
eBook - ePub
Chinese Intelligence Operations
Espionage Damage Assessment Branch, US Defence Intelligence Agency
- 190 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Chinese Intelligence Operations
Espionage Damage Assessment Branch, US Defence Intelligence Agency
About this book
Nicholas Eftimiades examines the infiltration of Chinese espionage agents into foreign governments and private businesses. He specifically addresses the human source in intelligence operations, and how these tactics fit into the conduct of internal and foreigh affairs in China.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Chinese Intelligence Operations by Nicholas Eftimiades in PDF and/or ePUB format, as well as other popular books in History & Military & Maritime History. We have over one million books available in our catalogue for you to explore.
Information
Part One
Introduction
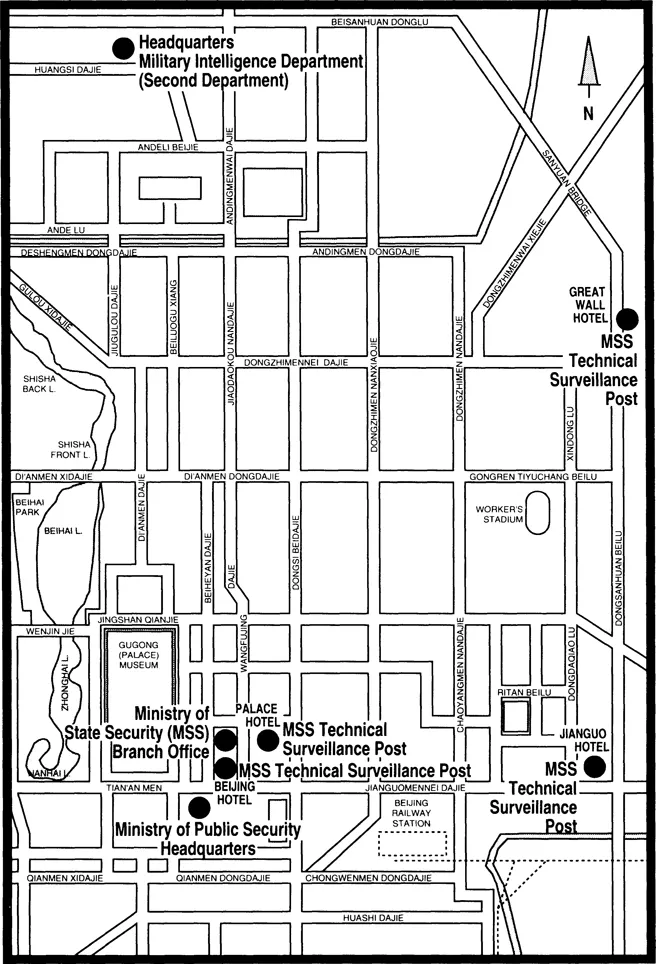
Locations of intelligence facilities in Beijing
DEBORAH A. EFTIMIADES
Chapter One
China’s Use of Intelligence
Chinese intelligence operations and methods are relatively new to the Western world. They are not, however, new in themselves. The practice of espionage in China dates back to at least the fifth century B.C., when the proper employment of spies was detailed in a military manual, Sun Tzu Bing Fa (Sun Tzu’s Art of War). Since that time, The Art of War has been revered as a classic work on the fundamentals of military tactics and strategy. Sun Tzu put a high value on accurate and timely intelligence in daily affairs of state and in support of military campaigns. He attributed a commander’s foreknowledge to the proper employment of espionage agents, saying that “no one in the armed forces is treated as familiarly as spies and no one is given rewards as rich as those given to spies.”1
Sun Tzu was not alone in his appreciation of accurate and timely intelligence in support of diplomatic and military campaigns. China’s military history is replete with examples of using espionage to attain policy and military objectives. In the book Chinese Ways in Warfare, Frank A. Kierman, Jr., describes ancient Chinese battle narratives such as the Tso-Chuan (Tradition of Tso) of the Eastern Chou period (ca. 770—403 B.C.) and the Shih Chi, an account of Chinese history up to the first century B.C. These narratives are divided into a sequence of preparatory and operational phases, and among the preparatory phases is the collection and analysis of military and relevant diplomatic intelligence information.
