
eBook - ePub
Information Technology Risk Management in Enterprise Environments
A Review of Industry Practices and a Practical Guide to Risk Management Teams
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Information Technology Risk Management in Enterprise Environments
A Review of Industry Practices and a Practical Guide to Risk Management Teams
About this book
- Discusses all types of corporate risks and practical means of defending against them.
- Security is currently identified as a critical area of Information Technology management by a majority of government, commercial, and industrial organizations.
- Offers an effective risk management program, which is the most critical function of an information security program.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
At the moment all of our mobile-responsive ePub books are available to download via the app. Most of our PDFs are also available to download and we're working on making the final remaining ones downloadable now. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Information Technology Risk Management in Enterprise Environments by Daniel Minoli,Jake Kouns in PDF and/or ePUB format, as well as other popular books in Computer Science & Cyber Security. We have over one million books available in our catalogue for you to explore.
Information
PART I
INDUSTRY PRACTICES IN RISK MANAGEMENT
CHAPTER 1
INFORMATION SECURITY RISK MANAGEMENT IMPERATIVES AND OPPORTUNITIES
1.1 RISK MANAGEMENT PURPOSE AND SCOPE
1.1.1 Purpose of Risk Management
This text deals with information technology (IT) risk management (ITRM), which, given the context of this text, we also just refer to as risk management.1 Concerns about the possibility of compromise and/or the loss of proprietary information have reached critical levels in many organizations in recent years as a barrage of news bulletins reporting on infractions and product defects, staffs shortfalls and shortcomings, functions’ outsourcings and offshorings, political instabilities in a number of countries and in wider regions, and management’s emphasis on short-term financial breakeven has become all too frequent. Cyber attacks continue to be a source of significant exposure to organizations of all types, and, as a consequence, potential damage, potential impairment, and/or potential incapacitation of IT assets have become fundamental business viability/continuity issues.
Information Security2 is recognized at this juncture to be a key area of IT management by a majority of government, commercial, and industrial organizations. Information Security is defined as the set of mechanisms, techniques, measures, and administrative processes employed to protect IT assets from unauthorized access, (mis)appropriation, manipulation, modification, loss, or (mis)use and from unintentional disclosure of data and information embedded in these assets. Some organizations have individuals on staff with a plethora of security certifications, yet these organizations continue to be afflicted with security breaches on a fairly routine basis and continue to be exposed to risk; this implies that perhaps other approaches to information security are needed. Practitioners of information security are all well aware that exposure to risk is ever-changing and that it is also hard to assess; therefore, what is needed to manage and minimize risk in organizations is a diversified, versatile, and experienced IT/networking staff along with a solid set of policies, processes, and procedures that create a reliable information security program. This approach is typically much more successful as compared to the case where an organization just attempts to rely on ultra-narrow staffers with cookbooks of perishable memorized software commands specific to a given version of a given program of a given vendor to produce results, where the organization seems to be assuming that the real-life information security issues are similar to an academic pre-canned rapid-fire test for abstract scholastic grades, and simply believes that an alphabet soup of tags following one’s name is sufficient (or necessary) to address incessant IT security threats.
Risk is a quantitative measure of the potential damage caused by a threat, by a vulnerability, or by an event (malicious or nonmalicious) that affects the set of IT assets owned by the organization. Risk exposure (that is, being subjected to risk-generating events) leads to potential losses, and risk is a measure of the “average” (typical) loss that may be expected from that exposure. Risk, therefore, is a quantitative measure of the damage that can incur to a given asset even after (a number of) information security measures have been deployed by the organization. Obviously, when the risk is high, an enhanced set of information security controls, specific to the situation at hand, needs to be deployed fairly rapidly in the IT environment of the organization. See Table 1.1 for some risk- related definitions, loosely modeled after [HUB200701]. The term “information asset” refers here to actual data elements, records, files, software systems (applications), and so on, while the term “IT asset” refers to the broader set of assets including the hardware, the media, the communications elements, and the actual IT environment of the enterprise; the general term “asset,” refers to either “information asset” or “IT asset;” or both, depending on context. Typical corporate IT assets in a commercial enterprise environment include, but are not limited to, the following:
- Desktops PCs and laptops
- Mobile devices and wireless networks (e.g., PDAs, Wi-Fi/Bluetooth devices)
- Application servers, mainframes
- Mail servers
- Web servers
- Database servers (data warehouses, storage) as well as the entire universe of corporate data, records, memos, reports, etc.
