1
Foundations of biometric identification
Introduction
The continuing advancement of scientific technology is the key factor in the vast improvements to living standards in western countries in the twentieth and twenty-first centuries. The contribution of scientific technology to crime prevention, investigation and other aspects of the criminal justice system, such as trials, is significant.
One of the earliest means of identifying individuals in the criminal justice system was fingerprinting, a technique first developed in the late eighteenth century to identify individuals based on the unique patterns on the fingertips. This technique is still used in the twenty-first century; however, it has now been digitised. Other examples of technology that has been developed to assist with criminal investigation include closed circuit television (CCTV) and deoxyribonucleic acid (DNA) identification, among others. The applications of technology in policing continue to rapidly expand into a central aspect of police work. This includes new developments relating to police information systems, big data analytics and predictive policing. All of these techniques have made very significant contributions to the investigation and prosecution of crime, but must be considered in the context of potential inaccuracy, due process implications and impacts on individual rights. Since the turn of the century, advancements in physics and information technology have provided the basis for a range of powerful identification techniques that continue to develop.
This text provides coverage and analysis of the major forms of biometrics that are currently used throughout the criminal justice sector, and, to some extent, the national security and commercial sectors. Biometrics that are presently being developed or used on a small scale, but are likely to become widely adopted in the future are also considered. The major forms of biometrics used in the criminal justice sector, including fingerprints, DNA and facial recognition will be discussed; along with emerging biometric technologies including ocular biometrics such as retina and iris recognition, voice recognition, vascular pattern recognition, keyboard dynamics, cognitive biometrics and gait analysis.
This introductory chapter is divided into four parts. The first discusses the conceptual foundations of biometric identification, and its historical development; the second examines the scientific background to some of the most commonly used biometrics; the third investigates the development of police information systems and their role in storing, searching and analysing biometric information to produce a match; and the final part considers theoretical and human rights issues that are relevant to the field of biometric identification.
Definitions
The term biometric refers to the measurement of a physical feature of the human body. There are many physical features that can be used as biometric identifiers. These include, most commonly, human physiology, such as patterns of the skin, aspects of the eyes, shape of the hands or blood vessel networks; facial appearance, taking account of the distance between the eyes, nose or mouth, or the general shape of the face; behavioural traits, such as gait or voice characteristics; and biodynamics, such as the pressure, pattern and speed of keystroke typing (Clarke, 1999).
As will be discussed further in later chapters, a distinction is drawn between first generation and second generation biometrics. First generation biometrics relate to physiological traits, such as fingerprint and facial recognition; while second generation biometrics include gait, keystroke analysis and cognitive biometrics.
In the context of biometric identification, a biometric feature must not only be a physiological feature capable of being measured, it must be sufficiently distinctive to form the basis of a unique identifier, capable of being efficiently verified. Biometrics should be a:
measurable, robust and distinctive physical characteristic or personal trait that can be used to identify an individual or verify the claimed identity of an individual.
(Woodward et al., 2003, p. 1)
Elaborating on this definition, biometrics must be capable of measurement, meaning that it must be possible to convert them to a digital format enabling database storage and searching. This has significant implications in the context of policing practice. A biometric must not change significantly over time, and be stable and reliable through the aging process, injury or changes in environmental conditions (Woodward et al., 2003).
Biometric identification can be contrasted with other means of identification, such as keys, photo identification cards and passwords that are used, for example, as proof of the right to obtain access to a restricted account, Internet site or building. The main distinction between biometric information and other contemporary forms of identification is that it is a part of the individual themselves, rather than an object carried on the person, or a password or code. A succinct description of biometric identification used by Hopkins (1999) to distinguish it from other forms of identification is that rather than being something that an individual knows or has, it is something that they are.
Biometric identification involves the automatic identification of a person based on their physiological or behavioural characteristics. This is undertaken by using non-invasive computer technology to match characteristics of live individuals in real time against stored records, such as their face or fingerprint, in applications such as border or physical access control (International Biometrics Industry Association, 2000).
Historical background
The earliest known examples of biometric identification occurred in Ancient Egypt at the time of Pharaoh Khaefre (2558BC–2532BC). Biometric identification was used to identify construction workers, with the purpose of ensuring that food provided by the state was shared equitably among those legitimately eligible to receive it. Administrators developed a system that recorded the distinctive physical and behavioural characteristics of workers, along with their name, age and place of residence, to address the issues of some employees attempting to obtain more than their allocated food allowance. In the more recent past, Frenchman Alphonse Bertillon developed more scientific forms of biometric identification in the nineteenth century. Bertillon developed a method of ‘judicial anthropology’ which identified criminals on the basis of anatomical features (Ashbourn, 2000).
The most significant historical development in biometric identification occurred in the mid-nineteenth century. Czech scientist, Jan Evangelista Purkinje (1787–1869), established that fingerprints were unique, which had implications for identifying individuals involved in criminal activity. Research continued into the applications of fingerprinting and techniques to record them throughout the nineteenth century. Francis Galton (1822–1911), a British geneticist, first used the term biometry in 1901 to describe ‘the application to biology of the modern methods of statistics’ and made further contributions to fingerprint and facial biometric analysis (Pato & Millett, 2010, p. 17). Scotland Yard was the first law enforcement agency to use fingerprints in criminal investigations in the twentieth century, applying Galton’s classification system (Ashbourn, 2000). Since that time, fingerprint identification has become an important component of criminal investigations, and remained the most important form of identifying people until the 1990s when DNA profiling became widely adopted in criminal investigations, providing a new avenue for the review of criminal convictions (Boukhonine, Krotov & Rupert, 2005).
