
eBook - ePub
Opportunistic Networking
Vehicular, D2D and Cognitive Radio Networks
- 320 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Opportunistic Networking
Vehicular, D2D and Cognitive Radio Networks
About this book
Opportunistic networking, by definition, allows devices to communicate whenever a window of opportunity is available. Many emerging technologies employ opportunistic exchanges of information. This book addresses this trend in communications engineering, taking into account three specific areas—vehicular, device-to-device (D2D), and cognitive radio—while describing the opportunistic communication methods of each. From smart homes to smart cities, smart agriculture to never-die-networks and beyond, the text explores the state of the art of opportunistic networking, providing the latest research, developments, and practices in one concise source.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Opportunistic Networking by Nazmul Siddique, Syed Faraz Hasan, Salahuddin Muhammad Salim Zabir, Nazmul Siddique,Syed Faraz Hasan,Salahuddin Muhammad Salim Zabir in PDF and/or ePUB format, as well as other popular books in Technology & Engineering & Information Technology. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Introduction
Syed Faraz Hasan, Nazmul Siddique, and Salahuddin Muhammad Salim Zabir
Contents
1.1 Introduction
1.2 Mobile Ad Hoc Networks
1.3 Opportunistic Networking
1.3.1 Opportunistic Vehicular Communication
1.3.2 Routing in Opportunistic Networks
1.4 Applications
1.4.1 Smart Environments
1.4.2 Smart Homes
1.4.3 Smart Cities
1.4.4 Smart Agriculture
1.4.5 Smart Health Care
1.4.6 Emergency Communications: An Introduction to Never-Die Networks
1.5 The Road Ahead
References
1.1 Introduction
The concept of interconnecting computer systems began in the 1970s when a few academic institutes in the United States wanted to share data. This culminated in the development of Advanced Research Projects Agency Network (ARPANET), which connected four academic institutions together. The successful deployment and operation of ARPANET gave rise to limitless discussion on how information can be shared between devices. Topics pertinent to the architecture of a network, its operation, the number and type of interconnected devices, data type, and so on were brought into the discussion. Issues related to the type of architecture were particularly interesting. Two of the earliest architectural designs were infrastructure-based and ad hoc networks [1]. Infrastructure-based networks have a central entity, generally the base station, which governs communication between all participating devices. In contrast, in ad hoc networks, devices communicate with each other directly. Because there is no central authority in ad hoc networks, a variety of research issues emerged that required careful consideration. The number and nature of these issues progressed with the introduction of wireless communication services. On top of everything else, devices can now move from one place to another while still staying connected to the network. An ad hoc network that gives its nodes freedom from wires and supports mobile nodes is known as a mobile ad hoc network (MANET) [2].
1.2 Mobile Ad Hoc Networks
By definition, a MANET is a group of devices that relays data from one device to another over several hops until the data reaches its intended destination. Figure 1.1 shows a typical scenario that uses mobile nodes to convey data over a multihop link. MANETs continue to play an important role in present-day communication systems. They are particularly popular in applications that use sensors. Freedom from wires and from a central managing entity makes MANETs an ideal choice for distributed environments. Several communication technologies can be used on such a distributed architecture. For instance, IEEE 802.11 Wi-Fi and IEEE 802.15.4 ZigBee have been extensively used in ad hoc network deployments. Another useful feature of MANETs is that the nodes can commence communication very quickly [3]. Due to this advantage, MANETs work well in emergency communication where access to the network infrastructure has been compromised. Several disaster recovery programs make use of MANETs to provide communication services in emergency environments.
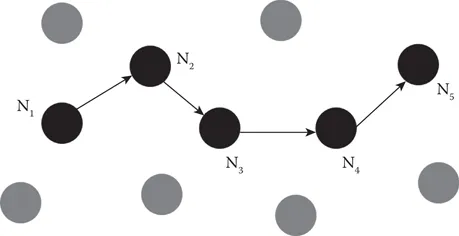
Figure 1.1 A MANET comprising 11 nodes. Node 1 uses Nodes 2–4 as relays to convey information to Node 5.
Because the devices forming a MANET are mobile, the network architecture (or topology) is dynamic. The architecture changes with the mobility of the participating devices. It is intuitive that the greater the device mobility, the quicker the change in network architecture. This rapidly changing architecture poses considerable challenges in terms of protocol design. Legacy communication protocols, for example Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), were developed for a network with fixed topology. It is therefore imperative for the success of MANETs to develop new protocols that can withstand a sudden change in network architecture.
The main discussion in this book starts with a detailed overview of MANETs in Chapter 2. Several important aspects of MANETs, their operation, associated challenges, and application scenarios are discussed in detail in Chapter 2. Giving due attention to the issue of protocol design for a rapidly changing topology, a new protocol known as Beatha is also proposed in Chapter 3. The internal and external delays caused by Beatha and its features related to flow control and retransmission are highlighted. After thoroughly defining the principles and operation of Beatha, its performance is evaluated using Optimized Network Engineering Tool (OPNET) for a variety of static and mobile scenarios. It is shown that Beatha outperforms TCP and its variants in terms of throughput, retransmission count, and time delay. Although Beatha is a routing protocol that is meant for mobile scenarios, we discuss the routing issues in highly mobile scenarios later in Chapters 4 and 5 in this book.
