
eBook - ePub
WiFi, WiMAX, and LTE Multi-hop Mesh Networks
Basic Communication Protocols and Application Areas
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
WiFi, WiMAX, and LTE Multi-hop Mesh Networks
Basic Communication Protocols and Application Areas
About this book
Wifi, WiMAX, and Cellular Multihop Network s presents an overview of WiFi-based and WiMAX-based multihop relay networks. As the first text to cover IEEE 802.16j multihop hop relay technology, this revolutionary resource explores the latest advances in multi-hop and ad-hoc networking. Not only does this reference provide the technological aspects, but also the applications for the emerging technology and architectural issues. Ranging from introductory material to advanced topics, this guidebook is essential for engineers, researchers, and students interested in learning more about WiFi and WiMAX multihop relay networks.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access WiFi, WiMAX, and LTE Multi-hop Mesh Networks by Hung-Yu Wei,Jarogniew Rykowski,Sudhir Dixit in PDF and/or ePUB format, as well as other popular books in Tecnologia e ingegneria & Ingegneria elettronica e telecomunicazioni. We have over one million books available in our catalogue for you to explore.
Information
1
Introduction
Nowadays, a global trend is to make our lives easier. To reach this goal, we freely apply new technologies to develop personal, organizational, and social solutions. We even create new technology domains and their applications, such as cellular telephony or Internet. And it looks like that this trend is only going to accelerate, as new technologies lead to new multidisciplinary innovations with a multiplier effect. The rapid change is akin to what Arthur C. Clarke described as “magic”—any sufficiently advanced technology is indistinguishable from magic (Clarke, 1962). And humans, for the most part, have begun to believe in that magic such that with technology and innovation almost everything is possible.
With the mass introduction of, first, the Internet, and, now, cellular telephony, a new need has arisen to be able to communicate with everybody (or everything), at anytime, from anywhere, including access to the Web. “Magical” mobile communication has been accepted as a norm around the world, and this nomadic lifestyle has prompted a serious look at the business and personal environment. However, the “magic” is unfortunately constrained by several technical and economic obstacles. Even if we do believe that unrestricted communication is a must, we are still faced with many challenges, for example, poor signal quality and range, and high calling costs. Satellite phones would probably work better to provide universal coverage (e.g., in rural and mountainous regions), but the cost will be prohibitively high. Similarly, a bigger battery would substantially reduce the need for frequent recharging, but it is going to severely impact portability.
As we become aware of our continuously expanding needs and expectations, we naturally tend to ignore the limitations. In general, two ways are possible: either we simply wait for an introduction of a new technical/organizational/social solution, new infrastructure, device, and so on, or we try to adapt the existing solutions for new challenges, even if this is a temporary solution; alternatively, we apply a mixed approach—first we try to accomplish the best from the existing solutions, and later search for a new solution to better fulfill our needs.
This book is devoted to applying such mixed approaches to mobile communication and internet access with the main objective to significantly improve coverage and minimize cost. Recently, wireless computer networks, such as WiFi and WiMAX, on the one hand, and mobile communication, such as general packet radio service/enhanced data rate for global evolution (GPRS/EDGE), high speed packet access (HSPA), and Long Term Evolution (LTE), on the other hand, have opened up new possibilities to meet the objectives. However, to build such a network, significant investment in the infrastructure is required, not to mention of the physical restrictions (such as the ability of the radio signals to penetrate through physical structures). From the organizational point of view, the connected equipment (mobile stations) must authorize itself prior to accessing the network, and there is a serious issue of potential denial of service attack between a “server” (i.e., network element serving the client devices) and a “client.” The advent of ad-hoc and multi-hop networking has only compounded the problem.
