
eBook - ePub
Intelligent Copyright Protection for Images
- 152 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Intelligent Copyright Protection for Images
About this book
This book describes the need of copyright protection for multimedia objects and develops an invisible image watermarking scheme to serve the purpose of copyright protection. Here intelligent systems are introduced to generate a better visual transparency with increased payload.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Intelligent Copyright Protection for Images by Subhrajit Sinha Roy,Abhishek Basu,Avik Chattopadhyay in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Science General. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Introduction
1.1 Information Hiding and Copyright Protection
1.1.1 Overview
Information hiding is the study of communication in concealment. The main purpose of this type of study is to prevent unauthorized copying and to provide a secured or authenticated system for secret transmission. It may use covert channels, pseudocode writing, or embedding data into a cover object (Katzenbeisser and Petitcolas, 2000). Information hiding techniques are very useful in multilevel security systems. The need-based applications of information hiding can be categorized as follows:
• Information hiding may be used for automatic monitoring of the Web for copyright protection, i.e. to identify the potential illegal usages of marked material on the Web or to tally the digestion of the downloaded documents of any registered Internet document against the original (Anderson, 1994).
• Information hiding is useful to indicate the particulars of music or advertisement content broadcasted on radio channels (Willard, 1993). This is known as an automatic audit of radio transmission.
• For the benefit of the public, users, or purchasers, data augmentation is needed for any objects, such as music or images (Gerzon and Graven, 1995). Information hiding has a role in providing more efficient retrieval from databases of any hidden documents (Johnson, 1999).
• To detect any unauthorized modifications or illegal attempts on any document, a digital object can be embedded in the document so that any type of tampering can be detected (Lin and Chang, 1999).
• Authentication and royalty proof are matters for using information hiding technologies.
This book primarily focuses on the information hiding techniques that can carry out the function of copyright protection for multimedia objects. Basically, copyright is the intellectual information used to protect the uniqueness and ownership of original works or documents, such as images, text, audio, video, software, architecture, etc. The modern trend for digital data transmission leads to large volumes of information transfer. Customers are benefited by the ease of use of property in the digital domain. Regrettably, this feature is often mistakenly and poorly utilized and that degrades data authentication. So, copyright protection in data transmission is essential not least for providing authentication to the signals, and it has become one of the most vital issues in this modern research era.
In the next section, the progress of information hiding is drawn from the ancient age to the present day. This discussion will be helpful when developing ideas about the growth of information hiding techniques and their employment in copyright protection.
1.1.2 Hiding Techniques
According to the methods and purposes, we can classify information hiding techniques in several ways. Before we go into detail of the present-day methods, we look at a historical review of information hiding.
1.1.2.1 The Ancient Age
The practice of information hiding has been taking place since the age of verbal communication. When words were not invented and no languages were present, only a few different sounds served the purpose of conveying messages. The uniqueness was maintained by the sounds used by each community so that no one, other than the people of that community, could understand the messages. In the process of human evolution, we learned to write, and uniqueness was kept up in the writing patterns. Different languages evolved. Smaller groups amalgamated and used larger territories. People started to prefer uniformity in communication rather than individuality. At this stage came the need to hide secret information. There are several examples of covert writing and information hiding in the world’s history. We can find them in Homer’s Iliad (Homer, 1972), Herodotus’ Histories (Herodotus, 1992), Vatsyayana’s Kama Sutra, Kautilya’s Arthashastra, and in many others (Ganguly, 1979; Kahn, 1967; Petitcolas et al., 1999). In the Kama Sutra, Vatsyayana mentions ‘Mlecchita-vikalpa,’ an art of secret writing through which women could conceal details of their liaisons. An example is given in Figure 1.1a of one of the suggested techniques. Here, letters from A to Z are haphazardly paired and the original message is written by replacing each letter with its comparable letter. Thus, the word CONFIDENTIAL has become RJLAMYSLGMFN. This led to present-day cryptography.