It is interesting to note that even in ancient times China had developed and documented an understanding of intelligence needs and practices for military and diplomatic activities. At that time, information requirements were relatively simple: enemy unit size, weaponry, location, and morale; biographical information on enemy com-manders; terrain features; and the intentions of neutral and allied forces. In addition, the Tso-Chuan describes intelligence operations employed not only to collect information but also to deceive the opposition and deny them militarily significant information.2
Today the People’s Republic of China’s intelligence needs are far more numerous and complicated than those of ancient times. Yet today’s policymakers show the same appreciation for the value of foreknowledge and the proper application of espionage activities in support of the affairs of state. The PRC’s intelligence apparatus is more than just a support department for policymakers. It is inextricably linked to the foreign policy decision-making process and internal methods of economic development and political control.
For centuries intelligence services have served their constituents by collecting information about friends and adversaries alike. Indeed, the history of the practice of intelligence operations is ancient and rich. Espionage has been described by insiders as “the world’s second oldest profession.” To comprehend the structure, roles, and nature of China’s intelligence system it is first necessary to understand that such activities do not just happen by themselves. That is, intelligence activities are tied to a government’s decision-making processes. Just like diplomatic or military campaigns, intelligence operations in the modern world require careful planning, command and control, communication, and tremendous financial resources. These elements must be organized in some way to accomplish their respective tasks.
Intelligence agencies worldwide share the same overall goal: to provide accurate and timely intelligence to their consumers. To do so they collect raw information from a variety of human and technical sources. They must then collate and analyze that data to separate fact from fiction and make judgments about a variety of past, current, and future events. The completed analytical product, intelligence, is then disseminated to the consumer, whose information requirement started the process. That person or group is then in a position to ask for additional analysis or to implement policy based on the intelligence received. The entire process is known as the intelligence cycle (see fig. 1).
Current world events show no indications of a decrease in the use of espionage to support national policy objectives. Even after the dissolution of the Warsaw Pact, the disintegration of the Soviet Union, and the subsequent reduction in bipolar tensions, intelligence services remain active—and in some cases their level of operations has increased. Global or regional changes in political, military, and economic conditions do not diminish the need for accurate intelligence. On the contrary, a nation’s need for accurate and timely intelligence corresponds to the level of global or regional instability and the scope of its interests worldwide.
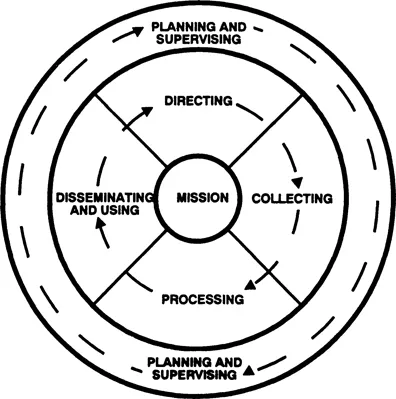
1. The intelligence cycle
From the end of World War II until recently the Soviet Union and its allies were considered the primary military threat to the United States’ global interests. As a result, American intelligence and counter-intelligence agencies gave a great deal of attention to the espionage capabilities of the Warsaw Pact nations. Considerably less effort was dedicated to identifying and neutralizing the espionage activities of nations such as China that presented no comparable military threat. Although it has the largest armed forces in the world, the PRC has never developed (and is not likely to develop in the near future) the force projection capability needed to invade any nation outside Asia. For this reason its espionage operations go largely unchecked by U.S. officials and policymakers. The PRC does, however, aggressively conduct espionage against the United States and a number of other industrialized nations.