Nevertheless, special-purpose routing protocols such as Beatha keep communication services running even when there is a change in network topology. In certain situations, however, a change in network architecture is so sudden and frequent that communication services run the risk of getting suspended anyway. Such time-critical MANETs are known as opportunistic networks [4]. It must be noted that the notion of opportunistic communication is not limited only to MANETs, as highlighted in the following.
1.3 Opportunistic Networking
In opportunistic networks, devices communicate with each other without having a dedicated end-to-end communication path. It is not necessary to know the communication path between the source and its intended destination in a typical opportunistic network. The concept is very similar to the delay-tolerant networking (DTN) paradigm, which also does not require a dedicated path between the source and destination [5]. In an ideal opportunistic network, the network topology may vary drastically, having little or no impact on the quality of service received by the users. The end user receives a high-level impression of being always connected to the network services. In essence, an opportunistic network offers a series of connections one after another. These opportunistic connections can be enabled by various wireless communication technologies. Dedicated wireless communication technologies that could work well in opportunistic networks are not well known in the literature. Most of the works consider the use of existing wireless technologies in opportunistic environments. These include infrastructure-based as well as ad hoc technologies.
The opportunistic scenarios often emerge because of high node mobility. When a mobile node is moving at high speeds, it often faces periods of connectivity and disruption. An interesting example of an opportunistic communication scenario is fast-moving vehicles that try to access sparsely deployed roadside infrastructure [7]. These vehicles give rise to vehicular ad hoc networks (VANETs), which are very similar to MANETs except that they have higher node mobility. This book gives a detailed account of VANETs in the context of opportunistic networking in Chapter 4. Chapter 5 provides a detailed account of opportunistic networking and its associated challenges. The chapter starts with a discussion on wireless technologies that may suit the intermittent nature of opportunistic networks. A detailed account of how data is forwarded in opportunistic networks is given. Several protocols and their underlying principles to support intermittent data transfer are also highlighted in Chapter 5. Because there is an intermittent path between the source and destination, it is important for the network to be able to store some information. Memory elements called repositories are often employed to hold communication sessions in case a connection is suddenly lost [6]. Chapter 5 also covers a detailed discussion on repositories and their placement within an opportunistic network. Towards the end, Chapter 5 reports some interesting simulation results that may be useful for designing an opportunistic network.
1.3.1 Opportunistic Vehicular Communication
Vehicular communication is the information exchange between vehicles, as well as between vehicles and the roadside infrastructure. The information that these vehicles share may be related to on-road safety services or other infotainment services. Vehicular communication is an essential part of the intelligent transportation systems project, which focuses on improving passenger safety on roads and highways [8].
The notion of opportunity in vehicular communication stems from the fact that vehicles change their position very rapidly, and hence their ability to send data to their immediate neighbors also changes drastically. The length of time for which the vehicles are within each other’s coverage range is an “opportunity” for them to exchange data. At two different instants in time, a vehicle may have completely different neighbors because of high mobility. As can be seen from Figure 1.2, vehicle V1 has taken a turn that resulted in it losing the opportunity to communicate with its previous neighbors. Of course, it will encounter other vehicles on the way and become a part of another VANET.
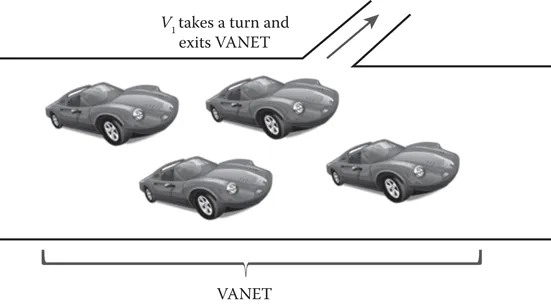
Figure 1.2 The concept of opportunity in vehicular communication.
Chapter 4 of this book starts by defining VANETs and comparing them with MANETs. It then explores various wireless technologies that may be used for enabling vehicular communication. Among several technologies that may be used, IEEE 802.11 has been used extensively in the literature. There...
Table of contents
- Title Page
- Copyright Page
- Table of Contents
- Editors
- Contributors
- 1 Introduction
- 2 Opportunistic Networking: An Application
- 3 Mobile Ad Hoc Networks: Rapidly Deployable Emergency Communications
- 4 Opportunistic Vehicular Communication: Challenges and Solutions
- 5 Routing Protocols in Opportunistic Networks
- 6 Smart Environments: Exploiting Passive RFID Technology for Indoor Localization
- 7 Smart Homes: Practical Guidelines
- 8 Wireless Sensor Network–Based Smart Agriculture
- 9 Cognitive Radio Networks: Concepts and Applications
- 10 Never Die Networks
- Index