
eBook - ePub
Available until 4 Dec |Learn more
Digital Watermarking and Steganography
Fundamentals and Techniques
This book is available to read until 4th December, 2025
- 200 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Available until 4 Dec |Learn more
About this book
Every day millions of people capture, store, transmit, and manipulate digital data. Unfortunately free access digital multimedia communication also provides virtually unprecedented opportunities to pirate copyrighted material. Providing the theoretical background needed to develop and implement advanced techniques and algorithms, Digital Watermarking and Steganography:
- Demonstrates how to develop and implement methods to guarantee the authenticity of digital media
- Explains the categorization of digital watermarking techniques based on characteristics as well as applications
- Presents cutting-edge techniques such as the GA-based breaking algorithm on the frequency-domain steganalytic system
The popularity of digital media continues to soar. The theoretical foundation presented within this valuable reference will facilitate the creation on new techniques and algorithms to combat present and potential threats against information security.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Digital Watermarking and Steganography by Frank Y. Shih in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Science General. We have over one million books available in our catalogue for you to explore.
Information
1 Introduction
Digital information and data are transmitted more often over the Internet now than ever before. The availability and efficiency of global computer networks for the communication of digital information and data have accelerated the popularity of digital media. Digital images, video, and audio have been revolutionized in the way they can be captured, stored, transmitted, and manipulated, and this gives rise to a wide range of applications in education, entertainment, the media, medicine, and the military, among other fields [1].
Computers and networking facilities are becoming less expensive and more widespread. Creative approaches to storing, accessing, and distributing data have generated many benefits for the digital multimedia field, mainly due to properties such as distortion-free transmission, compact storage, and easy editing. But free-access digital multimedia communication unfortunately also provides virtually unprecedented opportunities to pirate copyrighted material. Therefore, the idea of using a digital watermark to detect and trace copyright violations has stimulated significant interests among engineers, scientists, lawyers, artists, and publishers, to name a few. As a result, the research in watermark embedding robustness with respect to compression, image-processing operations, and cryptographic attacks has become very active in recent years, and the developed techniques have grown and been improved a great deal.
1.1 Digital Watermarking
Watermarking is not a new phenomenon. For nearly a thousand years, watermarks on paper have been used to visibly indicate a particular publisher and to discourage counterfeiting in currency. A watermark is a design impressed on a piece of paper during production and used for copyright identification (as illustrated in Figure 1.1). The design may be a pattern, a logo, or some other image. In the modern era, as most data and information are stored and communicated in digital form, proving authenticity plays an increasingly important role. As a result, digital watermarking is a process whereby arbitrary information is encoded into an image in such a way as to be is imperceptible to image observers.
Digital watermarking has been proposed as a suitable tool for identifying the source, creator, owner, distributor, or authorized consumer of a document or an image. It can also be used to detect a document or an image that has been illegally distributed or modified. Another technology, encryption, is a process of obscuring information to make it unreadable to observers without specific keys or knowledge. This technology is sometimes referred to as data scrambling. Watermarking, when complemented by encryption, can serve a vast number of purposes including copyright protection, broadcast monitoring, and data authentication.

FIGURE 1.1 A paper watermark.
In the digital world, a watermark is a pattern of bits inserted into a digital media that can identify the creator or authorized users. The digital watermark—unlike the traditional printed, visible watermark—is designed to be invisible to viewers. The bits embedded into an image are scattered all around to avoid identification or modification. Therefore, a digital watermark must be robust enough to survive the detection, compression, and other operations that might be applied upon a document.
Figure 1.2 depicts a general digital watermarking system. A watermark message W is embedded into a media message, which is defined as the host image H. The resulting image is the watermarked image H*. In the embedding process, a secret key K—that is, a random number generator—is sometimes involved to generate a more secure watermark. The watermarked image H* is then transmitted along a communication channel. The watermark can later be detected or extracted by the recipient.
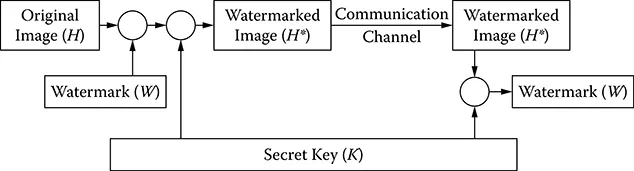
FIGURE 1.2 A general digital watermarking system.
Imperceptibility, security, capacity, and robustness are among the many aspects of watermark design. The watermarked image must look indistinguishable from the original image; if a watermarking system distorts the host image to some point of being perceptible, it is of no use. An ideal watermarking system should embed a large amount of information perfectly securely, but with no visible degradation to the host image. The embedded watermark should be robust with invariance to intentional (e.g., noise) or unintentional (e.g., image enhancement, cropping, resizing, or compression) attacks. Many researchers have been focusing on security and robustness, but rarely on watermarking capacity [2–3]. The amount of data an algorithm can embed in an image has implications for how the watermark can be applied. Indeed, both security and robustness are important because the embedded watermark is expected to be imperceptible and unremovable. Nevertheless, if a large watermark can be embedded into a host image, the process could be useful for many other applications.
Another scheme is the use of keys to generate random sequences during the embedding process. In this scheme, the cover image (i.e., the host image) is not needed during the watermark detection process. It is also a goal that the watermarking system utilizes an asymmetric key, as in public or private key cryptographic systems. (A public key is used for image verification and a private key is needed for embedding security features.) Knowledge of the public key neither helps compute the private key nor allows removal of the watermark.