The shortsighted allocation of America’s intelligence resources has allowed the Chinese espionage apparatus to operate outside the focus of mainstream counterintelligence concerns. As a result the United States and other Western industrialized nations are woefully unprepared to protect their national assets from Beijing’s espionage efforts. China’s intelligence gathering operations have increased to the point where agencies with counterintelligence responsibilities are overwhelmed by the sheer number of cases. Not until recently has the U.S. intelligence community recognized the magnitude of China’s efforts. Harry Godfrey III, chief of FBI counterintelligence, observed that
if we are talking about violations of U.S. law, the Chinese are surpassing the Russians. We know they are running operations here. We have seen cases where they have encouraged people to apply to the CIA, the FBI, Naval Investigative Service, and other Defense agencies. They have also attempted to recruit people at our [nuclear] research facilities at Los Alamos and at Lawrence Livermore.3
Like other regional or global powers, the leadership of the PRC bases its policies and actions on its military, political, and economic self-interests. Many of those interests involve reaping financial and technological benefits from close commercial ties with advanced industrialized nations. In recent years, China’s human rights policies have alienated some of its former friends among the Western democracies and, in the case of the United States, restricted its access to some categories of advanced technology. China’s intelligence services are therefore required to play a greater role in supporting national policy objectives by targeting and exploiting the technological, economic, political, and military infrastructures of the developed nations.
Industrial espionage and illegal technology transfers are only the most publicized aspects of China’s intelligence activities. These types of operations are likely to receive greater emphasis in the future as China’s foreign intelligence services continue to target the U.S. industrial sector. High-tech information—used to develop China’s ailing civilian and military industrial sectors—is of particular importance to Beijing. As a result, the PRC’s intelligence operations against the United States have become so intrusive that senior U.S. law enforcement officials have publicly identified China as “the most active foreign power engaged in the illegal acquisition of American technol-ogy.”4
Espionage and other intelligence activities rarely require the proverbial cloak and dagger, but they are far more complicated than mere theft of a foreign government’s classified materials. Espionage is an orchestrated, all-encompassing attempt to extract information from multiple levels of society. At the national level, desirable intelligence falls into several categories. Nations routinely collect and use volumes of data on foreign political situations, leadership figures, military force structures and capabilities, science and technology issues, economic conditions, and sociological factors. Each of these categories should be considered separately to piece together the true role of intelligence collection and analysis as practiced by the PRC:
Foreign political situations—All the affairs of state that determine a nation’s future actions domestically and internationally.
Leadership figures—The histories and personalities of those individuals (military and civilian) who influence the affairs of state, now or in the future.
Military force structures and capabilities—Information such as the table of organization and equipment (TOE) for units of the armed forces; the locations, strengths, and missions of those units; and their ability to wage war.
Science and technology issues—The overall level of sophistication in civilian and military sectors as well as a society’s ability to develop and use technology.
Economic conditions—Strengths and weaknesses of a nation’s economy and how economic factors might influence domestic and foreign policies.
Sociological factors—Religious, cultural, and customary practices of a society and how those factors might affect its actions and decisions. (An example of this type of intelligence is the study of Vietnamese burial practices that was used to locate the remains of missing soldiers.)
In democratic societies much of this information is available in the open press. Indeed, the downfall of communism in eastern Europe and the former Soviet Union has unleashed a torrent of published information, most of it new to the West. In addition, a great deal of usable information can be gathered simply by watching a society function on a daily basis. General attitudes of the populace, political personalities and trends, and economic conditions are all topics addressed daily in any major Western newspaper. Intelligence agencies therefore spend considerable time and effort identifying, collecting, translating, and analyzing information from published open sources.
Information that cannot be found in open sources must be collected secretly via technical means: satellite imagery, communications intercepts, and the use of recruited agents. Clandestine intelligence operations are directed with equal vigilance against hard targets such as government political and military institutions and soft targets such as the industrial and academic sectors. The latter are referred to as “soft” because persons associated with these institutions usually lack knowledge of the operational methods of espionage and are therefore vulnerable to foreign penetration and exploitation.
