
Internet Communications Using SIP
Delivering VoIP and Multimedia Services with Session Initiation Protocol
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Internet Communications Using SIP
Delivering VoIP and Multimedia Services with Session Initiation Protocol
About this book
"This book is like a good tour guide.It doesn't just describe the major attractions; you share in the history, spirit, language, and culture of the place."
--Henning Schulzrinne, Professor, Columbia University Since its birth in 1996, Session Initiation Protocol (SIP) has grown up. As a richer, much more robust technology, SIP today is fully capable of supporting the communication systems that power our twenty-first century work and life. This second edition handbook has been revamped to cover the newest standards, services, and products. You'll find the latest on SIP usage beyond VoIP, including Presence, instant messaging (IM), mobility, and emergency services, as well as peer-to-peer SIP applications, quality-of-service, and security issues--everything you need to build and deploy today's SIP services. This book will help you
* Work with SIP in Presence and event-based communications
* Handle SIP-based application-level mobility issues
* Develop applications to facilitate communications access for users with disabilities
* Set up Internet-based emergency services
* Explore how peer-to-peer SIP systems may change VoIP
* Understand the critical importance of Internet transparency
* Identify relevant standards and specifications
* Handle potential quality-of-service and security problems
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Chapter 1
Introduction
Problem: Too Many Public Networks
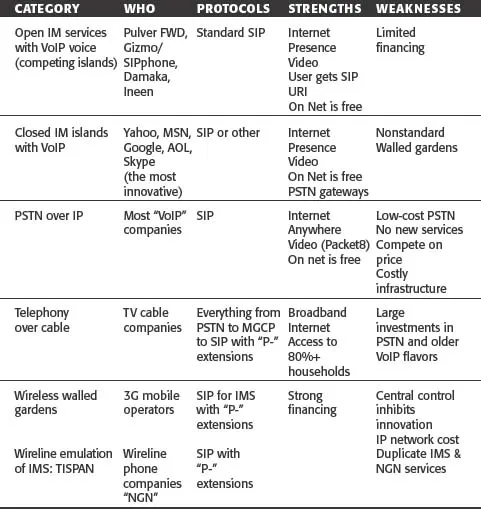
Incompatible Enterprise Communications
- Proprietary PBX and their phones. Phones from one PBX cannot be used by another.
- Instant messaging is a separate system from the PBX.
- Various IM systems don’t talk to each other.
- Voice conferencing and web-based collaboration use yet other systems.
Network Consolidation: The Internet
Voice over IP
- Use signaling concepts from the telephone industry—H.323, MGCP, MEGACO/H.248.
- Use control concepts from the telephone industry—central control and softswitches.
- Use the Internet-centric protocol—Session Initiation Protocol (SIP), the topic of this book.
Table of contents
- Cover
- Contents
- Title
- Copyright
- Dedication
- Foreword
- Acknowledgments
- Introduction
- Chapter 1: Introduction
- Chapter 2: Internet Communications Enabled by SIP
- Chapter 3: Architectural Principles of the Internet
- Chapter 4: DNS and ENUM
- Chapter 5: Real-Time Internet Multimedia
- Chapter 6: SIP Overview
- Chapter 7: SIP Service Creation
- Chapter 8: User Preferences
- Chapter 9: SIP Security
- Chapter 10: NAT and Firewall Traversal
- Chapter 11: SIP Telephony
- Chapter 12: Voicemail and Universal Messaging
- Chapter 13: Presence and Instant Messaging
- Chapter 14: SIP Conferencing
- Chapter 15: SIP Application Level Mobility
- Chapter 16: Emergency and Preemption Communication Services
- Chapter 17: Accessibility for the Disabled
- Chapter 18: Quality of Service for Real-Time Internet Communications
- Chapter 19: SIP Component Services
- Chapter 20: Peer-to-Peer SIP
- Chapter 21: Conclusions and Future Directions
- Index