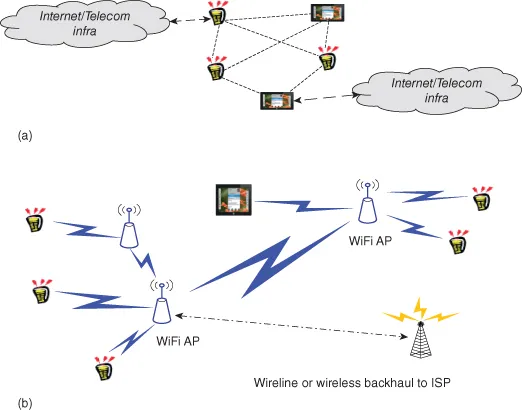
A mobile ad-hoc network (MANET for short) is defined as a self-organized set of wireless, mobile nodes with no fixed topology of connections. In general, wireless mesh network can be of two types (Fig. 1.1): MANET and infrastructure-based immobile network. MANETs are typically peer-to-peer networks with mobile client devices communicating with each other directly or through other nodes in multi-hop configuration (Fig. 1.1a). Here client nodes may function as routing nodes for others that are not within each other’s communication range. In immobile wireless mesh network, the access radio nodes and gateway nodes are stationary, and the client devices connect to the access node (Fig. 1.1b). MANET organization may vary in time—nodes are being connected and disconnected, they replace their point of connection (their neighborhood evolves), and dynamically adapt themselves to the topology changes. As a matter of fact, nothing is fixed; in contrast to classical networking, a MANET node may disappear at anytime, causing serious disruptions to the neighboring nodes. Furthermore, routing of the information must be planned in a dynamic manner so as to be able to deal with the evolving network topology (the route for the outgoing packet and the incoming packet between a pair of nodes may be different, as the topology may change even during the period of a single transmission).
Figure 1.1. Examples of (a) mobile ad-hoc (infrastructureless) mesh network and (b) immobile (infrastructure-based) mesh network.
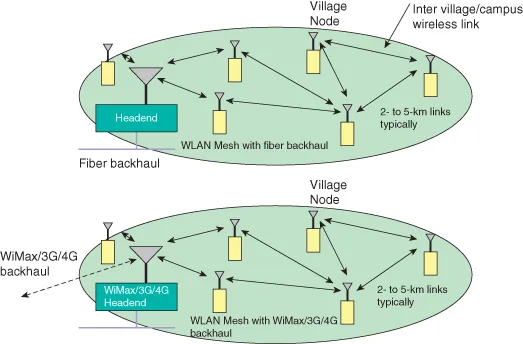
When we speak about MANETs, we think about mesh networking. A wireless* mesh network can be in general configured as a hierarchical network made up of home area network (HAN), Neighborhood Area Network (NAN), and wide area network (WAN), each utilizing the most suitable wireless technologies for their needs. For HAN, IEEE 802.11- and IEEE 802.15.4-based ZigBee (ZigBee Alliance, 2012) are thought of as most suitable. In the majority of cases, a single access point (AP) or ZigBee host is sufficient in the home scenario. If the source and destination nodes do not reside within the same NAN, the traffic from the various HANs is routed to one or more gateway nodes that backhaul the traffic utilizing high speed mobile data technologies, such as 3G, HSPA/HSPA+, LTE, LTE-A, or WiMax (3GPP Specifications, 2012; IEEE Wireless MAN [WiMax], 2012; WiMax Forum, 2012). The preferred solution to cover a wide area (resulting in a NAN), such as a neighborhood, a campus, or a city is to use IEEE 802.11x WLAN (aka WiFi) in mesh configuration. Figure 1.2 shows a generic wireless mesh network depicting the various scenarios. Figure 1.3 shows the use of lower frequency white spaces between the TV channels (which is at much lower frequencies than 2.4 GHz) in the ultra-high frequency (UHF) band (470–890 MHz) to create longer distance Internet connections that easily penetrate through the physical obstructions. These are still unlicensed and therefore their use is free and similar to WiFi and Bluetooth. This type of networking technology is called “Super WiFi” by the Federal Communications Commission (FCC) (Regulators, 2012; Segan, 2012). It should be noted that there is no similarity with the WiFi technology, and the use of “Super WiFi” is confusing and controversial with the Wi-Fi Alliance (WiFi, 2012; US regulators, 2012).
