![]()
1
Fundamentals
This introductory chapter uses the most appropriate terminology to give an overview of the history of the structure of telecommunications networks. For specialists in the domain, the chapter offers a recap on networking techniques, and the avenues which are open to companies are also touched upon.
1.1. Different kinds of network
1.1.1. Classic definitions
For simplicity’s sake, the definitions given here take account of both technical considerations and regulatory aspects. They are accurate at the time of writing (2014). For further details on the official terminology used, readers may consult the ITU.[1]
When we speak of a “network”, we mean a combination of various devices, management software packages and links which enable a certain number of terminals, distributed within a specific geographical area, to communicate with one another.
A local area network is one whose coverage is restricted to the dimensions of a particular private space – e.g. the premises of a company (an area between 10 m and 1 km in diameter). The abbreviation LAN is used to speak of such networks). There are various types of LAN, including hardwired LANs (where the connections are formed by metal wires or optical fibers), wireless LANs (WLANs) and hybrid LANs. LANs are managed by their owners, and are often the responsibility of the technicians in a company’s IT department. They may be completely independent of any external connection, or may be linked to another network. Small local networks are considered to be Personal Area Networks (PANs). Low energy-consumption wireless PANs are known as LoW PANs.
For greater distances – say, between 5 and 50 km, the expression “Metropolitan Area Network” (MAN) is used. An MAN belongs to several entities in cooperation with one another. It will be connected to one or more “Wide Area Networks” (WANs).
Thus, a WAN encompasses a number of MANs. Its coverage extends over diameters greater than that of a metropolitan area. WANs may be made up of numerous hardwired and wireless connections. Usually, they are managed by a number of competing companies. They are capable of handling communications to and from outside the LANs, including international connections. A WAN may be made up of hardwired, wireless and satellite connections.
In the medical field, we speak of Medical Body Area Networks (MBAN) for therapeutic applications or for clinical tests performed on the human body, using radio electric equipment exploiting the frequency bands authorized for that purpose. The terms BAN (Body Area Network) and BSN (Body Sensor Network) are often used to describe the use of portable low-consumption computerized devices, which function on, in or around the human body, for a wide range of applications – medical, consumer electronics, entertainment and more.
On a technical level, a large-scale network includes a “core network” (also known as a core network) and an access network. The core network handles the flow of traffic between network connection centers and intercity transfer centers. The core network is the junction between all the concentration points in the wired and radio access networks. In general, there tends to be one core network for each country, and one per network operator as well. The access network is the network which facilitates the receiving of calls and traffic hardwired or wireless subscribers. To define the interface between a wireless subscriber and the main network, we use the acronyms RAN (Radio Access Network) in 2G technology (2G means second generation in mobile telephony systems), UTRAN (Universal Terrestrial Radio Access Network) for 3G and eUTRAN for 4G.
Finally, we must mention private networks – i.e. those which are for the sole use of one company, and are made up of the equipment and resources in the general network of a particular operator. Real private networks (RPNs) are those which are physically in permanent existence, whilst Virtual Private Networks (VPNs) are those whose elements are added or removed on request by a computer. IVPRs are international virtual private networks.
A more recent vision represents the architecture of public communications networks as hierarchically-ranked set, hinged around three levels: the “backbone network” (or core network), the “backhaul network” and the “service network”; the latter two make up the “access network”. Backhaul networks, which are established at regional or municipal level, form the link between the backbone network and the subscribers, by carrying traffic between the service points where the operators’ distribution devices are installed.
1.1.2. National networks and international connections
Traditionally, every country has its own communications network, structured in accordance with the number of regions needing to be served and the density of subscribers to be connected. That national network is connected to the networks of the neighboring countries by way of international transit centers (or “nodes”). So as to avoid the demultiplication of operations when multiple transits take place, countries often agree to group together traffic with the same destination, depending on the affinity between the countries. There are bilateral international connections between the 193 UN member states (either direct or requiring transit operations), which form the basis of the global communications service. In classic network structures, financial viability is only guaranteed for around 10% of international connections, as there is insufficient traffic over the other connections.
