
- 160 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Practical Data Security
About this book
First published in 1993, this volume emerged in response to the genesis of the Internet and provides early considerations on issues including computer viruses, cyber security and network encryption management, with a particular focus on applying risk analysis to the data security of financial institutions. With the stage set by the UK Data Protection Act of 1984 and the Computer Misuse Act of 1990, this volume provides a series of useful contributions for large companies and home PCs and provides a clear introduction setting out the context and the relevant terminology.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1
An Organisation for Security in a Major Company
1.1 Background
Some years ago our main concerns within the company were with the investigation and detection of crime, with national security and to a lesser extent commercial security.
On becoming a commercial concern instead of a public utility, it became clear that proactive working had many more benefits than the reactive style. This has led to the introduction of units responsible for crime prevention, advice and electronic security. Over the years we have changed into our present organisation which has been modelled to meet the business’s needs, and in 1991 a major reorganisation took place to formalise the changes.
1.2 The Business Justification
The motivation for good security comes from the concern for quality, to save on the costs of security failures, and good business practice.
The most easily identifiable motivating reason is that of cost. Many security failures will inflict a direct cost on the customer, network or system, for example by gaining the power to make free calls or access to services, or by the theft of physical assets or goods.
Another area of concern is the theft of information which may lead to a commercial advantage to a competitor, such as the knowledge of new techniques, intellectual property, or marketing information from our customer base. The most important values are integrity, availability, and confidentiality of the information.
Of concern to the Company are some of the indirect consequential losses resulting from a security failure. These costs are harder to quantify and so are not often taken into account when deciding a security strategy. They include:
- investigation time, that is the time spent by experts to determine the scope of and put right any failure;
- loss of time for people, and the consequential problems of people being unable to fulfil their normal jobs;
- data destruction or lack of data integrity where it is impossible to recover data;
- legal implications, where external legal obligations are placed on us, such as the Data Protection Act, our licence conditions, and the Financial Services Act.
Other reasons that may lead to security being considered are:
- loss of customer confidence, where a security failure causes a customer to look elsewhere for the service; and
- indirect losses such as contracts and similar penalties, where a penalty results for late delivery or similar obligations under the contract.
1.3 Organisation of the Security within the Company
A high visibility of the importance of security is necessary within a company. It is important that all people at senior levels are aware of the problems and risks, and also behave and act in a way that strengthens the message.
Within the Company the security unit covers all aspects of security, and reports direct to the Company Secretary who is also a Board member.
The Director of Security is sometimes concerned with different security areas such as investigation and detection, national security, commercial security and estate security. The Director of Security manages by means of a coordinating committee drawn from all Company business divisions (see Figure 1).
Each business division has on its board a member, part of whose responsibility and job description is for security within that business division. Reporting directly to that board member within that business division is a Security Coordinator, who has suitable people and resources to carry out cost effective security within that business division area.
There is naturally a variation across business divisions depending on the activities which they are indulging in; for example there is a greater emphasis on computer security within our Information Technology divisions, and on network security within the Worldwide Networks division.
The Investigation unit carries out detective work to help combat crimes committed against the company.
The Commercial Security unit divides between three effective units:
- the first sets the policy in the areas of electronic systems, information, and physical security throughout the whole of the Company;
- the second is concerned with checking by means of compliance and review work so that new threats or risks are fed back to be considered in new policies; and
- the third is concerned with running a major programme. This is where the cost of security failures in significant areas is identified and acceptable security is built into business processes and systems. A single programme coordinating the business process owners, security experts and representatives from all those affected by the security failure.
The Estates Security unit is responsible for the physical guarding, including security guards.
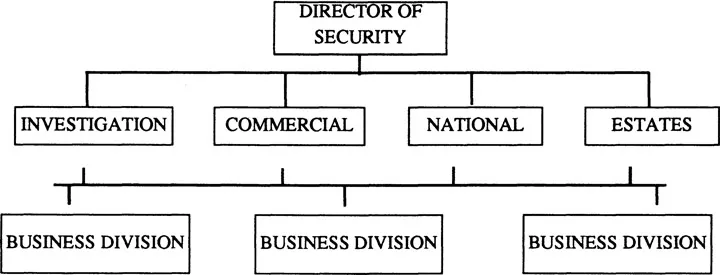
Figure 1.1 Structure of security
1.4 Policy Setting and Awareness
1.4.1 Company policy
An important method of getting security commitment is for the senior managers to make a formal statement of their beliefs. The Company has a security policy statement:
1.4.1.1 Policy
The Board attaches particular importance to the protection of its people, information, business processes, systems and property. The Company’s policy on security is to ensure that we properly safeguard all our assets, having regard to legal and regulatory requirements, the needs of our customers, our commercial interests and sound business practices. In doing so we will provide a quality security environment for our customers and our people.
