
SIP Handbook
Services, Technologies, and Security of Session Initiation Protocol
- 614 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
SIP Handbook
Services, Technologies, and Security of Session Initiation Protocol
About this book
Widely adopted by service providers to enable IP telephony, instant messaging, and other data services, SIP is the signaling protocol of choice for advanced multimedia communications signaling. Compiled by noted engineering experts Syed Ahson and Mohammad Ilyas, SIP Handbook: Services, Technologies, and Security of Session Initiation Protocol presents a thorough technical review of all aspects of SIP. It captures the current state of IP Multimedia Subsystem technology and provides a unique source of comprehensive reference material on this subject.
SIP Applications for Today and Tomorrow
The scope of this volume ranges from basic concepts to future perspectives. Divided into three sections, the book begins with a discussion of SIP in peer-to-peer networks and then goes on to examine advanced media integration, migration considerations, mobility management, and group conferencing, while also reviewing home networking and compliance issues.
The middle section of the book focuses on the underlying technologies of SIP. Chapters review network architecture, vertical handoffs, NAT traversals, multipoint extensions, and other areas at the forefront of research. Finally, the text examines various security vulnerabilities and provides perspectives on secure intelligent SIP services with a future outlook on a fraud detection framework in VoIP networks.
Insights from International Researchers
Authored by 65 experts from across the world, this text is sure to advance the field of knowledge in this ever-changing industry and provide further impetus for new areas of exploration. Because of the editors' pivotal influence and their proximity to both the current market and the latest science, this work is certain to become the definitive text on this emerging technology.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part II
TECHNOLOGIES
9
P2P SIP: Network Architecture and Resource Location Strategy
CONTENTS
9.1 Introduction
9.2 Peer-to-Peer Network Technologies
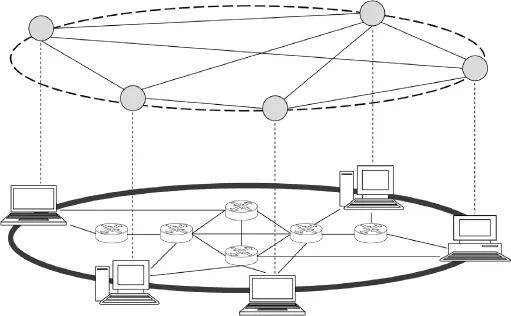
Example of an overlay network.
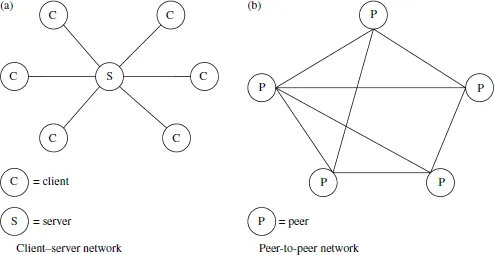
Client-server vs. peer-to-peer network.
9.2.1 Chord
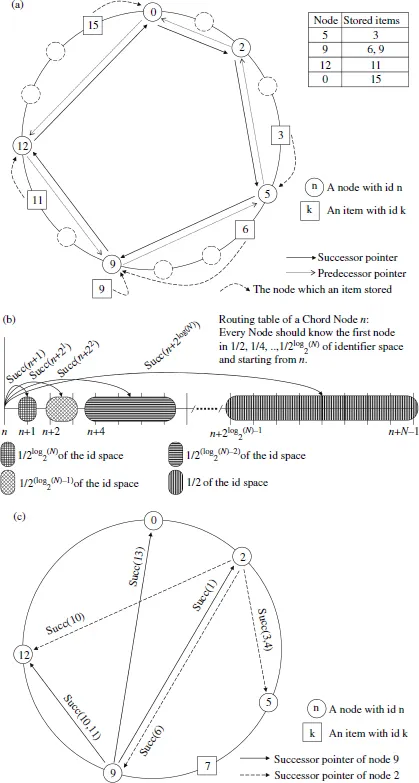
(a) A chord network with N = 16 populated with 6 nodes and 5 items. (b) The general policy for Chord’s routing tables. (c) Example of inserting a new item.
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Table of Contents
- Preface
- Editors
- Contributors
- I Concepts & Services
- II Technologies
- III Security
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app