Figure 1.2. Use of long range WLAN (Super WiFi) mesh to extend coverage to larger areas.
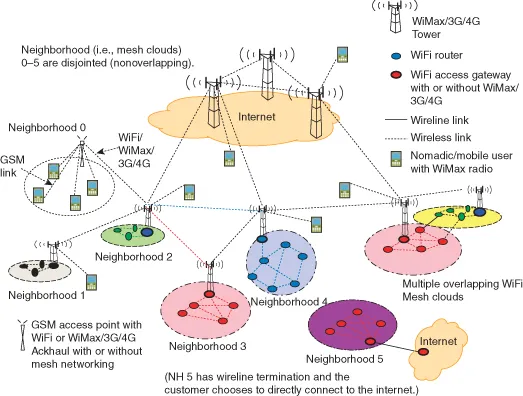
Figure 1.3. Use of long range WLAN (Super WiFi) mesh to extend coverage to larger areas.
Traditionally, wireless network design is based on the centralized architecture where the base stations control the operation of the wireless services delivered to subscriber stations. In the conventional wireless cellular architecture, a base station is the centralized controller of each cell, as shown in Figure 1.4a. The base station transmits and receives data packets and signaling messages to and from subscriber stations through a one-hop direct wireless link. On the other hand, a multi-hop relay wireless paradigm has emerged in recent years. In multi-hop wireless relay networks, wireless nodes may transmit and forward packets through one or several wireless relay hops, as shown in Figure 1.4b. In this multi-hop relay network configuration, a distributed design approach may be applied to enable multi-hop relay signaling and data transport. A third wireless network paradigm integrates the previous two approaches as shown in Figure 1.4c. Both direct one-hop wireless connections and multi-hop wireless relays are present in this hybrid architecture. This hybrid wireless network architecture leverages the benefits of both the conventional cellular architecture and the multi-hop relay architecture to provide efficient centralized wireless network control and flexibility of multi-hop relaying.
Figure 1.4. Networking paradigms: (a) conventional wireless cellular network, (b) multi-hop wireless relay network, and (c) hybrid wireless network integrating cellular structure and multi-hop relay.
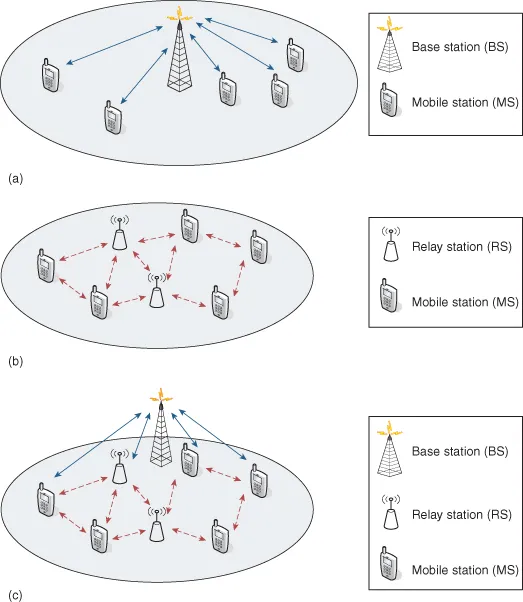
As the hybrid architecture could take advantages of both the conventional centralized cellular architecture and the emerging relay architecture, there are several design benefits that could be exploited. Some of the key advantages of this hybrid wireless multi-hop relay architecture are as follows:
- leveraged benefits of cellular architecture and multi-hop relay architecture
- extended wireless network coverage at cell boundary
- enhanced signal reception quality and throughput
- improved load balancing
- flexible deployment with fixed or mobile relay stations.
