
eBook - ePub
Introduction to Communications Technologies
A Guide for Non-Engineers, Third Edition
- 364 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Introduction to Communications Technologies
A Guide for Non-Engineers, Third Edition
About this book
Thanks to the advancement of faster processors within communication devices, there has been a rapid change in how information is modulated, multiplexed, managed, and moved. While formulas and functions are critical in creating the granular components and operations of individual technologies, understanding the applications and their purposes in the
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Introduction to Communications Technologies by Stephan Jones,Ronald J. Kovac,Frank M. Groom in PDF and/or ePUB format, as well as other popular books in Computer Science & Information Technology. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Systems and Models of Communications Technologies: ShannonWeaver, von Neumann, and the Open System Interconnection Model
The language, acronyms, and terminology in communications technology (CT) are based on fundamental ideas that can be considered systems. Understanding these fundamental systems allows knowledge of various information technologies (IT) to be added, brick by brick, to build an understanding of current and developing technologies. One of the primary systems in CT is signaling. Signaling occurs in traditional voice telephone connections, local area networking, and wireless communications ranging from cellular to satellite systems. Each of these areas of signaling usually becomes the domain of an engineer who is focused specifically on this area of expertise. Preparing someone to understand all the intricacies of each of these disciplines is a huge undertaking. However, understanding the basic underlying principles of the signaling process can give the nonengineering professional the ability to converse on the topic intelligently.
The capacity to communicate is determined by a number of factors that influence the quality of the signal. How will the information be sent or transmitted? Will the person or device at the distant end of the communication signal be able to receive the transmitted signal? Will the person or device at the receiving end need to decipher or decode the signal in any way? What would happen if noise were introduced into the transmitted signal? Would it cause the transmission signal to be corrupted in any way?
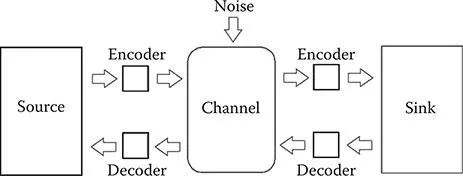
Exhibit 1.1 shows how communications can be understood in terms of a model (or systems format). The source (transmitting side of communications) signaling systems need to encode the information to be transmitted so that it fits onto the medium or channel that is used to convey the information. The medium could be air, copper wires, or even fiber optics. When we speak to another human, we first determine whether or not the person understands the language we are speaking. As the source, we encode our information in the language and put it on the medium (air) to be delivered to the other person. What if the transmitting person has French as his or her primary language and the receiving person does not? The receiving person will need to decode the French language into one that he or she is able to understand. The return signal from the receiving person may ask the transmitting person, Is this what you are trying to tell me? If it is, then we can discuss this topic further. This type of transmit/receive/confirm format is the basis of human communication and is also employed in data networking transmissions.
Claude Shannon developed a mathematical equation that defines the theoretical limit of the capacity of information transmitted in this model. He theorized (and later proved) that the amount of information being transmitted was based on a number of factors, including noise, frequency, transmission, and the strength of the signals. The formula is
Do not be concerned about solving the math problem! It is presented to show the relationship between the signal (S) and noise (N) in a given transmission based on the bandwidth (B) or frequency at which the signal is being transmitted. The capacity (C) of information being transmitted is determined by all of these factors. Later, when we consider more complex topics, we will be able to use this formula to help us understand how much information can be transmitted over a wireless connection for our local area network or how our cell phone can be used to connect to the Internet. This formula tells us that as the noise in a transmission increases, the capacity to send information decreases. As the frequency (or bandwidth) at which we transmit increases, the capacity for information transfer increases. We will discuss the topics of frequency and bandwidth in Chapter 3.
Computing Model
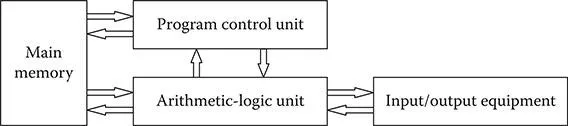
Any device on a communication network can be considered a node. A node can be a computer, telephone, router, server, tandem switch, or any number of devices that receive and transmit information on their respective networks. If every device connected to a network used a different format for collecting, storing, modifying, or transmitting information, the design of networks and the components connected to them would be extremely difficult to accomplish. John von Neumann, a mathematician whose theories led to the development of the first electronic digital computer, proposed a model based on work originally presented by Alan Turing (a mathematician who is famous for leading the group responsible for deciphering the Enigma code during World War II). Von Neumanns idea is known as the stored program model. Exhibit 1.2 is a simple block diagram of von Neumanns model.
