
eBook - ePub
Assessing and Managing Security Risk in IT Systems
A Structured Methodology
- 288 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
This book begins with an overview of information systems security, offering the basic underpinnings of information security and concluding with an analysis of risk management. Part II describes the McCumber Cube, providing the original paper from 1991 and detailing ways to accurately map information flow in computer and telecom systems. It also explains how to apply the methodology to individual system components and subsystems. Part III serves as a resource for analysts and security practitioners who want access to more detailed information on technical vulnerabilities and risk assessment analytics. McCumber details how information extracted from this resource can be applied to his assessment processes.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Assessing and Managing Security Risk in IT Systems by John McCumber in PDF and/or ePUB format, as well as other popular books in Business & Cyber Security. We have over one million books available in our catalogue for you to explore.
Information
II
THE McCUMBER CUBE METHODOLOGY
6: THE McCUMBER CUBE
INTRODUCTION
The McCumber Cube is shorthand for a paper published as “Information Systems Security: A Comprehensive Model,”1 in October 1991. The model itself was also used by the National Security Telecommunications and Information Systems Security Committee (NSTISSC) and published in National Security Telecommunications and Information Systems Security Instruction’s (NSTISSI) National Information Systems Security (INFOSEC) Glossary.2
The McCumber Cube was developed as a response to the attempts in the late 1980s and early 1990s to define the relationship between the communications and computer security disciplines. As the advent of the Internet age dawned, it was clear the distinction made little sense. However, no one was able to adequately portray the systemic interrelation of the components of each.
The development of the McCumber Cube was necessary to define an accurate model not constrained by organizational or technical changes. As with all models, the value lies in its ability to adapt to the information environment irrespective of the specific technologies involved. The model is necessarily three-dimensional to capture the true nature of the interplay of the elements in information systems security. The model is depicted as Figure 6.1.
For many the years, the U.S. government separated the disciplines of communications and computer security. The fundamental reason for this was the preexistence of the communications security infrastructure. Although the need for communications security has existed since the emergence of interpersonal communications, the modern era of technical communications security was the result of offensive and defensive operations in World War II. The well-documented evolution of technical cryptography and the exploitation of encrypted communications spawned an extensive and technically complex environment of policies and products championed by the NSA.
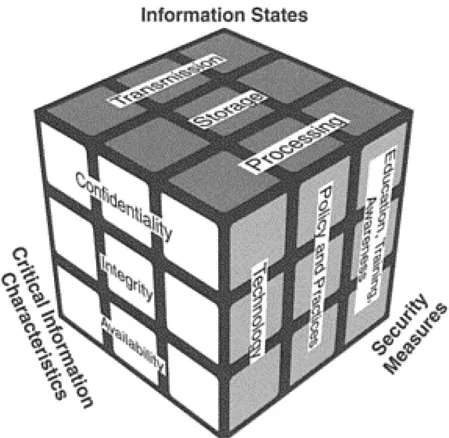
Figure 6.1 McCumber Cube Model
One of the vital insights of World War II cryptography was that reliance on the cryptographic algorithm itself for protecting sensitive or classified communications was inadequate. By analyzing a captured German Enigma encryption machine from a sunken U-boat, British and U.S. researchers were able to ultimately determine the encryption key and decrypt highly sensitive German military message traffic. The lesson was not lost on the Allies. From that time on, the cryptographic key became the focus for protecting our own communications system.
As computers and other computational resources evolved into critical defense technologies in the 1950s and 1960s, it became obvious that security for these new machines was critical. They were used to calculate weapons systems data, atomic and nuclear specifications, and geographic information used by military planners and weapons systems developers. At first, it was adequate to shield the stand-alone systems themselves for their classified computational missions. These early systems were also used for computationally intensive cryptographic calculations to either help reinforce our own cryptosystems or crack the codes of other nation-states.
Soon, however, access to computer systems was exploding as universities, research firms, and private industry all demanded automated processing of large amounts of data. As these capabilities moved outside the confines of sensitive military and government organizations, they became powerful tools for a quickly expanding industrial base as well. The lessons of World War II cryptography told us not to place our security emphasis on the machines, but on the key that unlocks access to the information itself.
The U.S. government endeavored to address computer security as a discipline distinct from the existing communications security infrastructure. Many people involved in the early development of computer security policy and practice felt there was a significant distinction between the two disciplines and skills were not easily shared among the various research and deployment teams. So for many years, computer security researchers toiled in facilities and organizations separate from the communications security environment.
