
M2M Communications
A Systems Approach
- English
- ePUB (mobile friendly)
- Available on iOS & Android
M2M Communications
A Systems Approach
About this book
A comprehensive introduction to M2M Standards and systems architecture, from concept to implementation
Focusing on the latest technological developments, M2M Communications: A Systems Approach is an advanced introduction to this important and rapidly evolving topic. It provides a systems perspective on machine-to-machine services and the major telecommunications relevant technologies. It provides a focus on the latest standards currently in progress by ETSI and 3GPP, the leading standards entities in telecommunication networks and solutions. The structure of the book is inspired by ongoing standards developments and uses a systems-based approach for describing the problems which may be encountered when considering M2M, as well as offering proposed solutions from the latest developments in industry and standardization.
The authors provide comprehensive technical information on M2M architecture, protocols and applications, especially examining M2M service architecture, access and core network optimizations, and M2M area networks technologies. It also considers dominant M2M application domains such as Smart Metering, Smart Grid, and eHealth. Aimed as an advanced introduction to this complex technical field, the book will provide an essential end-to-end overview of M2M for professionals working in the industry and advanced students.
Key features:
- First technical book emerging from a standards perspective to respond to this highly specific technology/business segment
- Covers the main challenges facing the M2M industry today, and proposes early roll-out scenarios and potential optimization solutions
- Examines the system level architecture and clearly defines the methodology and interfaces to be considered
- Includes important information presented in a logical manner essential for any engineer or business manager involved in the field of M2M and Internet of Things
- Provides a cross-over between vertical and horizontal M2M concepts and a possible evolution path between the two
- Written by experts involved at the cutting edge of M2M developments
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1.1 What is M2M?
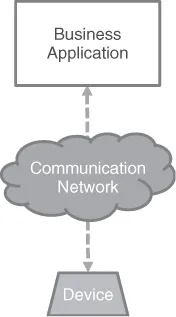
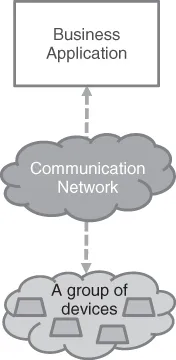
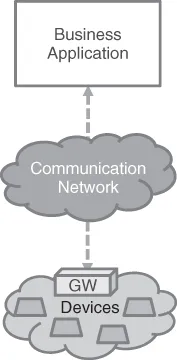
- Multitude – This is the most advocated change brought about by M2M. It is generally agreed that the number of “devices” connected in M2M relationships will soon largely exceed the sum of all those that directly interact with humans (e.g., mobile phones, PCs, tablets, etc.). An increased order of magnitude in the number of devices results in significantly more pressure on applications architectures, as well as on network load, creating in particular scalability problems on systems that have been designed to accommodate fewer “actors” and far greater levels and types of traffic. One of the early instances of such problems is the impact of M2M devices on mobile networks that have not been designed with this set of devices in mind and are in the process of being adapted to allow large numbers of devices with non-standard usage patterns (this will be discussed later in this chapter).
- Variety – There are already a particularly large number of documented possible use cases for M2M that apply to a variety of contexts and business domains. The initial implementations of M2M applications have already led to the emergence of a large variety of devices with extremely diverse requirements in terms of data exchange rate, form factor, computing, or communication capabilities. One result of the wide variety is heterogeneity, which is in itself a major challenge to interoperability. This can be a major obstacle to the generalization of M2M. It is also a challenge for the frameworks on which M2M applications have to be built, in order to define and develop common-enabling capabilities.
- Invisibility – This is a strong requirement in many M2M applications: the devices have to routinely deliver their service with very little or no human control. In particular, this is preventing humans from correcting mistakes (and also from creating new ones). As a result, device management more than ever becomes a key part of service and network management and needs to be integrated seamlessly.
- Criticality – Some devices are life-savers, such as in the field of eHealth (blood captors, fall detectors, etc.). Some are key elements of life-critical infrastructures, such as voltage or phase detectors, breakers, etc, in the Smart Grid. Their usage places stringent requirements upon latency or reliability, which may challenge or exceed the capabilities of today's networks.
- Intrusiveness – Many new M2M devices are designed with the explicit intention to “better manage” some of the systems that deal with the end-users' well-being, health, etc. Examples are the eHealth devices already mentioned, smart meters for measuring and/or controlling electrical consumption in the home, etc. This in turn leads to issues of privacy. In essence, this is not a new issue for ICT systems but it is likely that privacy may present a major obstacle in the deployment of M2M systems. This may occur when the large deployment of smart meters demands prior arbitration between the rights of end-users to privacy and the needs of energy distributors to better shape household energy consumption.
- limited in functionality – Most M2M devices have computational capabilities several orders of magnitude below what is currently present in a modern portable computer or a smart phone. In particular, devices may be lack remote software update capabilities. One of the main reasons for this design choice is cost, often because the business model requires very competitively priced devices (e.g., smart meters in many cases). Limited functionality also results from rational decisions based on the nature of the exchanged information and performable actions: most sensors are not meant to be talkative and operationally complex.
- low-powered – Although many M2M devices are connected to a power network, many of them have to be powered differently (often on batteries) for a variety of reasons. For instance, a large number of them are, or will be, located outdoors and cannot be easily connected to a power supply (e.g., industrial process sensors, water meters, roadside captors). This will reduce the amount of interaction between such devices and the M2M applications (e.g., in the frequency and quantity of information exchanged).
- embedded – Many devices are, and will be, deployed in systems with specific (hostile, secure) operating conditions that will make them difficult to change without a significant impact on the system itself. Examples are systems embedded in buildings or in cars that are hard to replace (e.g., when they are soldered to the car engine, as is the case with some M2M devices).
- here to stay – Last but not least, many of the new M2M devices are and will be deployed in non-ICT applications with very different lifetime expectancy. The rate of equipment change in many potential M2M business domains may be lower than in the ICT industry. This may be linked to cost issues due to different business models (e.g., no subsidization of devices by the operators), to the fact that they are embedded, but also to the complexity of evolution of the industrial process in which the device is operating (e.g., criticality of the service makes changing equipment in a electricity network very difficult, which leads to long life cycle of equipment in the field).
- IoT is dealing with Things or Objects that may not be in an M2M relationship with an ICT system. An example of this is in the supermarket where radio-frequency identification (RFID) “tagged” objects are offered to the customer. These objects are “passive” and have no direct means with which to communicate “upstream” with the M2M application but they can be “read” by an M2M scanner which will be able to consolidate the bill, as well as making additional purchase recommendations to the customer. From this perspective, the M2M scanner is the “end point” of the M2M relationship.
- There are M2M relationships initiated by devices that are to be seen as direct human–machine...
Table of contents
- Cover
- Title Page
- Copyright
- Foreword
- List of Contributors
- List of Acronyms
- Chapter 1: Introduction to M2M
- Part One: M2M Current Landscape
- Part Two: M2M Architecture and Protocols
- Part Three: Book Conclusions and Future Vision
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app