
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Surveillance After Snowden
About this book
In 2013, Edward Snowden revealed that the NSA and its partners had been engaging in warrantless mass surveillance, using the internet and cellphone data, and driven by fear of terrorism under the sign of 'security'.
In this compelling account, surveillance expert David Lyon guides the reader through Snowden's ongoing disclosures: the technological shifts involved, the steady rise of invisible monitoring of innocent citizens, the collusion of government agencies and for-profit companies and the implications for how we conceive of privacy in a democratic society infused by the lure of big data. Lyon discusses the distinct global reactions to Snowden and shows why some basic issues must be faced: how we frame surveillance, and the place of the human in a digital world.
Surveillance after Snowden is crucial reading for anyone interested in politics, technology and society.
In this compelling account, surveillance expert David Lyon guides the reader through Snowden's ongoing disclosures: the technological shifts involved, the steady rise of invisible monitoring of innocent citizens, the collusion of government agencies and for-profit companies and the implications for how we conceive of privacy in a democratic society infused by the lure of big data. Lyon discusses the distinct global reactions to Snowden and shows why some basic issues must be faced: how we frame surveillance, and the place of the human in a digital world.
Surveillance after Snowden is crucial reading for anyone interested in politics, technology and society.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1
Snowden Storm
Nineteen Eighty-Four is an important book but we should not bind ourselves to the limits of the author's imagination. Time has shown that the world is much more unpredictable and dangerous than that.
Edward Snowden, July 2014.
The solidly rectangular, fortress-like buildings of the NSA rise forbiddingly from Fort Meade, Maryland. So much is visible on the surface, but another 10 acres of buildings are underground. The dark-tinted glass-clad walls of the office tower reflect images of what looks like a medieval moat with the sprawling fields of parked cars as a kind of protective barrier surrounding it. For many years, the NSA has been shrouded in mystery, clearly super-scale in operation but also in its degree of secrecy. The joke was that NSA stood for ‘No Such Agency’. Most commentators have been forced to speculate on what really goes on inside, aware only that its employees cannot speak of it and that its chain of accountability seems to disappear in the clouds.
Few dare to voice their concerns but when they do they risk being framed as paranoid traitors. William Binney, co-inventor of the NSA's ThinThread program that analysed internet and other communications data, worked for more than 30 years at the NSA. He had climbed to Technical Leader for Intelligence when he resigned in 2001, in protest against increased domestic surveillance after 9/11. Investigated but not prosecuted, he still had to deal with an armed police raid on his home in 2007 and with opposition to his business by the NSA. J. Kirk Wiebe, another ThinThread inventor, also blew the whistle on the NSA. Thomas Drake, a former senior executive at the NSA, whose first day on the job was 9/11, also broke silence about the wastefulness and illegality of the NSA's security-threat data-gathering Trailblazer project – which superseded ThinThread – in 2006 and was prosecuted under the Espionage Act in 2010.
Against this backdrop the revelations about mass surveillance provided by Edward Snowden blew the NSA's cover as never before. NSA as ‘Not Secret Anymore’ was the new joke. The documents he disclosed offer extensive insights into the inner workings of that clandestine community. Among other things they indicate with stark clarity – as Binney, Drake and Wiebe had said before – that mass surveillance is carried out by government agencies on ‘US persons’.
In the US, the impact of citizen surveillance hits hard. Not just suspected terrorists or criminals, but average American citizens are monitored. This staggering fact shows that the stakes include not only privacy but democracy itself. Surely, authoritarian regimes such as China, or former Latin American dictatorships like Argentina, Brazil or Chile, subject their own citizens to surveillance, not democracies?1 This deviation from democratic practice in the US is indeed serious, but it also draws attention to an underlying problem. Why should indiscriminate mass surveillance be considered acceptable anywhere? Surely the distinction between citizens and foreigners itself is invidious in this case?
Snowden's exploits expose the undermining of the rule of law, the lack of care about human rights and the loss of liberty for innocent individuals. At the same time, they indicate how elite power is enlarged, and how the views of ordinary citizens are overridden. Dissent is endangered. The revelations shine light on a hugely expensive and elaborate enterprise of sophisticated surveillance that seems to have abandoned the attempt to distinguish between foreigners and citizens and whose remit clearly extends well beyond anti-terrorism. And this is why trusted officials at the NSA, who believed in the intelligence work they performed, felt it was their moral duty to expose the expansion of surveillance far beyond what was necessary for national security.
This chapter starts by examining the different kinds of NSA surveillance revealed by Snowden, before commenting on Snowden's statement that because of surveillance the world is more unpredictable and dangerous than ever. We then look at what had been quietly developing for decades – the slow cooker of surveillance – and lastly at the sea change represented by post-9/11 pressures and predicaments.