With the early advance of intercomputer communications, it became apparent to everyone in government circles that the two disciplines had to be integrated. Computers communicate. Communication systems compute. The evolution of technology has long since eliminated any arbitrary distinction between a computer and its communication components or a communications network and its computing system. The same is true for the security disciplines. Merely combining the COMSEC and COMPUSEC disciplines under an umbrella of common management is unacceptable.
Even if we address the other, albeit less technical, aspects of information systems security such as policy, administration, and personnel security, we still fail to develop a comprehensive view of this evolving technology. The reason for this becomes clear when we are reminded it is the information that is the cornerstone of information systems security. In this sense, any paradigm that emphasizes the technology at the expense of information will be lacking.
THE NATURE OF INFORMATION
The key element of the McCumber Cube is its reliance on an information-centric model. Both communications and computer systems are developed for some functions of information management. Defining the nature of information could be a tedious task. To some it represents the free-flowing evolution of knowledge; to others, it is intelligence to be guarded. Add to this the innumerable media through which information is perceived and we have a confusing array of contradictions. How can we present a study of information that has universal application?
It may be best to develop a simple analogy. The chemical compound H2O means many things to all of us. In its liquid state, water means life-giving sustenance to a desertdwelling Bedouin; to a drowning victim, it is the vehicle of death. The same steam we use to prepare vegetables can scald an unwary cook. Ice can impede river-borne commerce on the Mississippi River or make a drink more palatable. Science, therefore, does not deal with the perception of the compound, but with its state.
As the compound H1O can be water, ice, or steam, information has three basic states; at any given moment, information is being transmitted, stored, or processed. The three states exist irrespective of the media in which information resides. This subtle distinction ultimately allows us to encompass all information systems technology in our model.
It is possible to look at the three states in microcosm and say that processing is simply specialized state combinations of storage and transfer; so, in fact, there are only two possible states. By delving to this level of abstraction, however, we go beyond the scope and purpose of the model. The distinction between the three states is fundamental and necessary to accurately apply the model. For example, cryptography can be used to protect information while it is transferred through a computer network and even while it is stored in magnetic media. However, the information must be available in plaintext (at least to the processor) for the computer to perform the processing function. The processing function is a fundamental state that requires specific security controls.
When this information is needed to make a decision, the end user may not be aware of the number of state changes effected. The primary concern will be certain characteristics of the information. These characteristics are intrinsic and define the security-relevant qualities of the information. As such, they are the next major building block of our information systems security model.
CRITICAL INFORMATION CHARACTERISTICS
Information systems security concerns itself with the maintenance of three critical characteristics of information—confidentiality (Pfleeger’s secrecy), integrity, and availability.3 These attributes of information represent the full spectrum of security concerns in an automated environment. They are applicable for any organization irrespective of its philosophical outlook on sharing information.
CONFIDENTIALITY
Confidentiality is the heart of any security policy for an information system. A security policy is the set of rules that, given identified subjects and objects, determines whether a given subject can gain access to a specific object.4 In the case of discretionary access controls, selected users (or groups) are controlled as to which data they may access. Confidentiality is then the assurance that access controls are enforced. The reason I prefer the term confidentiality to secrecy is merely to avoid unwarranted implications that this is solely the domain of armies and governments. As we will see, it is a desirable attribute for information in any organization.
All organizations have a requirement to protect certain information. Even owners of a clearinghouse operation or Web site need the ability to prevent unwanted access to supervisory functions within their systems. It is also important to note that the definition of data that must be protected with confidentiality controls is broadening throughout government.5 Actual information labeling and need-to-know imperatives are aspects of the system security policy that are enforced to meet confidentiality objectives. The issue of military versus civilian security controls is one that need not impact the development of a comprehensive representation of information systems security principles.
INTEGRITY
Integrity is perhaps the most complex and misunderstood characteristic of information. Government seems to have a better foundation in the development of confidentiality controls than those that ensure data integrity. Some texts define integrity as “assets (which) can only be modified by authorized parties.”3 Such a definition unnecessarily confines the concept to one of access control.
I propose a much broader definition. Data integrity is a matter of degree (as is the concept of trust as applied to trusted systems), which has to be defined as a quality of the information and not as who does or does not have access to it. Integrity is that quality of information that identifies how closely the data represents reality. How closely does your resume reflect you? Does a credit report accurately reflect an individual’s historical record of financial transactions? The definition of integrity must include the broad scope of accuracy, relevancy, and completeness.