According to user embedding purposes, watermarks can be categorized into three types: robust, semifragile, and fragile. Robust watermarks are designed to withstand arbitrary, malicious attacks such as image scaling, bending, cropping, and lossy compression [4–7]. They are usually used for copyright protection in order to declare rightful ownership. Semifragile watermarks are designed for detecting any unauthorized modification, while at the same time allowing some image-processing operations [8]. In other words, it is selective authentication that detects illegitimate distortion while ignoring applications of legitimate distortion. For the purpose of image authentication, fragile watermarks [9–13] are adopted to detect any unauthorized modification at all.
In general, we can embed a watermark in two types of domains: the spatial domain or the frequency domain [14–17]. In the spatial domain we can replace the pixels in the host image with the pixels in the watermarked image [7, 18]. Note that a sophisticated computer program may easily detect the inserted watermark. In the frequency domain we can replace the coefficients of a transformed image with the pixels in the watermarked image [19, 20]. (The frequency-domain transformations most commonly used are discrete cosine transform, discrete Fourier transform, and discrete wavelet transform.) This kind of embedded watermark is, in general, difficult to detect. However, its embedding capacity is usually low, since a large amount of data will distort the host image significantly. The watermark must be smaller than the host image; in general, the size of a watermark is one-sixteenth the size of the host image.
1.2 Digital Steganography
Digital steganography aims at hiding digital information into covert channels so that one can conceal the information and prevent the detection of the hidden message. Steganalysis is the art of discovering the existence of hidden information; as such, steganalytic systems are used to detect whether an image contains a hidden message. By analyzing various image features between stego-images (images containing hidden messages) and cover images (images containing no hidden messages), a steganalytic system is able to detect stego-images. Cryptography is the practice of scrambling a message to an obscured form to prevent others from understanding it, while steganography is the practice of obscuring the message so that it cannot be discovered.
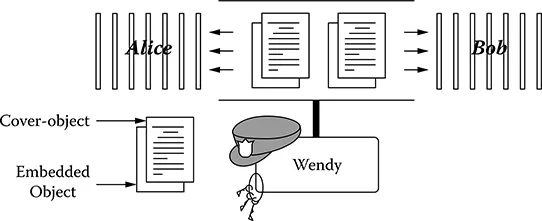
FIGURE 1.3 A classic steganographic model.
Figure 1.3 depicts a classic steganographic model presented by Simmons [21]. In it, Alice and Bob are planning to escape from jail. All communications between them are monitored by the warden Wendy, so they must hide their messages in other innocuous-looking media (cover objects) in order to obtain each others’ stego-images. The stego-images are then sent through public channels. Wendy is free to inspect all messages between Alice and Bob in one of two ways: passively or actively. The passive approach involves inspecting the message in order to determine whether it contains a hidden message and then to conduct a proper action. The active approach involves always altering Bob’s and Alice’s messages even if Wendy may not perceive any traces of hidden meaning. Examples of the active method would be image-processing operations such as lossy compression, quality-factor alteration, format conversion, palette modification, and low-pass filtering.
For steganographic systems, the fundamental requirement is that the stego-image be perceptually indistinguishable to the degree that it does not raise suspicion. In other words, the hidden information introduces only slight modification to the cover object. Most passive wardens detect the stego-images by analyzing their statistic features. In general, steganalytic systems can be categorized into two classes: spatial-domain steganalytic systems (SDSSs) and frequency-domain steganalytic systems (FDSSs). The SDSS [22, 23] is adopted for checking lossless compressed images by analyzing the spatial-domain statistic features. For lossy compressed images, such as a JPEG file, the FDSS is used to analyze frequency-domain statistic features [24, 25]. Westfeld and Pfitzmann have presented two SDSSs based on visual and chi-square attacks [23]. The visual attack uses human eyes to inspect stego-images by checking their lower bit planes, while the chi-square attack can automatically detect the specific characteristic generated by the least-significant-bit steganographic technique.
1.3 Differences Between Watermarking and Steganography
Watermarking is closely related to steganography; however, there are some differences between the two. Watermarking mainly deals with image authentication, whereas steganography deals with hiding data. Embedded watermarking messages usually pertain to host image information, such as copyright, so they are bound with the cover image. Watermarking is often used whenever the cover image is available to users who are aware of the existence of the hidden information and may intend to remove it. Hidden messages in steganography are usually not related to the host image. They are designed to make extremely important information imperceptible to any interceptors.
In watermarking, the embedded information is related to an attribute of the carrier and conveys additional information or properties about the carrier. The primary object of the communication channel is the carrier itself. In steganography, the embedded message usually has nothing to do with the carrier, which is simply used as a mechanism to pass the message. The object of the communication channel is the hidden message. As the applic...
Table of contents
- Cover Page
- Half title
- title
- copy
- dedication
- preface
- ack
- fmchapter
- Preface
- Acknowledgments
- 1 Introduction
- 2 Classification in Digital Watermarking
- 3 Mathematical Preliminaries
- 4 Digital Watermarking Fundamentals
- 5 Watermarking Attacks and Tools
- 6 Combinational Digital Watermarking in the Spatial and Frequency Domains
- 7 Genetic Algorithm-Based Digital Watermarking
- 8 Adjusted-Purpose Digital Watermarking
- 9 Robust High-Capacity Digital Watermarking
- 10 Introduction to Digital Steganography
- 11 Steganalysis
- 12 Genetic Algorithm-Based Steganography