either not present on the system or is contained in a manner that prevents it from contaminating the present investigation.
- Install the basic software necessary to connect to the device. Android forensic tools and methodologies will work on Windows, Linux, and OS X platforms.
- Obtain access to the device. An examiner must be able to enable settings or bypass them in order to allow the data to be extracted from the Android device.
- Issue commands to the device through the methods defined in this chapter and in Chapter 9, Android Data Extraction Techniques.
The Android Software Development Kit
The Android SDK installation
- Before you install the Android SDK, make sure that your system has Java Development Kit installed, because the Android SDK relies on Java SE Development Kit (JDK).
- Download the latest version of the Android SDK from: https://developer.android.com/studio/index.html. The installer version of the SDK is recommended for this purpose.
- Run the installer file, which we downloaded in the previous step. You will see a wizard window, as seen in the following screenshot. After this, run through the routine Next steps that you encounter:

- The installation location is the user's choice and must be remembered for future access. In this example, we will install it in the C:\ folder. Click on the Install button and choose the location (say, C:\android-sdk). The necessary files will be extracted to this folder.
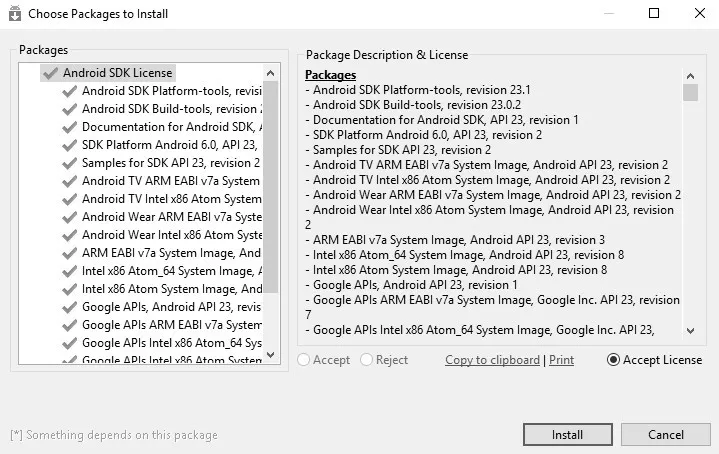
- Open the directory (C:\android-sdk) and double-click on SDK Manager.exe to begin the update process. Make sure that you select Android SDK Platform tools and any one release platform version of Android, as shown in the following screenshot. Some of the items in the list are chosen by default. For instance, it is necessary to install the USB driver in order to work with Android devices in Windows. In our example, Google USB Driver is selected. Similarly, you can find other items under the Extras section. Accept the license and click on Install, as shown in the following screenshot:
An Android Virtual Device
- Open the command prompt (cmd.exe). Start the AVD manager from the command line by navigating to the path where the SDK is installed and call the Android tool with the avd option, as shown in the following command line. This will automatically open the AVD manager:
C:\android-sdk\tools>android avd