Digital information and data are transmitted more often over the Internet now than ever before. The availability and efficiency of global computer networks for the communication of digital information and data have accelerated the popularity of digital media. Digital images, video, and audio have been revolutionized in the way they can be captured, stored, transmitted, and manipulated. This gives rise to a wide range of applications in education, entertainment, the media, industrial manufacturing, medicine, and the military, among other fields [1].
Computers and networking facilities are becoming less expensive and more widespread. Creative approaches to storing, accessing, and distributing data have generated many benefits for digital multimedia, mainly due to properties such as distortion-free transmission, compact storage, and easy editing. Unfortunately, free-access digital multimedia communication also provides virtually unprecedented opportunities to pirate copyrighted material. Therefore, the idea of using a digital watermark to detect and trace copyright violations has stimulated significant interest among engineers, scientists, lawyers, artists, and publishers, to name a few. As a result, research into the robustness of watermark embedding with respect to compression, image-processing operations, and cryptographic attacks has become very active in recent years, and the developed techniques have grown and been improved a great deal.
In this chapter, we introduce digital watermarking in Section 1.1 and digital steganography in Section 1.2. The differences between watermarking and steganography are given in Section 1.3. Finally, a brief history is described in Section 1.4.
1.1DIGITAL WATERMARKING
Watermarking is not a new phenomenon. For nearly a thousand years, watermarks on paper have been used to visibly indicate a particular publisher and to discourage counterfeiting in currency. A watermark is a design impressed on a piece of paper during production and used for copyright identification (as illustrated in Figure 1.1). The design may be a pattern, a logo, or some other image. In the modern era, as most data and information are stored and communicated in digital form, proving authenticity plays an increasingly important role. As a result, digital watermarking is a process whereby arbitrary information is encoded into an image in such a way as to be imperceptible to observers.
FIGURE 1.1 A paper watermark.
Digital watermarking has been proposed as a suitable tool for identifying the source, creator, owner, distributor, or authorized consumer of a document or an image. It can also be used to detect a document or an image that has been illegally distributed or modified. Another technology, encryption, is the process of obscuring information to make it unreadable to observers without specific keys or knowledge. This technology is sometimes referred to as data scrambling . Watermarking, when complemented by encryption, can serve a vast number of purposes including copyright protection, broadcast monitoring, and data authentication.
In the digital world, a watermark is a pattern of bits inserted into a digital medium that can identify the creator or authorized users. Digital watermarks— unlike traditional printed, visible watermarks— are designed to be invisible to viewers. The bits embedded into an image are scattered all around to avoid identification or modification. Therefore, a digital watermark must be robust enough to survive detection, compression, and other operations that might be applied to a document.
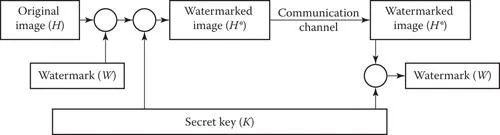
Figure 1.2 depicts a general digital watermarking system. A watermark message W is embedded into a media message, which is defined as the host image H . The resulting image is the watermarked image H* . In the embedding process, a secret key K — that is, a random number generator— is sometimes involved to generate a more secure watermark. The watermarked image H* is then transmitted along a communication channel. The watermark can later be detected or extracted by the recipient.
FIGURE 1.2 A general digital watermarking system.
Imperceptibility, security, capacity, and robustness are among the many aspects of watermark design. The watermarked image must look indistinguishable from the original image; if a watermarking system distorts the host image to the point of being perceptible, it is of no use. An ideal watermarking system should embed a large amount of information perfectly securely, but with no visible degradation to the host image. The embedded watermark should be robust, with invariance to intentional (e.g., noise) or unintentional (e.g., image enhancement, cropping, resizing, or compression) attacks. Many researchers have focused on security and robustness, but rarely on watermarking capacity [2,3]. The amount of data an algorithm can embed in an image has implications for how the watermark can be applied. Indeed, both security and robustness are important because the embedded watermark is expected to be imperceptible and unremovable. Nevertheless, if a large watermark can be embedded into a host image, the process could be useful for many other applications.
Another scheme is the use of keys to generate random sequences during the embedding process. In this scheme, the cover image (i.e., the host image) is not needed during the watermark detection process. It is also a goal that the watermarking system utilizes an asymmetric key, as in public or private key cryptographic systems. A public key is used for image verification and a private key is needed for embedding security features. Knowledge of the public key neither helps compute the private key nor allows the removal of the watermark.
For user-embedding purposes, watermarks can be categorized into three types: robust , semifragile , and fragile . Robust watermarks are designed to withstand arbitrary, malicious attacks such as image scaling, bending, cropping, and lossy compression [4– 7]. They are usually used for copyright protection in order to declare rightful ownership. Semifragile watermarks are designed for detecting any unauthorized modifications, while at the same time enabling some image-processing operations [8]. In other words, selective authentication detects illegitimate distortion while ignoring the applications of legitimate distortion. For the purpose of image authentication, fragile watermarks [9– 13] are adopted to detect any unauthorized modification at all.
In general, we can embed watermarks in two types of domains: the spatial domain or the frequency domain [14– 17]. In the spatial domain we can replace the pixels in the host image with the pixels in the watermark image [7,8]. Note that a sophisticated computer program may easily detect the inserted watermark. In the frequency domain, we can replace the coefficients of a transformed image with the pixels in the watermarked image [19,20]. The frequency domain transformations most commonly used are discrete cosine transform, discrete Fourier transform, and discrete wavelet transform. This kind of embedded watermark is, in general, difficult to detect. However, its embedding capacity is usually low, since a large amount of data will distort the host image significantly. The watermark must be smaller than the host image; in general, the size of a watermark is one-sixteenth the size of the host image.