A still-growing trend is to spend large sums of money on the development of ad-hoc and multi-hop technologies. However, it is worth noting that these ideas are not quite new. The very first research on these topics was undertaken in the late 1960s. Then, ALOHA protocol was proposed to control the access to telecommunication channels. Although it considered only stationary nodes, communicating in a single-hop mode, it was the first step toward spontaneous and unrestricted networking. In 1973, DARPA initiated the PRnet (Packet Radio Network) project based on multi-hop transmission. This proposal clearly showed that using multi-hops may substantially extend the network range, improve efficiency (especially by division and parallel transmission of signal parts), and reduce energy consumption. Nowadays, MANETs are capable of multi-hop information routing even when the network topology and traffic are dynamically changing, while employing narrow and temporal channels. Several companies now offer global solutions, prime examples being Intel, CISCO, Mitsubishi, BMW, Nokia, and Deutsche Telecom. Despite technical, organizational, societal, and legislative issues (some of them discussed in this book), the global trend is clear. Using ordinary nodes as routers substantially improves network range and efficiency. Each device already connected to the network may in turn become an access point for other devices, even those not operating directly in mesh topology. The replacement of “one-to-many” access mode by “many-to-many” opens up new connection and transmission possibilities. Local instead of long-distance communication reduces network traffic and improves coding and noise/error reduction while also eliminating interference among devices and improving radio bandwidth sharing. Local communication also protects the environment—less power is needed to transmit the signals at a short distance. These advantages compensate the necessity to use own energy for serving other network nodes.
As in other modern technologies, the army was the first big client of mobile ad-hoc, multi-hop networking. A need for efficient local transmission among the soldiers at the battlefield seems to be the ideal case for testing networking mode needing no “central” and/or “server” node. Even if marked as “top secret” for obvious reasons, the technologies had to migrate, sooner or later, to the civilian world. Businessmen see themselves as “business soldiers,” and they have similar needs. And even ordinary users would welcome network efficiency and range. So why not adapt the army-related solutions to everybody? Linked with personal firewalls and ciphering (virtual private networking, VPN), ad-hoc and multi-hop access is a need in many situations at home and at work. In addition, the network operators may significantly improve customer satisfaction. The users themselves may also apply mesh networking to new application areas, including self-managed “community” networks outside the control of the network operators/administrators.
Problems and questions emanating due to the success of ad-hoc and multi-hop networking create their own challenges. This book is intended to address both the technologies of mesh and ad-hoc networking and quality of service issues. The book adopts the following approach. First, potential application areas of ad-hoc and multi-hop networking are discussed, with emphasis on privacy, security, anonymity, trust management, traffic filtering, information searching and addressing, quality of services, personalization, and other aspects. We try to enumerate the biggest potential application areas, including telematics, public transportation, telemedicine, environment protection, public safety, marketing and shopping guidance. Last but not least, in this part of the book, we discuss the most important economic aspects of multi-hop and ad-hoc networking, both from the point of view of the network provider/operator and the end user.
Second, we describe several technical aspects of multi-hop networking while limiting the scope to three key networking technologies: WiFi (IEEE 802.11*), WiMAX (IEEE 802.16*), and LTE. Starting from the introduction of network architecture and basic terminology, we move on to discuss some important technical details, such as routing and node addressing, MANET multi-hop extensions, such as WiFi mesh networking 802.11s, enhancements to physical and media access control (MAC) layers for 802.16j protocol, and recent proposals toward efficient LTE relaying.
The book is addressed to a wide audience, from students of computer science and related domains to engineers and system designers. The book introduces the emerging multi-hop relay wireless networking technology and its applications. An engineer, who works for a wireless network service provider, ...
Table of contents
- COVER
- WILEY SERIES ON INFORMATION AND COMMUNICATION TECHNOLOGY
- TITLE PAGE
- COPYRIGHT PAGE
- FOREWORD
- PREFACE
- ABOUT THE AUTHORS
- LIST OF FIGURES
- LIST OF TABLES
- 1 Introduction
- 2 Architectural Requirements for Multi-hop and Ad-Hoc Networking
- 3 Application Areas for Multi-hop and Ad-Hoc Networking
- 4 Mesh Networking Using IEEE 802.11 Wireless Technologies
- 5 Wireless Relay Networking Using IEEE 802.16 WiMAX Technologies
- 6 Wireless Relay Networking with Long Term Evolution (LTE)
- 7 Summary
- REFERENCES
- INDEX