
eBook - ePub
Botnets
Architectures, Countermeasures, and Challenges
- 426 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Botnets
Architectures, Countermeasures, and Challenges
About this book
This book provides solid, state-of-the-art contributions from both scientists and practitioners working on botnet detection and analysis, including botnet economics. It presents original theoretical and empirical chapters dealing with both offensive and defensive aspects in this field. Chapters address fundamental theory, current trends and techniques for evading detection, as well as practical experiences concerning detection and defensive strategies for the botnet ecosystem, and include surveys, simulations, practical results, and case studies.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Botnet Architectures
A State-of-the-Art Review
Contents
1.1 Introduction
1.2 Botnets main characteristics
1.2.1 Overview
1.2.2 Characterizing botnets
1.2.2.1 The botnet size
1.2.2.2 Geographical Distribution of Botnets
1.2.2.3 Spatial-Temporal Correlation and Similarity
1.3 Centralized Botnets
1.3.1 Case study: IRC-based botnets
1.4 P2P Botnets
1.4.1 Case study: ZeroAccess P2P botnet
1.5 Mobile Botnets
1.5.1 Examples of mobile botnets
1.5.1.1 SMS-based mobile botnets
1.5.1.2 Cloud-based push-styled mobile botnets
1.6 IoT Botnets
1.7 Social Botnets
1.7.1 Operation
1.8 Conclusion
1.1 Introduction
In recent years, cybercrimes that are associated with botnets have been considered a major threat to the Internet and technology. A botnet consists of a number of infected hosts and receive commands from a botmaster [1]. The botnet is basically formed by installing bots on vulnerable computers. Bots are software programs that perform actions upon receiving commands from users or programs. Bots usually stay in a passive state until they receive commands from the botmaster (a hacker). Bots are designed to establish and utilize available communication channels that enable them of receiving commands, executing commands, and periodically reporting data back to the botmaster. Reports include their status and statistical information. Furthermore, bots are usually programmed to keep up to date with the latest bot version. The botmaster maintains control over the botnet through the command and control (C&C) communication channel that represents the core of the botnet.
Generally, bots try to exploit software vulnerabilities that allow malicious programs to infect computing systems. Examples of software vulnerabilities are buffer overflow, backdoor installations, software bugs, and unsecured memory management mechanisms. Releasing bot codes to the public results in spreading of many variants of the bot within a short time [2–5]. Making the bot’s source code available makes it easier for hackers to extend it and develop more sophisticated codes to serve their objectives. For example, Agobot is structured in a modular design, which makes it attractive for botnet’s developers. According to [2], there exist different types of bots and different variants of each type in today’s digital computing world. Hackers are always interested in discovering new software vulnerabilities and in improving their bots to higher level of sophistication. Hence, it is expected that more bots will evolve and pose serious threats. This urges companies and researchers to develop efficient countermeasure methods to stop the cybercrimes that are posed by botnets. Botnets represent a major contributor to malicious traffic in today’s Internet [1].
Moreover, the botnet attack landscape has increased tremendously in recent years because of new highly sophisticated versions of botnets. The development of botnet architectures and types are driven by hackers’ interest, the expansion of the Internet, and the Internet technology development. Organized hacking groups, organizations, and cyber criminals are increasingly threatening businesses, where about one-third of the world companies have experienced the threat of cybercrimes [6]. Botnets are being used extensively for malware distribution to target banking sectors [7]. Botnets provide hackers with a platform for personal profit and financial gain through extortion, ransom-ware, and cryptocurrency. Cyberattacks are also targeting critical Internet infrastructure and cyber-physical systems, including smart grids, nuclear plants, and transportation systems. In addition, botnets are expected to take a role in future cyber wars. With the tremendous expansion of the Internet, botnets are no longer limited to infect only PCs and laptops. Several types of botnets have appeared in recent years such as smartphone, Internet of Things (IoT), and social botnets. The enormous growth of botnets enabled hackers to use them for different forms of malicious activity including distributed denial-of-service (DDoS) attacks, email spam, click-fraud, and identity theft. In this context, botnets can be viewed as an attack infrastructure that is used to launch several types of cybercrimes. This chapter is focused on the emerging and predominant threat of botnets. In Section 1.2, we provide a detailed description of botnets and we discuss their main characteristics. Section 1.3 discusses centralized botnets. Section 1.4 explains peer-to-peer (P2P) botnets. Section 1.5 presents mobile botnets. Section 1.6 provides a description on IoT-based botnets. Social botnets are presented in Section 1.7. Finally, the conclusion is presented in Section 1.8.
