
Improving your Penetration Testing Skills
Strengthen your defense against web attacks with Kali Linux and Metasploit
Gilberto Najera-Gutierrez, Juned Ahmed Ansari, Daniel Teixeira, Abhinav Singh
- 712 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Improving your Penetration Testing Skills
Strengthen your defense against web attacks with Kali Linux and Metasploit
Gilberto Najera-Gutierrez, Juned Ahmed Ansari, Daniel Teixeira, Abhinav Singh
About This Book
Evade antiviruses and bypass firewalls with the most widely used penetration testing frameworks
Key Features
- Gain insights into the latest antivirus evasion techniques
- Set up a complete pentesting environment using Metasploit and virtual machines
- Discover a variety of tools and techniques that can be used with Kali Linux
Book Description
Penetration testing or ethical hacking is a legal and foolproof way to identify vulnerabilities in your system. With thorough penetration testing, you can secure your system against the majority of threats.
This Learning Path starts with an in-depth explanation of what hacking and penetration testing is. You'll gain a deep understanding of classical SQL and command injection flaws, and discover ways to exploit these flaws to secure your system. You'll also learn how to create and customize payloads to evade antivirus software and bypass an organization's defenses. Whether it's exploiting server vulnerabilities and attacking client systems, or compromising mobile phones and installing backdoors, this Learning Path will guide you through all this and more to improve your defense against online attacks.
By the end of this Learning Path, you'll have the knowledge and skills you need to invade a system and identify all its vulnerabilities.
This Learning Path includes content from the following Packt products:
- Web Penetration Testing with Kali Linux - Third Edition by Juned Ahmed Ansari and Gilberto Najera-Gutierrez
- Metasploit Penetration Testing Cookbook - Third Edition by Abhinav Singh, Monika Agarwal, et al
What you will learn
- Build and analyze Metasploit modules in Ruby
- Integrate Metasploit with other penetration testing tools
- Use server-side attacks to detect vulnerabilities in web servers and their applications
- Explore automated attacks such as fuzzing web applications
- Identify the difference between hacking a web application and network hacking
- Deploy Metasploit with the Penetration Testing Execution Standard (PTES)
- Use MSFvenom to generate payloads and backdoor files, and create shellcode
Who this book is for
This Learning Path is designed for security professionals, web programmers, and pentesters who want to learn vulnerability exploitation and make the most of the Metasploit framework. Some understanding of penetration testing and Metasploit is required, but basic system administration skills and the ability to read code are a must.
Frequently asked questions
Information
Meterpreter
- Understanding the Meterpreter core commands
- Understanding the Meterpreter filesystem commands
- Understanding the Meterpreter networking commands
- Understanding the Meterpreter system commands
- Setting up multiple communication channels with the target
- Meterpreter anti-forensics
- The getdesktop and keystroke sniffing
- Using a scraper Meterpreter script
- Scraping the system with winenum
- Automation with AutoRunScript
- Meterpreter resource scripts
- Meterpreter timeout control
- Meterpreter sleep control
- Meterpreter transports
- Interacting with the registry
- Load framework plugins
- Meterpreter API and mixins
- Railgun—converting Ruby into a weapon
- Adding DLL and function definitions to Railgun
- Injecting the VNC server remotely
- Enabling Remote Desktop
Introduction
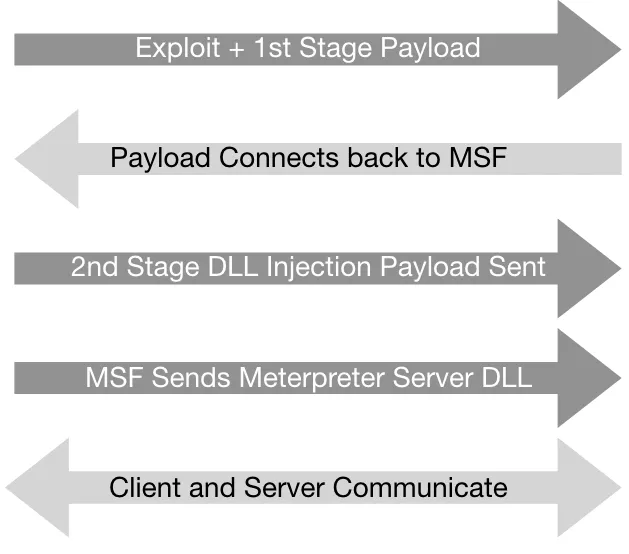
- It works in context with the exploited process, so it doesn't create a new process
- It can migrate easily among processes
- It resides completely in memory, so it writes nothing to disk
- It uses encrypted communications
- It uses a channelized communication system so that we can work with several channels at a time
- It provides a platform to write extensions quickly and easily
Understanding the Meterpreter core commands
Getting ready
How to do it...
- The Metasploit Framework comes packed with several resource scripts that have been contributed to by the community, which you can find at /usr/share/metasploit-framework/scripts/resource/ in your Kali Linux machine:
root@kali:~# ls /usr/share/metasploit-framework/scripts/resource/
auto_brute.rc fileformat_generator.rc
auto_cred_checker.rc mssql_brute.rc
auto_pass_the_hash.rc multi_post.rc
auto_win32_multihandler.rc nessus_vulns_cleaner.rc
autocrawler.rc oracle_login.rc
autoexploit.rc oracle_sids.rc
bap_all.rc oracle_tns.rc
bap_dryrun_only.rc port_cleaner.rc
bap_firefox_only.rc portscan.rc
bap_flash_only.rc run_all_post.rc
bap_ie_only.rc wmap_autotest.rc
basic_discovery.rc
- To create our own resource scripts, we simply need to execute the module and then use the makerc command to create a re...