![]()
Chapter 1
Overview of the Companies
Before beginning any analytical testing of financial information, a financial forensic examiner needs to consider preliminary discussions with management to gather information that may become useful in analyzing financial information. For use within this book, a financial forensic examiner is any individual who wants to pursue a detailed analysis of a set of financial statements to determine not only the consistency of the financial information but also possible anomalies that may suggest the possibility of fraudulent activity. Discussions should provide information relating to general company operations, allowing the financial forensic examiner to understand management's philosophy and general operating style. These discussions should also include financial matters, such as profit margins built into pricing products and any unusual transactions or changes that might have occurred during the period under examination. These discussions may reveal information that the financial forensic examiner will need to assess in determining the results of analytical testing of financial information.
Herein lies a lesson for the financial forensic examiner: Anomalies in financial information may occur and may not be representative of fraudulent activity.
The Four Companies
Before beginning any of the analytics noted in future chapters, this chapter is dedicated to providing general information about each company, including basic financial information and an overview of each company's general operations. Specific information for each case is available so the financial forensic examiner may follow each case study through the analytical process of finding anomalies in the financial information. This chapter will provide the foundation for interpretations made from the various tools and techniques shown throughout the book.
Company 1
Company 1 is a communications company whose primary revenues relate to advertising. The company is an S-corporation and includes three shareholders. Shareholder 2 maintained the financial information for the company. Throughout the history of the corporation, various shareholders sold their shares to new shareholders, with the exception of Shareholder 2, who would add any rounding of shares to Shareholder 2's total shares, increasing the total shares over time. Shareholder 2 was also the corporate secretary and treasurer, even though both corporate positions were not to be held by the same person, according to the Articles of Incorporation. The other two shareholders did not protest this arrangement.
Even though Company 1 filed annual tax returns, management did not review monthly, quarterly, or even annually prepared financial statements. Shareholder 3 suspected the financial information was flawed and began retaining information related to the company for an independent external review. Having gathered sufficient information, Shareholder 3 presented the documents to an external auditor for review.
Since formal financial statements had never been prepared for management, information subject to examination included sales journals, customer ledger cards, tax returns, bank statements, cash disbursement journals, and payroll journals. Even though an accounting software package maintained the financial information, Shareholder 2 would not supply a backup of the files. Financial information shown in the following tables came from the tax returns provided by the client and adjusted to book basis using the M-1 reconciliations on the tax returns.
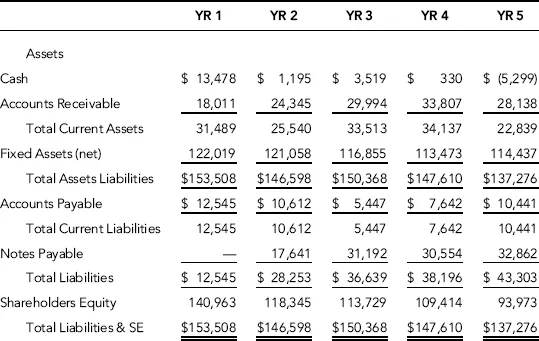
Figure 1.1 illustrates the reconstructed balance sheet for the periods under investigation and condensed for presentation purposes.
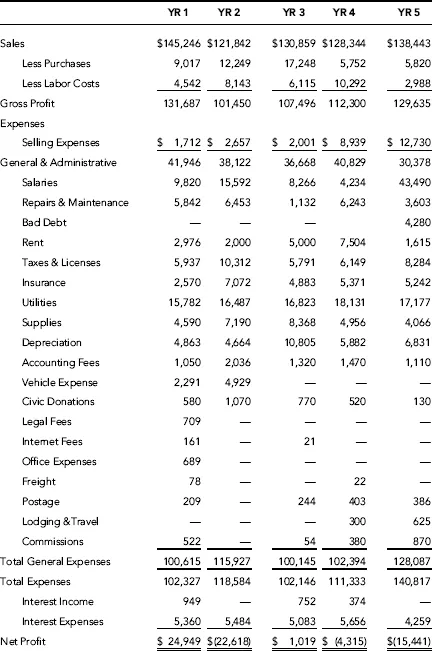
Figure 1.2 shows the reconstructed income statements for the periods under investigation and condensed for presentation purposes. More detail has been included for additional discussions in Chapter 2.
After the recomputation of the financial statements, an integral part of the investigative planning stage used various analytical tools and techniques employed to determine specific focus areas for further investigations. Due to the nature of inconsistent postings of similar expenses in various categories during a fiscal year, the income statement presented contains some reclassifications among account balances for comparisons. The results of these tools and techniques are the focus of the case study for Company 1 throughout the remaining chapters.
Other developments in the examination included the finding of a checking and savings account that was in the company's name but not recorded in the financial information, and another entity set up as a partnership for the three shareholders to maintain the rental property owned by the S-corporation.
Herein lies a lesson for the financial forensic examiner: Financial records are not always entirely conclusive for all transactions.
Although the rental property was not vacant during the periods under investigation, the company did not complete tax returns for the partnership and did not keep financial records for the partnership. The use of off-book bank accounts allowed Shareholder 2 to remove funds from these accounts and then deposit these funds into the company, recording a note payable to Shareholder 2, although the funds in these accounts were actually revenues from advertising sales and rental income for the partnership.
As the investigation progressed, interviews with Shareholder 2 revealed that the intent of the fraud was to reduce the net worth of the company so that Shareholder 1 and Shareholder 2 would be able to purchase the shares of the heir of Shareholder 3 at a fraction of their true net worth. The local district attorney received a report of the examination findings and ultimately the shareholders' attorney negotiated the case before any court appearance. The plea-bargain arrangements removed the note payable to Shareholder 2 from the company's financial records, and required the hiring of an additional employee to manage the finances of the company, thus removing all operational and corporate authority from Shareholder 2.
Company 2
Company 2 is a manufacturing company with a niche in the market as the sole source for specific parts for large equipment, such as excavators, wheel loaders, cranes, and so forth. As a sole-source provider of these specific products, the company has a select customer base, maintaining a good working relationship with its customers and recording very little, if any, bad debt. The company monitored its receivables continuously and many of its customers paid their balances within the 30-day period, or the amounts due were collected at the time of delivery. Due to the nature of its manufacturing products, cost of sales and gross margins are consistent among the various models of its product lines.
The company is a C-corporation and did not have external audits of its financial records, just external compilations and reviews of its financial information. The financial information compiled for management's reviews consisted of specific ratios requested by management relating to liquidity, such as the current ratio, the quick ratio, income before tax to net worth, the debt coverage ratio, and the leverage ratio. The financial information related to the reviews did not include cash flow statements as part of the basic reports, nor did it include ratios relating to performance, such as gross margins and measurements of profitability.
Only the accounting staff had access to the financial information maintained through a commercial accounting software package. The accounting staff had access to various modules of the software, but not the complete accounting package. The office manager and the chief financial officer (CFO) both had unrestricted access to the accounting software. Other basic internal controls in place included appropriate segregation of duties relating to receiving cash, depositing cash, writing checks, and performing bank reconciliations. The CFO would use the signature stamp (kept locked in a filing cabinet in the office) to sign the checks. The CFO would ensure that each check had all support documentation attached before the checks were stamped. Only the office manager and the CFO were able to record manual journal entries in the accounting system.
The company issued hundreds of checks monthly, so staff did n...