Historically, names, passwords, personal identification numbers, keys and passwords have been used to verify individuals. However, these are proxies for the verification of a person’s presence, a password can be shared, a key can be lost and a system cannot know who has presented an item (Pato & Millett, 2010). The other contemporary methods of biometric identification that are discussed throughout the text have been developed and implemented in the last two decades. They seek to apply scientific advancement to address these problems, but in turn have other issues that must be addressed.
Identification methods and issues
There are three main ways in which biometrics are used. The first is one-to-many searching, which involves a biometric profile being compared with a database of profiles to identify the individual through a direct or partial match, resulting in a computer generated likelihood that any two profiles are from the same individual. This approach is generally used in a surveillance context by police or intelligence agencies or in a criminal investigation when a DNA profile is obtained from biological material located at a crime scene and the police seek to identify an unknown individual. The second approach is one-to-one verification of identity, which seeks to determine whether an individual is who they purport to be. In this case, a live profile is provided by the individual and compared with a template stored in the computer system or identification document, such as a passport or licence. This is increasingly being used in providing an individual with physical access to a building or computer network, or to transit through international borders. The third approach in which biometrics can be used is to identify individuals on a watch-list, for example, by screening CCTV footage using facial recognition technology – a more challenging task than the methods described in the first two examples (Table 1.1) (Du, 2013).
TABlE 1.1 Basic functions of biometrics
| Type | Matching | Question | Difficulty |
| Verification | One-to-one | Are you who you claim to be? | Hard |
| Identification | One-to-many | Who are you? | Harder |
| Watchlist | One-to-a-few | Are you a person of interest? | Hardest |
Source: Du, 2013
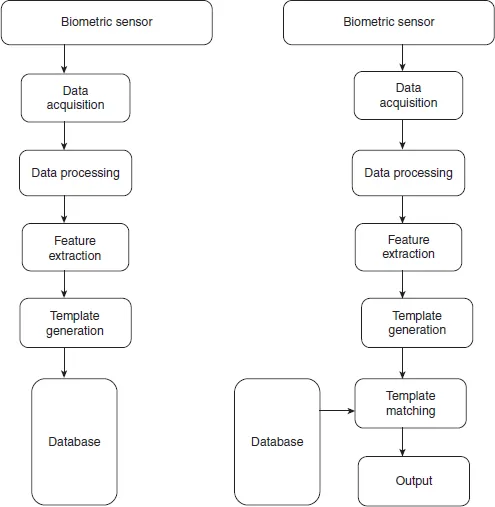
Biometric systems involve an enrolment stage and a matching process. Enrolment involves the acquisition of the individual’s biometric data, generating a template that can be stored in a database. Matching also involves the acquisition of an individual’s biometric data, but adds the comparison with all templates held in a database to establish whether a match can be established (Figure 1.1) (Du, 2013).
FIGURE 1.1 Biometric system enrolment and matching processes
Source: Du, 2013
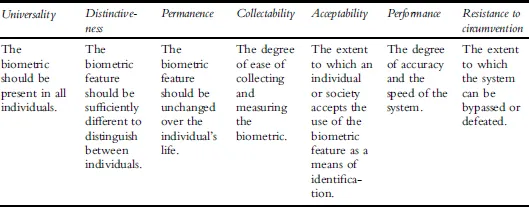
There are several considerations in selecting physical traits for biometric identification. Each biometric has strengths and weaknesses and may be suitable for identification purposes depending on the context. There are also general suitability criteria that can be applied to each biometric identification method to assess which is the most appropriate in particular circumstances. Seven criteria have been accepted as key indicators of the suitability of biometric features. These are: universality, distinctiveness, permanence, collectability, acceptability, performance and resistance to circumvention or ‘spoofing’. Collectively, this group of criteria have been referred to as the seven pillars of biometrics (Table 1.2) (Jain, Ross & Pankanti, 2006).
TABlE 1.2 The seven pillars of biometrics
When compared against these criteria, certain types of biometrics have features that make them most suitable in particularly contexts. Fingerprinting may be favoured over gait analysis for accuracy in a broader range of contexts because it may be considered more distinctive and permanent, however, in some contexts (such as analysing television footage) gait analysis may be preferred because it can be assessed from a greater distance. On the other hand, in cases where a large number of people must be processed quickly, such as a border crossing, fingerprint or iris recognition may be most appropriate because a high degree of accuracy is required and a person’s identity is being confirmed in close proximity.
Fingerprint identification
Fingerprints are universal in the human population and remain unchanged throughout life. In combination with easy accessibility, the fact that they are deposited on surfaces by touch makes them an attractive feature for biometric identification. Fingerprints are formed in the first seven months of foetal development and are caused by the formation of nerves beneath the skin. Their key purpose is to enhance grip when handling objects. Individual fingerprints are unique among all other fingers of the same person, and indeed, among all persons, including identical twins. One limitation of fingerprint identification is that the fingerprints of approximately four per cent of the population cannot be effectively used for biometric identification purposes, due, for example, to burns and other injuries, limiting the prospect of universal population coverage. Fingerprints can also be faked relatively easily (Dessimoz et al., 2006).
Fingerprints are composed of a series of ridges and valleys in the skin on the surface of the fingertip that form a unique pattern. Fingerprint patterns are described by three key features, arches, loops and whorls: one of each is present in every fingerprint. The centre of a pattern is described as the core and points of discontinuity in the fingerprint ridges are known as minutiae (Jain, 2004). Fingerprint identification compares the unique combination of the patterns of ridges and valleys. Fingertips are placed against an optical scanner and a laser illuminates the fingerprint an...