
Metasploit Penetration Testing Cookbook
Abhinav Singh, Nipun Jaswal, Monika Agarwal, Daniel Teixeira
- English
- ePUB (disponibile sull'app)
- Disponibile su iOS e Android
Metasploit Penetration Testing Cookbook
Abhinav Singh, Nipun Jaswal, Monika Agarwal, Daniel Teixeira
Informazioni sul libro
Over 100 recipes for penetration testing using Metasploit and virtual machines
Key Features
- Special focus on the latest operating systems, exploits, and penetration testing techniques
- Learn new anti-virus evasion techniques and use Metasploit to evade countermeasures
- Automate post exploitation with AutoRunScript
- Exploit Android devices, record audio and video, send and read SMS, read call logs, and much more
- Build and analyze Metasploit modules in Ruby
- Integrate Metasploit with other penetration testing tools
Book Description
Metasploit is the world's leading penetration testing tool and helps security and IT professionals find, exploit, and validate vulnerabilities. Metasploit allows penetration testing automation, password auditing, web application scanning, social engineering, post exploitation, evidence collection, and reporting. Metasploit's integration with InsightVM (or Nexpose), Nessus, OpenVas, and other vulnerability scanners provides a validation solution that simplifies vulnerability prioritization and remediation reporting. Teams can collaborate in Metasploit and present their findings in consolidated reports.
In this book, you will go through great recipes that will allow you to start using Metasploit effectively. With an ever increasing level of complexity, and covering everything from the fundamentals to more advanced features in Metasploit, this book is not just for beginners but also for professionals keen to master this awesome tool.
You will begin by building your lab environment, setting up Metasploit, and learning how to perform intelligence gathering, threat modeling, vulnerability analysis, exploitation, and post exploitation—all inside Metasploit. You will learn how to create and customize payloads to evade anti-virus software and bypass an organization's defenses, exploit server vulnerabilities, attack client systems, compromise mobile phones, automate post exploitation, install backdoors, run keyloggers, highjack webcams, port public exploits to the framework, create your own modules, and much more.
What you will learn
- Set up a complete penetration testing environment using Metasploit and virtual machines
- Master the world's leading penetration testing tool and use it in professional penetration testing
- Make the most of Metasploit with PostgreSQL, importing scan results, using workspaces, hosts, loot, notes, services, vulnerabilities, and exploit results
- Use Metasploit with the Penetration Testing Execution Standard methodology
- Use MSFvenom efficiently to generate payloads and backdoor files, and create shellcode
- Leverage Metasploit's advanced options, upgrade sessions, use proxies, use Meterpreter sleep control, and change timeouts to be stealthy
Who this book is for
If you are a Security professional or pentester and want to get into vulnerability exploitation and make the most of the Metasploit framework, then this book is for you. Some prior understanding of penetration testing and Metasploit is required.
Domande frequenti
Informazioni
Meterpreter
- Understanding the Meterpreter core commands
- Understanding the Meterpreter filesystem commands
- Understanding the Meterpreter networking commands
- Understanding the Meterpreter system commands
- Setting up multiple communication channels with the target
- Meterpreter anti-forensics
- The getdesktop and keystroke sniffing
- Using a scraper Meterpreter script
- Scraping the system with winenum
- Automation with AutoRunScript
- Meterpreter resource scripts
- Meterpreter timeout control
- Meterpreter sleep control
- Meterpreter transports
- Interacting with the registry
- Load framework plugins
- Meterpreter API and mixins
- Railgun—converting Ruby into a weapon
- Adding DLL and function definitions to Railgun
- Injecting the VNC server remotely
- Enabling Remote Desktop
Introduction
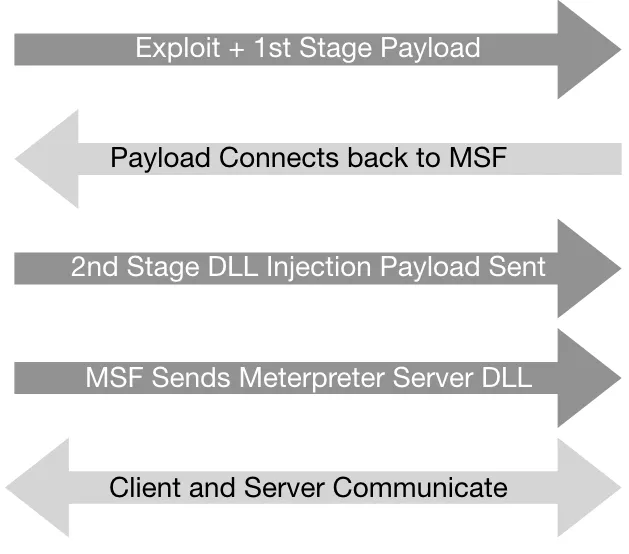
- It works in context with the exploited process, so it doesn't create a new process
- It can migrate easily among processes
- It resides completely in memory, so it writes nothing to disk
- It uses encrypted communications
- It uses a channelized communication system so that we can work with several channels at a time
- It provides a platform to write extensions quickly and easily
Understanding the Meterpreter core commands
Getting ready
How to do it...
- The Metasploit Framework comes packed with several resource scripts that have been contributed to by the community, which you can find at /usr/share/metasploit-framework/scripts/resource/ in your Kali Linux machine:
root@kali:~# ls /usr/share/metasploit-framework/scripts/resource/
auto_brute.rc fileformat_generator.rc
auto_cred_checker.rc mssql_brute.rc
auto_pass_the_hash.rc multi_post.rc
auto_win32_multihandler.rc nessus_vulns_cleaner.rc
autocrawler.rc oracle_login.rc
autoexploit.rc oracle_sids.rc
bap_all.rc oracle_tns.rc
bap_dryrun_only.rc port_cleaner.rc
bap_firefox_only.rc portscan.rc
bap_flash_only.rc run_all_post.rc
bap_ie_only.rc wmap_autotest.rc
basic_discovery.rc
- ...