
Android Hacker's Handbook
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Android Hacker's Handbook
About this book
The first comprehensive guide to discovering and preventing attacks on the Android OS
As the Android operating system continues to increase its share of the smartphone market, smartphone hacking remains a growing threat. Written by experts who rank among the world's foremost Android security researchers, this book presents vulnerability discovery, analysis, and exploitation tools for the good guys. Following a detailed explanation of how the Android OS works and its overall security architecture, the authors examine how vulnerabilities can be discovered and exploits developed for various system components, preparing you to defend against them.
If you are a mobile device administrator, security researcher, Android app developer, or consultant responsible for evaluating Android security, you will find this guide is essential to your toolbox.
- A crack team of leading Android security researchers explain Android security risks, security design and architecture, rooting, fuzz testing, and vulnerability analysis
- Covers Android application building blocks and security as well as debugging and auditing Android apps
- Prepares mobile device administrators, security researchers, Android app developers, and security consultants to defend Android systems against attack
Android Hacker's Handbook is the first comprehensive resource for IT professionals charged with smartphone security.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Looking at the Ecosystem
Understanding Android's Roots
Company History
www.openhandsetalliance.com/oha_members.html.Version History
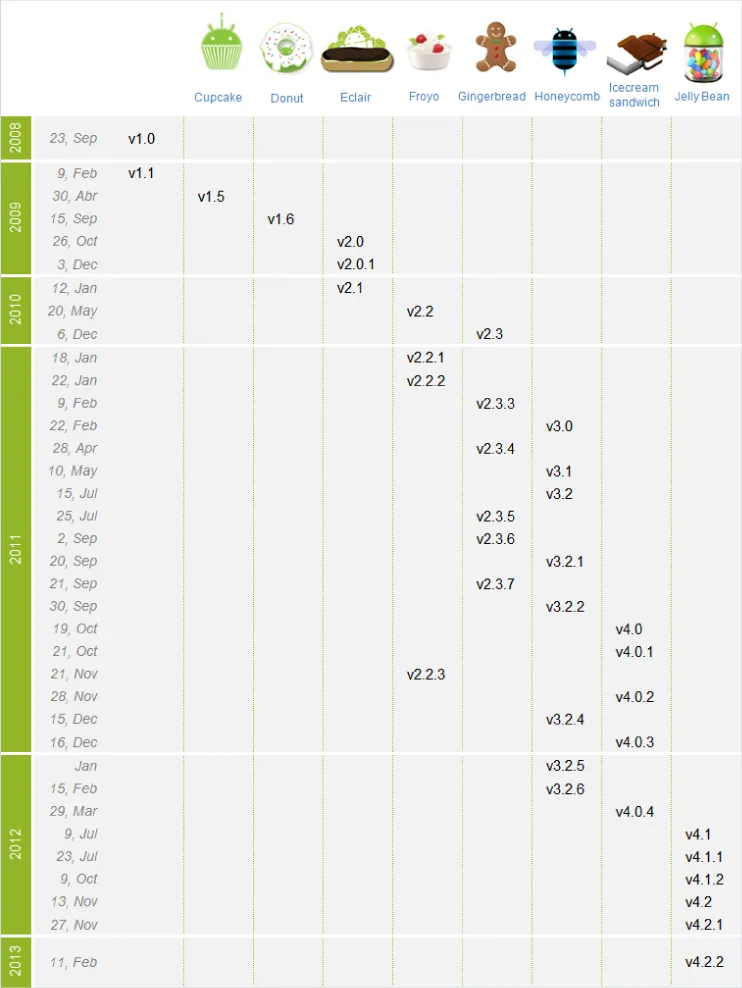
http://source.android.com/source/build-numbers.html. For example, take the build number JOP40D. The first letter represents the code name of the Android release (J is Jelly Bean). The second letter identifies the code branch from which the build was made, though its precise meaning varies from one build to the next. The third letter and subsequent two digits comprise a date code. The letter represents the quarter, starting from A, which means the first quarter of 2009. In the example, P represents the fourth quarter of 2012. The two digits signify days from the start of the quarter. In the example, P40 is November 10, 2012. The final letter differentiates individual versions for the same date, again starting with A. The first builds for a particular date, signified with A, don't usually use this letter.Examining the Device Pool
Google Nexus

Market Share
http://gs.statcounter.com/, show that Android is currently the number one player in the mobile operating system market, with 41.3 percent worldwide as of November 2013. Despite these small variations, all sources seem to agree that Android is the dominating mobile operating system.Release Adoption
http://developer.android.com/about/dashboards/. Additionally, Wikipedia contains a chart showing dashboard data aggregated over time. Figure 1.3 depicts the chart as of this writing, which includes data from December 2009 to February 2013.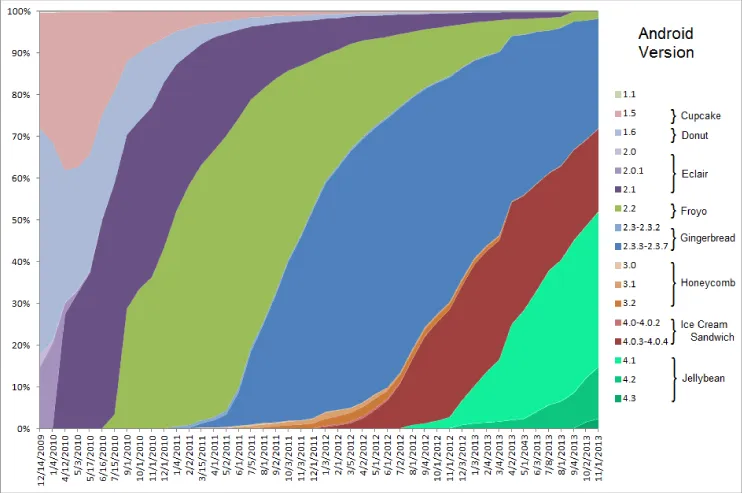
http://en.wikipedia.org/wiki/File:Android_historical_version_distribution.pngOpen Source, Mostly
apache.org/licenses/LICENSE-2.0. Some outliers do exist, mainly consisting on upstream projects, which are external open source projects on which Android depends. Two examples are the Linux kernel code that is licensed under GPLv2 and the WebKit project that uses a BSD-style license. The AOSP source repository brings all of these projects together in one place.Table of contents
- Cover
- Chapter 1: Looking at the Ecosystem
- Chapter 2: Android Security Design and Architecture
- Chapter 3: Rooting Your Device
- Chapter 4: Reviewing Application Security
- Chapter 5: Understanding Android's Attack Surface
- Chapter 6: Finding Vulnerabilities with Fuzz Testing
- Chapter 7: Debugging and Analyzing Vulnerabilities
- Chapter 8: Exploiting User Space Software
- Chapter 9: Return Oriented Programming
- Chapter 10: Hacking and Attacking the Kernel
- Chapter 11: Attacking the Radio Interface Layer
- Chapter 12: Exploit Mitigations
- Chapter 13: Hardware Attacks
- Appendix A: Tool Catalog
- Appendix B: Open Source Repositories
- Appendix C: References
- Introduction
- End User License Agreement
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app