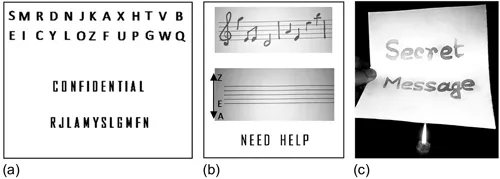
FIGURE 1.1 Example of early information hiding techniques: (a) Vatsyayana’s cipher-based data hiding; (b) use of musical notation to hide information; (c) use of lemon juice as invisible ink.
One of the oldest practices of information hiding is technical steganography, although the term ‘steganography’ itself came into use after the appearance of Trithemius’ book on steganography in the fifteenth century. A famous example of technical steganography was told by Herodotus. In Ancient Greece, Histiaeus tattooed information on the shaved head of his most trusted slaves and, when the hair had regrown, the messages were hidden. Herodotus also told of how Demaratus, a Greek, informed Sparta about an imminent invasion by Xerxes, king of Persia. Removing the wax from a writing tablet, Demaratus wrote his message on the wood and covered it again with the wax.
Aeneas the Tactician (Tacticus, 1990) introduced some message-hiding techniques, such as sending letters through the soles of messengers’ shoes, concealing messages in women’s earrings, writing secret information on the wooden frames of writing tablets and then covering it them with wax, etc. He also suggested a famous technique that was still in use during the seventeenth century. Using this technique, a cover text was typed and the letters constructing the information were highlighted either by changing the heights of those particular letter strokes or by making very small holes above or below the letters (Katzenbeisser and Petitcolas, 2000). This technique was improved by Wilkins (1694), who used invisible ink when printing the tiny dots instead of making holes. This method was also used by German spies during both the World Wars, and an improved version of this practice is still in use for security purposes today.
Dragon, a French photographer, succeeded in making tiny images and, as a result, messages on microfilm became a means of information exchange via pigeon post during the Franco-Prussian War of 1870–1871 (Hayhurst, 1970; Tissandier, 1874). During the Russo-Japanese War (1904–1905), microscopic messages were hidden in ears and nostrils, and under fingernails (Stevens, 1968).
Linguistic steganography was also used for the purpose of information hiding. It was used in two ways: semagram, which is not in written form, and open code, which means a code that uses words in scrambled messages or illusions. As an example of a semagram, John Wilkins had shown how two musicians could communicate with each other by playing on their musical instruments as if they were actually speaking with those instruments. Musical notation can also be used as a secret language simply by identifying the staves with distinct alphabets (Figure 1.1b). Geometric drawings can use points, lines, angles, triangles, etc., which can also indicate a message. One of the greatest examples of open code is found in Hypnerotomachia Poliphili (Colonna, 1499), published in 1499. This book divulged an illicit love between a monk and a woman in an innovative way – the first letter of each of the 38 chapters spelled out “Poliam frater Franciscus Columna Peramavil,” which is supposed to mean “Father Francisco Columna loves Polia.”
An extensively used technique of information hiding is the use of invisible inks. Lemon juice can be used as an ink, and it becomes visible only when the paper is heated (Figure 1.1c). Ovid suggested using milk as invisible ink in his Art of Love. Later progress in chemistry invented more sophisticated combinations of ink, developed at the time of the First World War. But the process was not so useful after the invention of ‘universal developers,’ which could be detected as the wetted parts of the paper. This led to the discovery of watermarking for information hiding.
An example of copyright protection from the ancient age is the Liber Veritatis of Claude Lorrain, the great painter. Liber Veritatis is a sketchbook that consists of two types of paper arranged in such a manner that every four blue pages will be followed by four white pages. This book was a collection of Lorrain’s 195 drawings and was made to prevent forgery, as well as to serve the purpose of authentication (Samuelson, 1995).
The concepts of earlier data hiding techniques have been...
Table of contents
- Cover
- Half-Title
- Series
- Title
- Copyright
- Dedication
- Contents
- Preface
- Acknowledgements
- About the Authors
- Chapter 1 ■ Introduction
- Chapter 2 ■ Perspectives on Digital Image Watermarking
- Chapter 3 ■ Intelligent Systems Used in Copyright Protection
- Chapter 4 ■ Copyright Protection Framework
- Chapter 5 ■ Hardware Implementation
- Chapter 6 ■ System Evaluation
- Chapter 7 ■ Conclusion
- References
- Index