- Network elements (switches, routers, firewalls, appliances, etc.)
- PBXs, IP-PBXs, VRUs, ACDs, voicemail systems, etc.
- Mobility (support) systems (Virtual Private Network nodes, wireless e-mail servers, etc.)
TABLE 1.1. Uncertainty, Probability, and Risk
| Uncertainty | The lack of complete certainty, that is, the existence of more than one possibility for the outcome. The “true” outcome/state/result/value is not known. |
| Measurement of uncertainty | A set of probabilities assigned to a set of possibilities (specifically for risk events, threats, and/or vulnerabilities). |
| Risk exposure (also, liability) | A state of uncertainty where some of the possibilities (also colloquially called “risks”) involve a loss, catastrophe, or other undesirable outcome. An environment exposed to risk events, threats, and/or vulnerabilities. Each new risk event, threat, and/or vulnerability gives rise to new risk exposure. |
| Measurement of risk | A set of possibilities, each with quantified probabilities and quantified losses. |
| Risk (singular) | The expected loss. Namely, the aggregation (summation) of the possibilities, their probabilities, and the loss associated with each possibility. |
| Risks (plural) (colloquial) | Individual possibilities (risk events) that are encountered with risk exposures. |
| Risk-exposing event (also called risk event) | Any changes in the state of the environment that have the potential of creating a new state where there is nonzero risk. |
- Power sources
- Systems deployed in remote/branch locations (including international locations)
- Key organizational business processes (e.g., order processing, billing, procurement, customer relationship management, and so on)
Continuing with some definitions, a security threat is an occurrence, situation, or activity that has the potential to cause harm to the IT assets. A vulnerability (or weakness) is a lack of a safeguard that may be exploited by a threat, causing harm to the IT assets; specifically, it can be a software flaw that permits an exogenous agent to use a computer system without authorization or use it with an authorization level in excess of that which the system owner specifically granted to said agent. Risk-exposing events (also called risk events) are any changes in the state of the environment that have the potential of creating a new state where there is nonzero risk. Risk events and vulnerabilities are implicitly related in the context of this discussion in the sense that a vulnerability is ultimately given an opportunity for harm by some subtending event, malicious or nonmalicious. For example, in a so-called “nonmalicious event,” a flaw may be inadvertently introduced in some software release by its designers; the event of having the IT group load and distribute that software throughout the enterprise creates a predicament where risk ensues. A “malicious” event may be a direct attack on the organization’s firewalls, routers, website(s), or data warehouse.
Note: Some people use the term “risk” (singular) more loosely than defined above to mean a potential threat, vulnerability, or (risk) event; we endeavor to avoid this phraseology, and we use the term risk to formally describe the quantitative (numerical) measure of the underlying damage-causing issues, and not the issues themselves.
We acknowledge that the term “risks” (plural) is used colloquially to describe the set of individual possibilities (risk events) that are encountered with risk exposures. We occasionally use this phraseology.
Information security spans the areas of confidentiality, integrity, and availability. Confidentiality is protection against unauthorized access, appropriation, or use of assets. Integrity is protection against unauthorized manipulation, modification, or loss of assets. Availability is protection against blockage, limitation, or diminution of benefit from an asset that is owed. The Computer Crime and Intellectual Property Section (CCIPS) Computer Intrusion Cases of the U.S. Department of Justice defines these terms (and considers respective infractions as crimes) as follows:
- Confidentiality. A breach of confidentiality occurs when a person knowingly accesses a computer without authorization or exceeding authorized access. Confidentiality is compromised when a hacker views or copies proprietary or private information, such as a credit card number or trade secret.
- Integrity. A breach of integrity occurs when a system or data has been accidentally or maliciously modified, altered, or destroyed without authorization. For example, viruses and worms alter the source code in order to allow a hacker to gain unauthorized access to a computer system.
- Availability. A breach of availability occurs when an authorized user is prevented from timely, reliable access to data or a system. An example of this is a denial of service (DoS) attack.