Between a certain number of selected countries, it is possible to establish international networks which simply handle large volumes of business traffic: this is the function of IRCs (Internationally Recognized Carriers). Unlike RPOAs (Recognized Private Operating Agencies), which are public and private network operators recognized by the ITU (the International Telecommunications Union – the United Nations agency for telecoms), IRCs handle the business traffic of specialist companies. For example, SWIFT (Society for Worldwide Interbank Financial Telecommunication) is a cooperative which runs a private international messaging network linking over 10,000 banks. SITA (Société internationale de télécommunications aéronautiques – International Aeronautical Telecommunications Society) is an organization which provides computing and communications services to the aeronautics industry, through a vast international private network.
Although it does not have the status of an IRC, the activities of the Internet have been extended so that it now plays a very similar role in terms of international connections. The Internet is distributed in every country by network operators using Internet-connection application servers, which are also known as ISPs (Internet Service Providers). The Internet is distributed through access networks offered by different ISPs. The equivalent of the backbone network of the Internet is made up of high data rate connections between GIX (Global Internet eXchanges): switching and routing centers.
A GIX is a center housed in a physical infrastructure which interconnected networks use to accelerate and optimize their Internet traffic, thanks to what is known as “peering” – mutual agreements between the operators. GIX nodes are open to any and all network operators wishing to connect to them: Internet Service Providers, service companies, large accounts, local collectives, associations, etc. SOHOs (small offices), SMEs and individuals benefit from the use of GIXs by their ISP.
IPX (IP eXchange) is a model for the interconnection of telecommunications networks favored by the “GSM Association (GSMA)”, for the exchange of different IP traffic from mobile and landline network operators and service providers, such as ISPs. The aim of this structure is not to compete with the Internet. It is an alternative for clerical application providers, and at all stages in the value chain, which is supported by Service-Level Agreements (SLAs), to guarantee performance, quality and security. Indeed, in today’s world, it is necessary to minimize the number of conversions of voice signals between circuit-switching networks and packet-switching networks. The IPX architecture also includes inter-network packet exchange interfaces (peering points).
1.1.3. Network exploiters and operators
The policy of deregulation, which has been widely implemented in Europe and indeed the world over since the 1980s, has opened up the telecommunications markets to competition, and forced network administrations to become private commercial entities. Alongside the role of the network exploiter (exploitant), that of the network operator (opérateur) has come into being.
In the author’s native French, this distinction is an important one: it relates to the different responsibilities attached to these two types of enterprise. The nuance is rooted in the legal obligations incumbent upon a “historical” network exploiter (closely related to the idea of a public service, with a duty to provide 24/7 coverage for the whole of a national territory, free emergency calls, rights of passage and obligations in cases of public good). An opérateur, on the other hand, is a purely commercial enterprise, free to engage in competition but also to collaborate with other operators (of which there may be several within a given country). An “operator” benefits from the skill and experience of the “network exploiter” providing the basic service – including for the maintenance of cables, for example. Unfortunately, in English, this distinction is difficult to preserve, as one tends simply to speak of a “network operator”. Where the separation is of particular importance for the discussion, the word “network exploiter” will be used; otherwise, the term “operator” is systematically employed for both entities.