1.2 Botnets Main Characteristics
A botnet can be viewed as an attack infrastructure that consists of compromised hosts that are connected together to form a network using a variety of application layer protocols, such as IRC, HTTP, email, and P2P protocols. In this section, we discuss botnet life cycle, explain their malicious usage, discuss their main characteristics, and illustrate different approaches that are used to obtain insightful information about botnets.
1.2.1 Overview
A botnet’s life time consists of three main stages as follows.
Stage 1—recruitment stage: The botnet formation starts by recruiting as many vulnerable machines as possible to become part of a botnet. This is done through infecting machines with the bot code using different mechanisms. One of the mechanisms adopts traditional worm propagation techniques to spread botnet malware [8,9]. This approach does not require any user intervention. An infected machine has the ability to search for other vulnerable machines on the Internet through active scanning for holes of known vulnerabilities. There are several mechanisms to recruit vulnerable machines in a passive manner where user interventions are required. Social engineering is a powerful mechanism that is used by botmasters to convince end users to download bot binaries [10,11]. This is usually achieved by sending out massive phishing campaigns through email and social networks (e.g., Twitter, Facebook), where a user is tricked to click on a malicious link that results in downloading of a bot binary [12,13]. In other cases, the malware may spread as an email attachment or by tricking the user to visit websites that have active content such as JavaScripts or ActiveX controls. When a user visits a website that contains malicious active contents, the malware is installed automatically. It is also possible to spread botnets’ binaries through physical media (e.g., USB flash drive), where the malware is usually in the form of an executable and starts running as soon as the user double click on it. Physical media infection aims to compromise machines with private IP address that are unreachable directly from the Internet (e.g., behind a NAT box).
Stage 2—C&C stage: The botmaster maintains a control over the infected machines (bots) through a C&C channel. The architecture of the botnet depends on the implementation of the C&C channel. In centralized botnets, the botmaster controls its botnet through a central server known as the C&C server. In P2P botnets, there is no central server between the botmaster and botnet machines. Hence, the botmaster communicates directly with a small subset of botnet machines. These machines in the subset serve as mailboxes between the botmaster and other botnet machines. The machines are located using the inherent features of the P2P protocol that is used to implement the botnet. More details of centralized and P2P botnets are provided in Section 1.3 and Section 1.4. The communication style between the botmaster and the bots can be a Push or a Pull style. In the Push style, commands are sent directly to the bots. In the Pull style, bots (infected machines) keep checking for new commands periodically [14]. The two communication styles are illustrated in Figure 1.1.
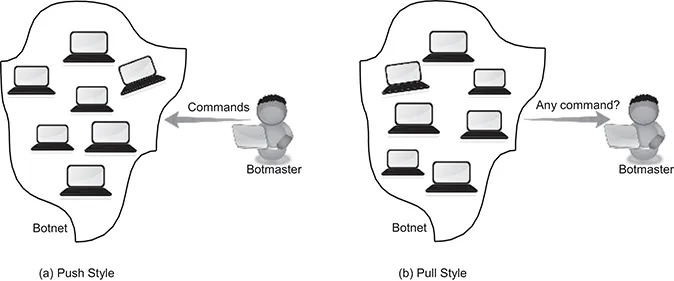
Figure 1.1 Botnet communication styles: (a) Push style (b) Pull style.
