
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
An example-driven approach to securing Oracle APEX applications
As a Rapid Application Development framework, Oracle Application Express (APEX) allows websites to easily be created based on data within an Oracle database. Using only a web browser, you can develop and deploy professional applications that are both fast and secure. However, as with any website, there is a security risk and threat, and securing APEX applications requires some specific knowledge of the framework. Written by well-known security specialists Recx, this book shows you the correct ways to implement your APEX applications to ensure that they are not vulnerable to attacks. Real-world examples of a variety of security vulnerabilities demonstrate attacks and show the techniques and best practices for making applications secure.
- Divides coverage into four sections, three of which cover the main classes of threat faced by web applications and the forth covers an APEX-specific protection mechanism
- Addresses the security issues that can arise, demonstrating secure application design
- Examines the most common class of vulnerability that allows attackers to invoke actions on behalf of other users and access sensitive data
The lead-by-example approach featured in this critical book teaches you basic "hacker" skills in order to show you how to validate and secure your APEX applications.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Access Control
THE PROBLEM
THE SOLUTION
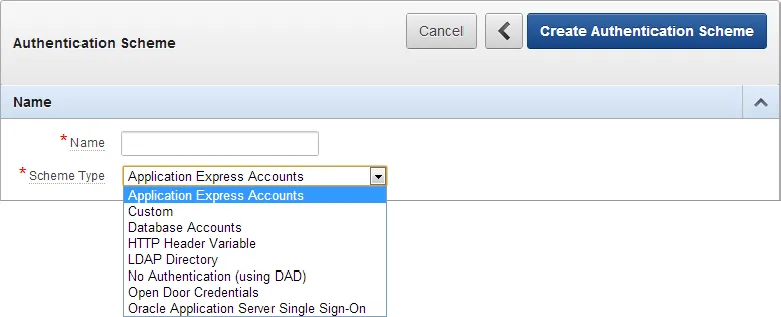
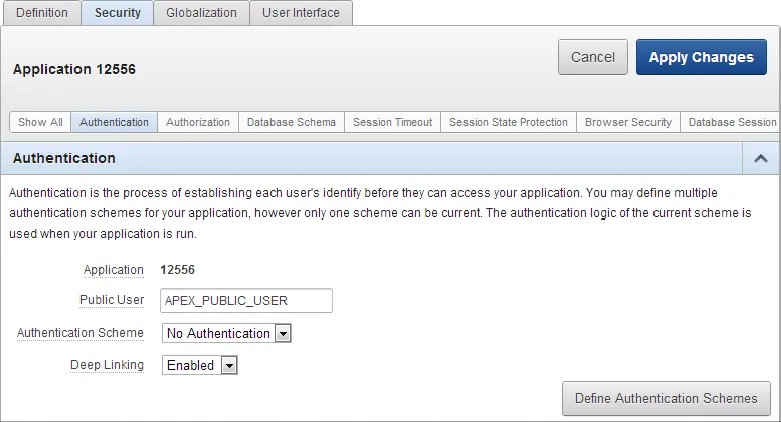
AUTHENTICATION
- Account lockout: If a user attempts authentication with an invalid password a number of times, consider rejecting future access for a certain period (the chosen threshold and timeout depends on the sensitivity of the application and the corporate security policy).
- Password complexity: Users invariably choose the simplest password they can, so an application should enforce a level of complexity so attackers cannot guess valid user credentials (again, the chosen policy depends on the application).
- Password reset: Where an application allows users to reset their password if they forget, it should either require some additional confirmation or send a reset link with a unique token to their configured e-mail address. The application should not allow a reset based on some publicly available information (for example, birth date or mother’s maiden name), and should never e-mail users their actual password.
- Password storage: The application should not store user credentials in clear text, but instead should store passwords that are cryptographically “hashed” and preferably “salted” with a unique value. This limits the damage of the worst-case-scenario of your account information being compromised, because an attacker would still not be able to authenticate as other users without “cracking” the password hashes. Storing passwords that are encrypted, rather than hashed, is not considered good practice because they can be decrypted should the key be discovered.
Application Authentication
Page Authentication
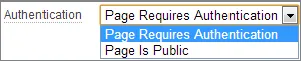
Table of contents
- Cover
- Contents
- Introduction
- Chapter 1: Access Control
- Chapter 2: Cross-Site Scripting
- Chapter 3: SQL Injection
- Chapter 4: Item Protection
- Appendix A: Using Apexsec to Locate Security Risks
- Appendix B: Updating Item Protection
- Appendix C: Untrusted Data Processing
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app