The distinction between the work done by network exploiters and network operators has become a tenuous one. In principle, whilst the network exploiters invest in the installation of infrastructures and carry out the exploitation and maintenance of complete and diverse networks, in addition to general service provision, network operators concentrate their efforts on one clearly-defined part of the range of tasks of a network exploiter. The service offered by operators is often original and innovative. This type of specialization of activity means that there is a dynamic aspect to the service provision which is both technical and commercial. Although strict terminology cannot yield a rational classification, the evolution of the professions leads us to distinguish a number of different types of actors or operators, including:
– Telco2.0 organizations, which are represented by actors who, thanks to the Internet, now harbor the ambition to take possession of value chains from the domain of conventional network exploiters, by controlling the distribution of value-added services (e.g. Amazon, Apple, Google, social networks, etc.);
– MVNOs (Mobile Virtual Network Operators), which do not have a dedicated radio frequency (RF) spectrum, or their own networking infrastructure. They sign agreements with mobile network exploiters, purchasing trafficking capacities or usage concessions from them, and selling services under their own brand names;
– BVNOs (Broadband Virtual Network Operators), which play the same role as MVNOs but with broadband;
– Infrastructure operators, who specialize in the design, construction, technical running and commercialization of very high data rate optical networks, under-roads, terrestrial and submarine, access to GIX (Global Internet eXchange, as discussed above), supply of “cloud computing” services (remote, Internet-based computing services), corporate telephony, and in hosting capability for the deployment of services to other operators or companies. They may also have the status of a regional not-for-profit organizations, or be partners in local collectives for public-initiative networks (PINs), and infrastructure operators;
– local operators, who cater for the communication needs of SOHOs, SMEs and administrations, in terms of Internet connections, corporate telephony, server hosting and network security, with computer applications hosted by a cloud computing service;
– an operator specializing in corporate-telephony and professional computing, oriented toward speech recognition and -synthesis technologies, who creates and markets tools which are essential for consumer relations for large enterprises and health establishments (university hospitals, clinics). Such an operator has developed software tools capable of handling telephone calls, irrespective of the language used, with virtual operators. When the call is connected, the called is asked to speak the name of the department or person he/she wishes to contact. The virtual operator responds to each demand by employing a number of scenarios. These new tools are able to extend the operating hours of the telephone answering service, reduce costs and improve a company’s image by way of a personalized, efficient reception service;
– an operator who may specialize in the provision of communication services, e.g. for yacht owners, offering a value-added service by means of SIM cards, in partnership with the other operators, for varied bundles of services (GSM, Internet, television), playing the role of the single port of call from the Mediterranean to the Caribbean.
After Skype was bought by Microsoft, it began offering Internet telephony to companies. Thus, in March 2013, Skype was forced to declare itself to be a telecoms network exploiter in France. “The fact that Skype provides the services of an electronic communications operator, and in particular the fact of providing a public telephone service, also means it must meet certain obligations, including the handling of emergency calls and the use of the means necessary for legal interception of calls” (article L. 33-1 of the Code des postes et des communications électroniques, CPCE - Postal and electronic communications code). However, Skype maintains that it is not a true network operator or an MVNO, because in fact, Skype provides users with no hardware and no SIM cards. It does not require a paid subscription, it does not invest in the telephone network, and it does not install relay antennas or centers. Declaring itself to be an operator would require connection to a paying telephone network, keeping of a directory, and installation and maintenance of public phone booths. Ultimately, on a technical level, Skype, which does not use the SIP protocol, proves to be incompatible with the hardware and autoswitches used by other network operators.
1.1.4. Economic role of MVNOs and VNO
The introduction of MVNOs into a national mobile telephony market is supposed to stimulate the global market – either by price competition or by the provision of particularly attractive services and terminals. It does not necessarily require the redistribution of the frequencies between the beneficiaries, because MVNOs use the same frequencies as the mobile network operator with which they are associated. The entry of Apple into the Chinese market, or that of Google into many other mobile networks, can be achieved in this way, with the promise of investment as a result. The acceptance of this exchange – foreign investment for the creation of an MVNO – is often left up to the judgment of the regulatory services.
The introduction of VNOs into a national telephony market stimulates demand on target markets. It may facilitate the sale of original terminals or services. The introduction of new actors or new operators into the communications market reduces the market share held by the historical network exploiter, and drives down the price of its services. As the profit margins of the traditional network exploiters decrease, so too do their capacities to invest.
1.1.5. Public and private networks
The age-old notions of a public network and a private network have been revised (see the ARCEP Website for the most up-to-date information on this topic).
The “public network” used to be that which provided public communication services with constant (24/7) service requirements, total coverage of a country’s territory, handling of emergency calls, provision of directories, etc. The privatization of the historical network exploiters in most countries has caused this concept to change.