Stage 3—botnet activity stage: The botnet activity represents the set of actions and attacks (e.g., DDoS, scanning, etc.) that are performed by bots in response to commands that are issued by the botmaster [15–17]. A compromised host’s bandwidth is an important information that indicates the host’s capability in launching attacks, especially DDoS. Hence, bots estimates the host’s bandwidth by sending data to many servers. Figure 1.2 shows an example of an IRC-based botnet activity in response to a set of commands that were issued by the botmaster. The figure shows the interaction between a botmaster (nickname seed) and one of the bots (nickname vofm) in an IRC chat channel (#nes554). This is a typical example of a push style communication where the botmaster issues certain commands that are sent to the bot directly. For example, the command
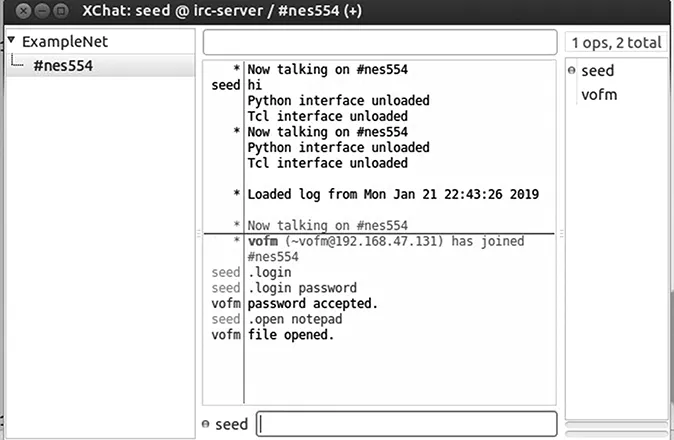
Figure 1.2 Example of an IRC-based botnet activity.
.open notepad
instructs the bot to run notepad.exe. Running notepad application is just an example that shows the capabilities of this botnet. Botmasters instruct bots to run malware binaries after downloading them from a given server. Other example involves instructing the bot to perform a DNS query for a given host name and return the result to the botmaster.
Understanding botnets and their operational aspects require us to investigate different bots to reveal their malicious intents [2]. For example, P. Barford et al. studied the source codebases for the four major botnets Agobot, SDBot, SpyBot, and GT Bot [18]. Analyzing bots’ source code or running a botnet malware instance in a sandbox are efficient methods to identify botnet features and capabilities including the C&C mechanisms. In general, botnets are considered as major sources of different types of attacks and malicious activities in the Internet. This includes the following:
■ DDoS attacks: Botnets are used to launch several forms/types of DDoS attacks, such as application layer attacks (e.g., HTTP-based attacks), SYN flooding, and DNS amplification attacks. Bots are instructed to overwhelm the target system with a high volume of traffic rate (e.g., HTTP requests, SYN packets, and DNS requests).
■ Email spam campaigns: This belongs to sending a large amount of spam emails, which results in a traffic that decreases the signal-to-noise measure [19]. Email spammers usually use botnets for massive email spam campaigns to advertise pharmaceutical products, adult content, and malware distribution. An email spam template is distributed along with an email recipients’ list to the workers (bots). The bots are then instructed to send spam with the contents that are specified in advance by the spammer.
■ Identity theft: Botmasters have the ability to collect sensitive information (such as email accounts, banking accounts, and credit card numbers) from the bot machines.
■ Cryptocurrency: The computing power of the machines that belong to a botnet can be utilized by botmasters to perform cryptocurrency mining to obtain bitcoins in an illegal way.
■ Click-Fraud: Whereby a botmaster generates bogus clicks for online advertisements (usually utilizing the field of the HTTP request header) that mimic legitimate request patterns, which results in large sums of money to be paid by the advertisers [20]. Online advertisement is becoming ...
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Table of Contents
- Preface
- About the Editors
- Contributors
- 1. Botnet Architectures: A State-of-the-Art Review
- 2. IoT Botnets: The Journey So Far and the Road Ahead
- 3. IoT Botnet Traits and Techniques: A View of the State of the Art
- 4. Advanced Information Hiding Techniques for Modern Botnets
- 5. Steganography Techniques for Command and Control (C2) Channels
- 6. Blockchain-Based Botnets for Command-and-Control Resilience
- 7. Detecting Botnets and Unknown Network Attacks in Big Traffic Data
- 8. Domain Generation Algorithm Detection Techniques through Network Analysis and Machine Learning
- 9. Identifying IoT-Based Botnets: A Microservice Architecture for IoT Management and Security
- 10. Understanding and Detecting Social Botnet
- 11. Use of Botnets for Mining Cryptocurrencies
- 12. Time to Diverge the Botnet Revenues from Criminal Wallet?
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Botnets by Georgios Kambourakis, Marios Anagnostopoulos, Weizhi Meng, Peng Zhou, Georgios Kambourakis,Marios Anagnostopoulos,Weizhi Meng,Peng Zhou in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.