Under the Iceberg Tip
Snowden handed 58,000 secret NSA documents to journalists for them to release in ways that would have maximum impact, a story that Glenn Greenwald and Laura Poitras have begun to tell. Sorting out the evidence of different surveillance techniques and practices is a massive task and the way that the media has latched on to certain stories does not necessarily reflect their comparative importance. Even to think in terms of earlier evidence of NSA ‘warrantless wiretapping’ of the communications of US citizens provided by AT&T technician Mark Klein in 2006 and publicized by James Bamford in 20082 gives little clue about the magnitude of what Snowden uncovered. As Andrew Clement says, the ‘warrantless wiretapping program was the tip of a much bigger iceberg, covering all forms of communications traffic and implicating most of the major telecommunications carriers across the US’.3
Let us look at some dimensions of the iceberg that lie beneath the surface, below its warrantless wiretapping tip. Like icebergs, formed when glaciers meet the ocean and break off to float freely, the NSA's activities are distinctively layered. Three main layers have been made visible by Snowden. The first is the interception of data-in-transit (see figure 1). These are the Upstream programs, including for example, Fairview, which is how the NSA gains access to the 55,000 miles of optical cables that lie between the US and other parts of the world (see figure 2). These cables carry internet data to many places – we learned early about Germany or Brazil4 – where, with the cooperation of local telecoms companies, millions of citizens were surveilled. The NSA and its partners are part of a global mass surveillance system about which most people in the world had no idea and which has profound implications at many levels.
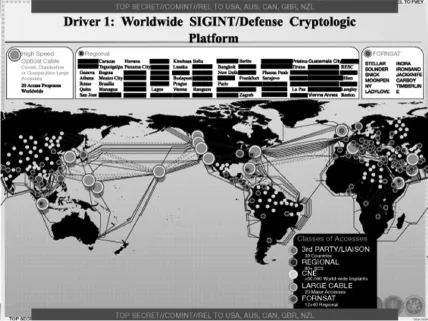
Figure 1 ‘Collect it all’ signals intelligence (SIGINT) interception
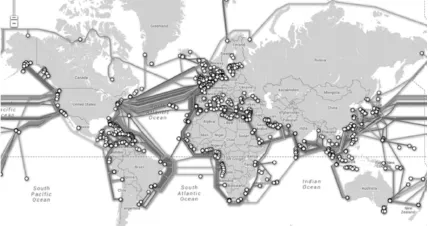
Figure 2 Submarine fibre-optic cabling (telegeography.com)
The second layer of NSA surveillance is its access to stored data. The Prism program is the best-known example, not least because it was featured in one of the first of Snowden's revelations. It is also a primary data-source. This is a data-mining program run by the NSA with help from the UK's GCHQ. Started in 2007, it taps directly into the servers of US internet companies AOL, Apple, Facebook, Google, Microsoft, PalTalk, Skype, Yahoo! and YouTube. It collects, identifies, sorts and stores chatroom posts, emails, file transfers, internet telephone calls, login/IDs, metadata, photos, networking, stored data, videos and video conferencing – and maybe more.5 Although ‘targeted’ at foreigners, it also touches American citizens ‘inadvertently’, ‘incidentally’ or deliberately if an American is conversing with a foreign target overseas. Again, no one guessed the audacity or the scope of such data gathering, nor how well-known companies were partnered with the NSA.
The third layer of the iceberg is the installing of spyware on individual computers, a practice with the innocent-sounding name of Computer Network Exploits (CNE). The Gemalto SIM card case fits here. It is achieved by using programs like Quantum Insert which, as well as capturing data-in-transit, secretly injects malware into users' computers. In another European case, some technical employees at Belgacom, a Belgian telecommunications company, pulled up normal-looking LinkedIn pages that were in fact fake. The lookalike pages contained invisible spyware that allowed UK GCHQ operators to infiltrate Belgacom networks and those of a subsidiary, BICS, that runs a so-called GRX router system. From there, control could be obtained of cellphones that use the router for making calls from abroad. Quantum Insert is the system that enables these practices.6 This means that everyday devices may be infected with malware that is constantly reporting back to spy agencies.
All this suggests that surveillance has in recent times been ramped up to a much higher level than was imagined by anyone before Snowden intervened. So many questions are raised, it is baffling to decide where to begin. How can any government expect to be trusted with their own citizens' data? Who knows when their own telecoms provider is colluding with this surveillance? The systems described here are highly secret, apparently unaccountable and growing by the day. Perhaps the iceberg metaphor is useful for more than the ‘visible tip and submerged mass’ and the ‘distinct layers of what is below the surface’? Another similarity may be that these agencies seem to have floated free ...
Table of contents
- Cover
- Title page
- Copyright page
- Preface
- Acknowledgements
- Citizenfour Alert!
- 1: Snowden Storm
- 2: World Watching
- 3: Menacing Metadata
- 4: Precarious Privacy
- 5: Framing Futures
- Selected Bibliography
- Index
- End User License Agreement
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Surveillance After Snowden by David Lyon in PDF and/or ePUB format, as well as other popular books in Social Sciences & Media Studies. We have over one million books available in our catalogue for you to explore.