
- 200 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Cyber Strategy: Risk-Driven Security and Resiliency provides a process and roadmap for any company to develop its unified Cybersecurity and Cyber Resiliency strategies. It demonstrates a methodology for companies to combine their disassociated efforts into one corporate plan with buy-in from senior management that will efficiently utilize resources, target high risk threats, and evaluate risk assessment methodologies and the efficacy of resultant risk mitigations. The book discusses all the steps required from conception of the plan from preplanning (mission/vision, principles, strategic objectives, new initiatives derivation), project management directives, cyber threat and vulnerability analysis, cyber risk and controls assessment to reporting and measurement techniques for plan success and overall strategic plan performance. In addition, a methodology is presented to aid in new initiative selection for the following year by identifying all relevant inputs.
Tools utilized include:
- Key Risk Indicators (KRI) and Key Performance Indicators (KPI)
- National Institute of Standards and Technology (NIST) Cyber Security Framework (CSF) Target State Maturity interval mapping per initiative
- Comparisons of current and target state business goals and critical success factors
- A quantitative NIST-based risk assessment of initiative technology components
- Responsible, Accountable, Consulted, Informed (RACI) diagrams for Cyber Steering Committee tasks and Governance Boards' approval processes
- Swimlanes, timelines, data flow diagrams (inputs, resources, outputs), progress report templates, and Gantt charts for project management
The last chapter provides downloadable checklists, tables, data flow diagrams, figures, and assessment tools to help develop your company's cybersecurity and cyber resiliency strategic plan.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
1.1 The Value Proposition
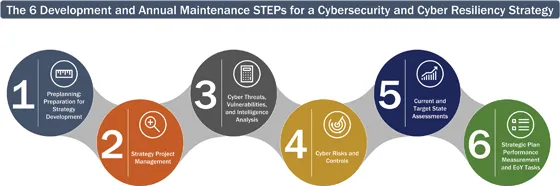
1.2 The 6 Steps for Developing and Maintaining A Cybersecurity and Cyber Resiliency Strategy
- STEP 1: Preplanning: Preparation for Strategy Development
- STEP 2: Strategy Project Management
- STEP 3: Cyber Threats, Vulnerabilities, and Intelligence Analysis
- STEP 4: Cyber Risks and Controls
- STEP 5: Current and Target State Assessments
- STEP 6: Strategic Plan Performance Measurement and End of the Year (EoY) Tasks
1.3 Cybersecurity and Cyber Resiliency Strategy Key Players
Developers, Approvers, or Readers |
|---|
|
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Contents
- Author Biographies
- Chapter 1 Why Cybersecurity and Cyber Resiliency Strategies Are Mandatory for Organizations Today
- Chapter 2 The 6 STEPs in Developing and Maintaining a Cybersecurity and Cyber Resiliency Strategy
- Chapter 3 Strategy Project Management
- Chapter 4 Cyber Threats, Vulnerabilities, and Intelligence Analysis
- Chapter 5 Cyber Risks and Controls
- Chapter 6 Current and Target State Assessments
- Chapter 7 Measuring Strategic Plan Performance and End of Year (EoY) Tasks
- Chapter 8 Checklists and Templates to Help Create an Enterprise-Wide Cybersecurity and Cyber Resiliency Strategy