Data integrity calls for a comprehensive set of functions to promote accuracy and completeness as well as security. This is not to say that too much information cannot be a problem. Data redundancy and unnecessary records present a variety of challenges to system implementers and administrators. The users must define their needs in terms of the information necessary to perform certain functions. Information systems security functions help ensure this information is robust and (to the degree necessary) reflects the reality it is meant to represent.
AVAILABILITY
Availability is a coequal characteristic with confidentiality and integrity. This vital aspect of security ensures the information is provided to authorized users when it is requested or needed. Often it is viewed as a less technical requirement that is satisfied by redundancies within the information system such as backup power, spare data channels, and parallel databases. This perception, however, ignores one of the most valuable aspects of our model that this characteristic provides. Availability is the check-and-balance constraint on our model. Because security and utility often conflict, the science of information systems security is also a study of subtle compromises.
As well as ensuring system reliability, availability acts as a metric for determining the extent of information system security breaches. Ultimately, when information systems security preventive measures fail, remedial action may be necessary. This remedial activity normally involves support from law enforcement or legal departments. To pursue formal action against people who abuse information systems resources, the ability to prove an adverse impact often hinges on the issue of denying someone the availability of information resources. Although violations of information confidentiality and integrity can be potentially more disastrous, denial of service criteria tend to be easier to quantify and thus create a tangible foundation for taking action against violators.
The triad of critical information characteristics covers all aspects of security-relevant activity within the information system. By building a matrix with the information states positioned along the horizontal axis and the critical information characteristics aligned down the vertical, we have the foundation for the model.
SECURITY MEASURES
We have now outlined a matrix that provides us with the theoretical basis for our model. What it lacks is a view of the measures we employ to ensure the critical information characteristics are maintained while information resides in or moves between states. It is possible, at this point, to perceive the chart as a checklist. At a high level of abstraction, one could assess the security posture of a system by using this approach. By viewing the interstices of the matrix as representing system vulnerabilities, you can attempt to determine the security aspects of an information system as categorized by the nine intersection areas. For example, you may single out information confidentiality during transmission or any intersection area for scrutiny.
The two-dimensional matrix also has another less obvious utility. We can map various security technologies into the nine interstices. Using our example from above, we note that it is necessary to protect the confidentiality of the information during its transmission state. We can then determine which security technologies help ensure confidentiality during transmission of the information.
In this case, cryptography would be considered a primary security technology. We can then place various cryptographic techniques and products within a subset in this category. Then we repeat the process with other major types of technology that can be placed within this interstice. The procedure is repeated for all nine blocks on our grid. Thus we form the first of three layers that will become the third dimension of our model-security measures.
TECHNOLOGY
The technology layer will be the primary focus of the third dimension. We will see that it provides the basis for the other two layers. For our purposes, we can define technology as any physical device or technique implemented in physical form that is specifically used to ensure that the critical information characteristics are maintained through any of the information states. Technology can be implemented in hardware, firmware, or software. It could be a biometric device, cryptographic module, or security-enhanced operating system. When we think of a thing that could be used to protect the critical characteristics of information, we are thinking of technology.
Usually, organizations are built around functional responsibilities. The advent of computer technology created the perception that a group needed to be established to accommodate the new machines that would process, store, and transmit much of our vital information. In other words, the organization was adapted to suit the evolving technology. Is this wrong? Not necessarily; however, it is possible to create the impression that technology exists for technology’s sake.
Telecommunications and computer systems are simply media for information. The media need to be adapted to preserve certain critical characteristics with the adaptation and use of the information media (technology). Adaptation is a design problem, but use and application concerns bring us to the next layer.
POLICY AND PRACTICE
The second layer of the third dimension is that of policy and practice. It is the recognition of the fact that information systems security is not just a product that will be available at some future date. Because of our technology focus, it is easy to begin to think of security solutions as devices or add-on packages for existing information systems. We are often guilty of waiting for technology to solve a problem that is not solely a technological problem. An enforceable (and enforced) policy can aid immeasurably in protecting information.
A study has shown that 75 percent of federal agencies do not have a policy for the protection of information on PC-based information systems.5 Why, if it is so effective, is policy such a neglected security measure? It may be due in part to the evolving social and moral ethic with regard to our use of information systems. The proliferation of unauthorized software duplication is just another symptom of this problem. Even though software companies have policies and licensing caveats on their products, sanction...
Table of contents
- COVER PAGE
- OTHER INFORMATION SECURITY BOOKS FROM AUERBACH
- TITLE PAGE
- COPYRIGHT PAGE
- DEDICATION
- INTRODUCTION
- I SECURITY CONCEPTS
- II THE MCCUMBER CUBE METHODOLOGY
- III APPENDICES