1.4.1.2 Scope
This policy applies to all aspects of Company’s operations including networks and switching systems, products and services, administration procedures and system s, security of buildings and the workplace, and all internal communications.
Security issues must be considered at all stages in the life cycle of business processes, products and services; from feasibility study through development to operational use and withdrawal from service. It applies regardless of whether a product or process is developed or acquired from an external supplier, and to operations at all locations, including customer premises and international operations.
1.4.1.3 Responsibilities
People are personally responsible and accountable for the security of their operations. Senior Divisional Management, through their Security Coordinators, will be responsible and accountable for the provision of divisional security management and support services using a team of suitably qualified and trained people.
To help everyone carry out these responsibilities, the Director of Security and Investigation will issue appropriate supporting policy and advice, provide certain specialist security services, and is the Company authority for policy on security and will monitor compliance with it.
1.4.2 Baseline policies
Baseline policies have been set within three key documents that are compulsory throughout the Company. These are the:
- Commercial Security Manual, covering security policies for all electronic systems;
- Information Security Code, covering the secure handling of all information;
- Physical Security Handbook, covering policy in the physical and environmental protection of buildings and business processes.
These policies are the baseline policies that apply throughout the Company (see Figure 2). Each business division interprets and adds to the policies for their own particular business area. Security Coordinators are responsible for these activities, and in many cases have amplified and set more stringent requirements, in their own particular areas.
In addition, for security critical items such as products, computer systems, platforms and so on, security standards are produced.
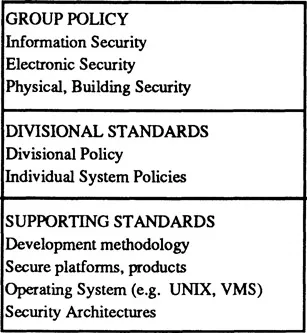
Figure 1.2 Policy hierarchy
1.4.3 Policy compliance checking and other activities
The Commercial Security Compliance and Review unit checks key business processes for their conformance to existing policy. The unit draws members from throughout Company, so individual experts in particular areas can contribute to the right part of a security review. This is important as in many technical areas it is not possible for security people to be fully informed about the risks of, say, a particular operating system.
A security review is not the same as an audit within our Company; the team works closely with the client to make sure that their recommendations are technically feasible and cost effective. A full quality review of the documentation is always held with the client at the end, and this ensures that recommendations are understood and discussed.
As a result of reviews and the making of policies, it often becomes necessary to ensure that suitable products and systems exist to support the security features that are developed. Our Research Department makes, designs, and defines security products, algorithms and systems. This expertise is used to ensure that products are suitable for the threats against which they will be used as countermeasures.
1.5 Conclusion
Over the last six years, the Company has developed its security structure to meet the changing business need. We believe that we now have the right structure to meet the threats that we now face. Naturally, continuous improvement is the key, with the costs and assessment of the threats we face being constantly reviewed, and an apt business decision made to ensure that we use sufficient resources to contain the losses that we sustain.
Acknowledgements
Acknowledgement is due to the Director of Security and Investigation for permission to publish this paper.
2
Information Technology Security Evaluation: Management Summary
2.1 The Need for Security
The effective use of Information Technology (IT) is essential for increasing business prosperity; dependence on IT is increasing, as is the diversity of usage within all sectors of commerce and industry. However, there are potential risks associated with the use of IT...
Table of contents
- Cover
- Title
- Copyright
- Contents
- Data Security – An Introduction
- 1. An Organisation for Security in a Major Company
- 2. Information Technology Security Evaluation: Management Summary
- 3. Closing the Evaluation Gap – the CLEF Experience
- 4. Mechanisms of Stealth
- 5. Computer Viruses
- 6. Security Modelling
- 7. Secure Delivery of Software
- 8. Digital Signatures for Non-Repudiation
- 9. Network Encryption Management
- 10. Computer Crime: Law and Regulation – Protection and Prosecution
- 11. A Structured Control Methodology to Aid Data Security
- 12. Securing your PC
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Practical Data Security by John Gordon in PDF and/or ePUB format, as well as other popular books in Computer Science & Information Technology. We have over one million books available in our catalogue for you to explore.