“Universal service” must be understood as a minimum set of services which operators have to provide their users in accordance with the legislation in force. An example of a universal service is the United States Postal Service.
A “private network”, often constructed using rented bandwidth for connections, may be built for the benefit of a particular company or a group of clients (e.g. SWIFT, HP, PMU [a betting network in France]). These networks, be they hardwired or radio electric, are specialized for particular services: banking messages, voice messages, still or moving images, fax, text or data-messaging, etc. They may be characterized, for example, by the process of leaving and returning of messages. PMR and PAMR are private radio electric networks with shared frequency resources:
– PMR – Private Mobile Radio communications: a mobile communication system using radio waves over a short or medium range, for use by professionals, security personnel, public works, industry, etc. Examples include the walkie-talkie from Motorola, TETRA, PMR446, RUBIS, etc. PMR facilitates the communication of messages to a particular group, with or without confidentiality;
– PAMR – Public Access Mobile Radio: radio electric communications systems for professional activities, which can be connected to the public network, divided into a number of categories defined by the regulations.
1.1.6. Fixed and radio networks
A fixed network is one wherein the connections between the devices are formed by terrestrial and submarine cables, self-supporting cables or approved supports in the public or private domain. The communications terminals are not mobile.
A radio network uses radio links to establish the connections between the network centers and the users’ mobile terminals.
1.1.7. Main operators worldwide
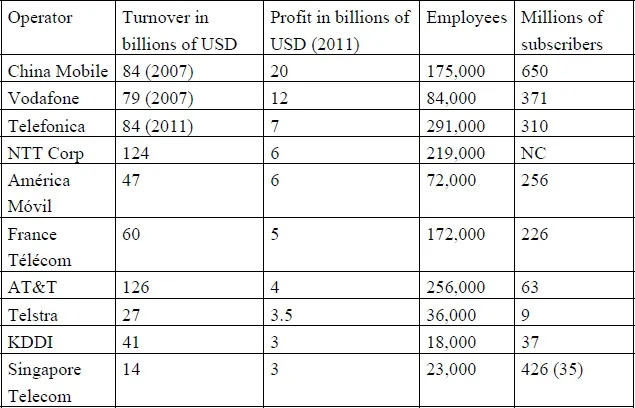
In view of economic globalization, the networking market covers the whole of the planet. Logically, in time, we expect to see only those with international stature survive. However, the system of competition in Europe has weakened European operators in favor of others, who are benefiting from the current favorable conditions. The current regulation system has led to the fracturing of the sector: there are 159 network operators in Europe, whereas in the United States there are only four. Network operators are also under pressure from Internet actors in terms of services (e.g. Google, Microsoft), and it is always possible that mergers or acquisitions will take place.
Table 1.1. Main telecoms network operators (2011)
This selection of operators was constructed from data provided by BVD Info. However, it shows that there are no discernible recurring “laws” linking the number of subscribers, workforce size and financial results.
1.1.8. Pan-European network project
In January 2013, AT&T and Verizon, between them, controlled 75% of the American market (340 million users). The seemingly-demagogic European regulatory constraints have scared away investment. Tariffs in 2012 in France were nearly twice as low as in Germany, and three times lower than in the United States.
ETNO, the European Telecommunications Network Operators Association, which brings together 38 European telecoms companies from 35 Member States, stated at the start of 2013 that there were no projects in its then research program relating to the unification of mobile networks in Europe. However, the European authorities do want to put an end to the fragmentation of the European telecoms market, both for wired and wireless communication. In 2013, the project for pooling of infrastructures or simpler regulation of communications between limitrophe states was again brought up among the major European network operators, without the presence of European industrialists, who feel their business would be damaged by the splitting up of the European equipment market.
The European deregulation authorities, which actually caused the aforementioned fragmentation in order to encourage competition and drive down prices, now wish to unify the networks in 28 countries into a single entity using uniform technology and ...