The general structure of this model is based on four primary components, and a fifth component is necessary for interblock signaling. This model can be extrapolated to define how the nodes connected to any communication network operate:
1. Main memory: stores data and instructions
2. Arithmetic Logic Unit (ALU): performs computational functions on binary data
3. Control unit: interprets the instructions in memory and causes them to be executed
4. Basic Input/Output System (BIOS): devices operated by the control unit
The fifth component of this model is the bus structure. The information that needs to be exchanged between these blocks relies on an interconnecting medium referred to as a bus. Bus structures can be found in everything from digital wristwatches to the most sophisticated high-speed computer device. We will look at this model and how it relates to a computer and, using the same model, define how it works with telephone systems, data networking equipment, and other nodal devices.
The main memory on the computer is its working area. The program files that are needed to run specific applications are stored in this work area. An analogy is with a large legal pad of paper. The program running on a computer occupies the top page of a writing tablet: this area of memory is also called the random access memory (RAM) of a computer. If it needs more information to process a request, the system will look into the pages available on the tablet to see if the data are there. To retrieve more information for a program or to pull a completely new program into the work area, the system needs to retrieve more pages of information (data). Another typical memory storage area is the hard drive, which, according to our model, is viewed as an I/O device.
The process of responding to requests for data is based on a set of instructions written in binary language. Most of us have never seen the machine language that runs our digital devices, but it is the mother tongue of the information age. Requests for printer or modem access (instructions for information retrieval) and other functions are acted upon by the central processing unit (CPU). The CPU relies on the ALU to crunch numbers and feed the information back so that it can control the flow of data.
Exhibit 1.3 represents a more detailed view of the stored program model. The memory portion of the diagrams is now populated with the various pages of information necessary to operate the computer: BIOS, operating system, and application programs. The bus structure represented by arrows in Exhibit 1.2 is shown in greater detail in Exhibit 1.3, which shows the connection between the memory, CPU, and ALU. The I/O modules are connected to external memory (hard drives), networks, or printers. This greater level of detail depicted in Exhibit 1.3 is also applicable to other network equipment that requires processing and memory management to work.
This model can be used to define how a router, digital personal automatic branch exchange (PABX), and data networking switches work. (These topics are defined in subsequent chapters.) A router is a device used in data networks to forward information from one network to another. They are the workhorses of the Internet, the World Wide Web (the web), and corporate wide area networks (WANs). With this level of responsibility, the equipment may seem more complex and sophisticated than it really is. A router is required to analyze packetized information received from its I/O module connection to decide where the information packet is sent or routed next. This requires an operating system that keeps the organization of the system flowing correctly. A CPU to control requests in conjunction with the ALU is necessary to analyze the binary data. Connecting all of these parts together is a bus structure that is able to send and receive millions of requests every second!
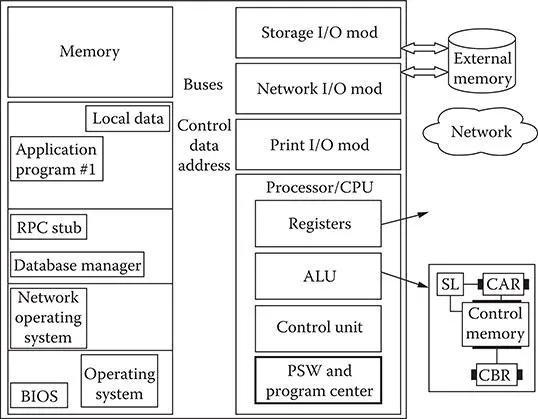
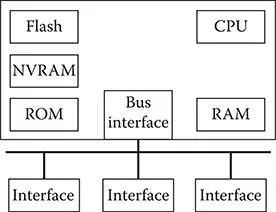
Exhibit 1.4 is another example of how the von Neumann architecture works on a different type of computing device. The router has all the components previously defined for a computer, and it works in a similar manner. The operation system and application programs reside in the flash and other nonvolatile memory. Just as in the computer, RAM is the working area memory of the router. A router does not need the same memory capacity as a computer, but it requires the same binary process, or 1s and 0s, to analyze data.
By understanding the von Neumann architecture, you can comprehend how any number of devices can operate on different networks. The foundational work ...
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Table of Contents
- Preface
- Authors
- 1 Systems and Models of Communications Technologies: Shannon–Weaver, von Neumann, and the Open System Interconnection Model
- 2 Basic Concepts of Electricity
- 3 Modulation Schemes
- 4 Signaling Formats, Multiplexing, and Digital Transmissions
- 5 Legacy to Current-Day Telephone Networks
- 6 Basics of Multiprotocol Label Switching Networking
- 7 Local Area Network Technology
- 8 The Language of the Internet: Transmission Control Protocol/ Internet Protocol (TCP/IP)
- 9 Wireless Local Area Networks
- 10 Mobile Wireless Technologies
- 11 Virtualization
- 12 Analyzing Big Data
- 13 The Cloud and Cloud Computing
- 14 Video Basics
- 15 Digital Media
- 16 Network Security and Management
- Appendix: Answer Key to Chapter Questions
- Index