At this point in time, the practical challenges for enterprises are how to organize and run an efficient and effective information security program for persistent, high-grade protection and, in turn, how to actually (i) identify risk events, (ii) assess the risk, and (iii) mitigate (“manage”) the environment to reduce risk. IT risk management (information security risk management) is the process of reducing IT risk (a process is a well-defined, repeatable sequences of activities.) Risk management is a continuous process. IT risk management encompasses five processes (also see Table 1.2 and Figure 1.1):
1. (Ongoing) identification of threats, vulnerabilities, or (risk) events impacting the set of IT assets owned by the organization
2. Risk assessment (also called risk analysis by some, especially when combined with Step 1)
3. Risk mitigation planning
4. Risk mitigation implementation
5. Evaluation of the mitigation’s effectiveness
TABLE 1.2. Risk Management Processes
| Risk identification | The process of identifying threats, vulnerabilities, or events (malicious or nonmalicious, deterministic/planned, or random) impacting the set of IT assets owned by the organization. |
| Risk assessment | The process of calculating quantitatively the potential damage and/or monetary cost caused by a threat, a vulnerability, or by an event impacting the set of IT assets owned by the organization. Identification of the potential damage to the IT assets and/or to the business processes based on previous internal and external events, input from subject matter experts, and audits. Specifically, this entails (a) quantifying the potential damage, and (b) quantifying the probability that damage will occur. |
| Risk mitigation planning | Process for controlling and mitigating IT risks. It typically includes cost-benefit analysis, and the selection, implementation, test, and security evaluation of safeguards. This overall system security review considers both effectiveness and efficiency, including impact on the mission and constraints due to policy, regulations, and laws [STO200201]. |
| Risk mitigation implementation | Deploying and placing in service equipment and/or solution identified during the risk mitigation planning phase, or actuating new corrective processes. |
| Evaluation of the mitigation’s effectiveness | Monitoring the environment for effectiveness against the previous set of threats, vulnerabilities, or events, as well as determining if new/different threats, vulnerabilities, or events results from the modifications made to the environment. |
When the term risk management (or information security risk management) is used in this text, all five of these processes are implied. Risk management is a fundamental, yet complex, element of information security. Figure 1.2, contained in the International Organization for Standardization (ISO) 27002 standard, depicts the macrocosms of information security management (ISM), including risk management. The National Institute of Standards and Technology (NIST) defines risk management (in their recommendation NIST SP 800–30) as the process that allows IT managers to balance the operational and economic costs of protective measures and achieve gains in mission capability by protecting the IT systems and data that support their organizations’ missions. Figure 1.3 provides a graphical view of the (assessment) process of NIST SP 800–30. Figure 1.4 depicts the ISO 31000 view of risk management. Figure 1.5 depicts the view in the Australian/New Zealand Standard AS/NZS 4360:2004. Figure 1.6 shows a vendor-based approach, specifically from Microsoft. Finally, Figure 1.7 depicts the view taken by OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation), a risk-based strategic assessment and planning technique for security, developed by CERT (Carnegie Mellon University’s Computer Emergency Response Team).
FIGURE 1.1. Risk management process as defined in this text.
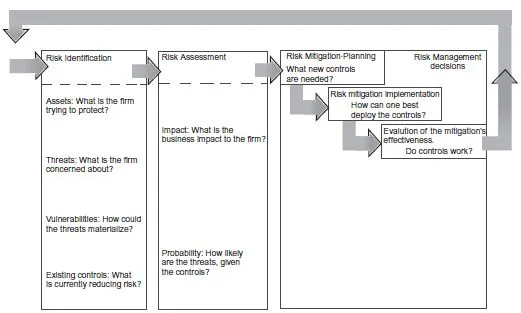
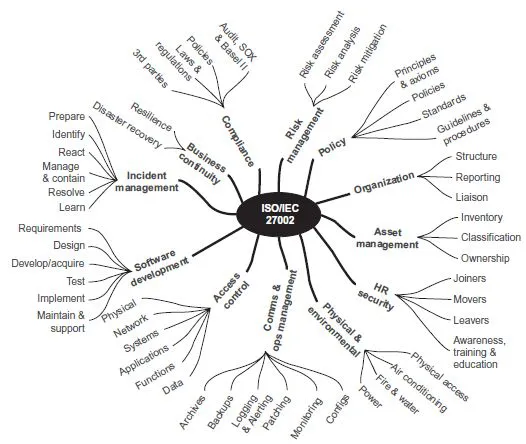
FIGURE 1.2. A view of information security management, as conceived in ISO 27002.
A recent confluence of technical and geopolitical factors has sensitized decision-makers about the business and legal consequences of cyber intrusions and risk exposures to an organization...
Table of contents
- Cover
- Title page
- Copyright Page
- Dedication
- PREFACE
- ABOUT THE AUTHORS
- PART I
- PART II
- BASIC GLOSSARY OF TERMS USED IN THIS TEXT
- INDEX