My goal in this book is to identify China’s national intelligence structure, objectives, and collection operations. I focus primarily on human-source intelligence (HUMINT) operations, which I analyze to determine China’s intelligence strategies, methods, and capabilities. In addition, I also give some attention to the PRC’s intelligence analysis community by identifying the roles and organization of major departments and agencies. For readers unfamiliar with intelligence terminology, a glossary of frequently used words and acronyms is provided.
Chapter Two
Framework for Analysis
For the purposes of this study, human-source intelligence operations can be divided into three broad categories: overt, clandestine, and covert action. Overt intelligence activities are those collection and analysis functions that can be identified and attributed to a specific country. For example, when military attachés attend another country’s military exercises they are engaged in overt intelligence collection. The host government expects that the attachés will report the event and any relevant information from it to their own governments. This information might include unit strengths, proficiency, procedures, equipment, tactics, and biographical data on commanders. In turn, the host government will attempt to gather information from the attending attachés—and they will do the same among themselves in the course of normal conversation. This type of activity, and other forms of direct observation and contact (e.g., a diplomat holding discussions with local inhabitants or government officials), is generally considered overt collection.
Clandestine activities are intelligence collection operations that, even if detected, cannot be attributed to a specific nation. These operations usually involve the recruitment of spies and are designed to hide the involvement of the nation that is behind them. For example, one might suspect clandestine collection activities if classified or restricted equipment was discovered in the hands of a third world nation that did not have the technical capability to produce it. One can assume that the equipment was stolen, although the thief and the exact method remain unknown.
Covert action operations are not intelligence collection activities per se. Instead, they are efforts such as economic and military assistance programs that are designed to manipulate a foreign government or other entity. Covert action operations can be divided into four general categories: political, economic, paramilitary, and those that feature disinformation.
All countries need various types of information to ensure their own security. And while there are substantial differences in national objectives, doctrines, and capabilities, the methods employed to collect and analyze information are virtually identical worldwide. This results in substantial similarities in the structures of intelligence services. This is not to say that every nation’s intelligence units are organized along the same lines. However, the peculiar and generally clandestine nature of intelligence activities calls for certain operational and support services, and the departments that provide these essential services have a logical place in all organizations engaged in such activities.
Identifying the common administrative and functional bureaus within China’s government agencies provides some insight into the structure of its civilian and military intelligence services. Governments generally create similar departments in each interlocking agency in order to achieve uniformity and to facilitate communication within the system. Like all government bureaucracies, the Chinese intelligence services must have a defined organizational structure to accomplish their various missions. In his study Cadres, Bureaucracy, and Political Power in China, noted sinologist A. Doak Barnett observed that China’s government ministries have certain standard departments.1 The hierarchical structure of authority in the PRC dictates that the roles and responsibilities of these common departments will be the same in each ministry.
Another source of information on the structure of China’s intelligence apparatus is public exposure of clandestine operations. For the nonspecialist, analysis of publicly available information carries with it some dangers. Media accounts of a particular event can be tainted by a variety of outside influences, intentionally or inadvertently. First, a reporter’s assessment of the meaning of the event may be inaccurate. For example, the publicly announced arrest of a spy by country X may mean very little to the reporter. But to the world’s intelligence professionals it means that an espionage network set up by country Y has been compromised, along with the clandestine communic...
Table of contents
- Cover
- Half Title
- Title
- Copyright
- Dedication
- Contents
- Foreword
- Acknowledgments
- Glossary
- PART ONE Introduction
- PART TWO Ministry of State Security
- PART THREE China’s Intelligence Community
- PART FOUR Conclusion
- Appendixes
- Notes
- Select Bibliography
- Index
- About the Author