
eBook - ePub
Database and Applications Security
Integrating Information Security and Data Management
- 656 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Database and Applications Security
Integrating Information Security and Data Management
About this book
This is the first book to provide an in-depth coverage of all the developments, issues and challenges in secure databases and applications. It provides directions for data and application security, including securing emerging applications such as bioinformatics, stream information processing and peer-to-peer computing. Divided into eight sections,
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1: Introduction
1.1 Trends
Recent developments in information system technologies have resulted in computerizing many applications in various business areas. Data has become a critical resource in many organizations, and, therefore, efficient access to data, sharing the data, extracting information from the data, and making use of the information has become an urgent need. As a result, there have been many efforts on not only integrating the various data sources scattered across several sites, but extracting information from these databases in the form of patterns and trends has also become important. These data sources may be databases managed by database management systems, or they could be data warehoused in a repository from multiple data sources.
The advent of the World Wide Web (WWW) in the mid-1990s has resulted in even greater demand for managing data, information, and knowledge effectively. There is now so much data on the Web that managing it with conventional tools is becoming almost impossible. New tools and techniques are needed to effectively manage this data. Therefore, to provide interoperability as well as warehousing between the multiple data sources and systems, and to extract information from the databases and warehouses on the Web, various tools are being developed.
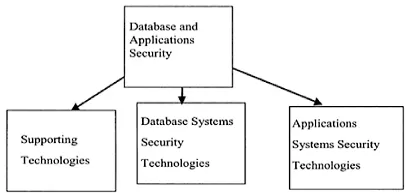
Figure 1.1 Components of database and applications security
As the demand for data and information management increases, there is also a critical need for maintaining the security of the databases, applications, and information systems. Data and information have to be protected from unauthorized access as well as from malicious corruption. With the advent of the Web it is even more important to protect the data and information as numerous individuals now have access to this data and information. Therefore, we need effective mechanisms for securing data and applications.
This book reviews the developments in data and applications security with a special emphasis on database security. Then it provides directions for data and applications security. These directions include securing semantic Webs as well as emerging applications such as E-commerce, knowledge management, and sensor information processing. Figure 1.1 illustrates the various technologies discussed in this book.
The organization of this chapter is as follows. In each of Sections 1.2 through 1.11 we elaborate on the various parts addressed in this book. For example, supporting technologies for database security are discussed in Section 1.2. Access control and discretionary security issues are the subject of Section 1.3. Multilevel secure databases are addressed in Section 1.4. Aspects of multilevel secure relational data models and systems are discussed in Section 1.5. The inference problem is the subject of Section 1.6. Secure distributed databases are discussed in Section 1.7. Secure object and multimedia systems are discussed in Section 1.8. Data warehousing, data mining, security, and privacy are discussed in Section 1.9. Secure Web information systems are the subject of Section 1.10. Some emerging data security technologies such as secure sensor information management and digital identities are discussed in Section 1.11. Finally in Section 1.12 we discuss a framework for database and applications security and discuss the organization of this book. Some final thoughts are given in Section 1.13.
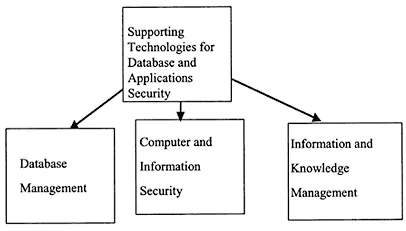
Figure 1.2 Supporting technologies for database and applications security
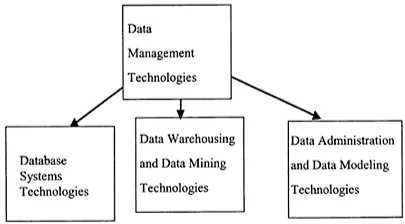
Figure 1.3 Data management technologies
1.2 Supporting Technologies for Database and Applications Security
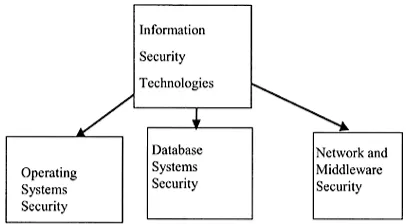
Figure 1.4 Information security technologies
As illustrated in Figure 1.2, database and applications security have evolved from database technologies, computer security technologies, and many other technologies including objects, distributed systems, information management, and applications such as medical informatics. Database technologies are illustrated in Figure 1.3. These include database systems, data modeling, data warehousing, and data mining. Information security technologies include operating systems security, network security, database security, middleware security, and Web security and are illustrated in Figure 1.4. Other technologies include almost every information management technology such as multimedia, knowledge management, and many more, and are illustrated Figure 1.5.
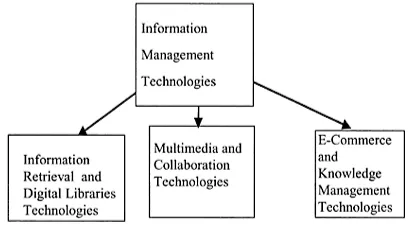
Figure 1.5 Information management technologies
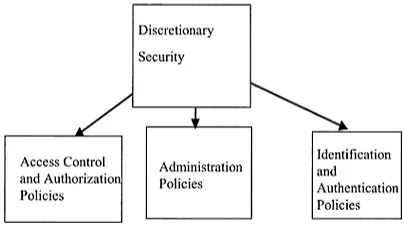
Figure 1.6 Discretionary security
Part I of this book discusses in more detail database system technologies, information security technologies, and some of the other information management technologies. Because we are dealing with many “other technologies” we also discuss these other technologies as needed throughout the book. Note that data management is much broader than database systems. That is, data management includes database systems as well as data administration aspects. An evolution of database systems technologies is discussed in Appendix A.
1.3 Discretionary Security in Database Systems
Discretionary security deals with granting access to the data depending on the users, user groups, and other factors such as roles of users. Discretionary security was initially investigated for secure operating systems where access was granted to files depending on the kinds of processes. The types of access included read and write operations. Then the concept was extended to databases where access was granted, say, to relations, attributes, and elements. Now discretionary security also includes handling complex security policies, granting access to data based on roles and functions, and also both positive and negative authorization policies. Figure 1.6 illustrates various types of discretionary access control mechanisms.
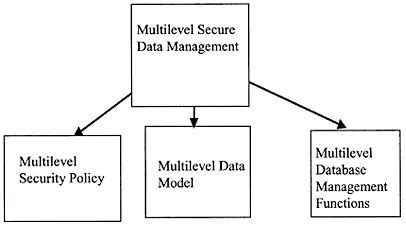
Figure 1.7 Multilevel secure data management
Articles on discretionary security for database systems have consistently appeared since the mid-1970s. The field is still evolving as new models and paradigms are discovered. Furthermore as new kinds of systems emerge including multimedia systems, medical information systems, and E-commerce systems, discretionary security policies have been expanded and adapted.
1.4 Multilevel Secure Data Management
Numerous developments on multilevel secure database systems were reported throughout the 1980s and during the early 1990s. These systems evolved from multilevel secure operating systems. The idea is for users to be granted access to the data depending on the user’s clearance level and the sensitivity level of the data. For example, data is assigned sensitivity levels such as Unclassified, Confidential, Secret, and Top-Secret. Users are also cleared, say, at Confidential, Secret, and Top-Secret levels. In addition, there may also be compartments both for data and the users.
The early developments focused on multilevel secure relational database systems. Then the focus was on multilevel object database systems and multilevel distributed database systems. In Part III we focus mainly on historical developments and design principles. Specific multilevel secure database systems as well as the inference problem in such systems are discussed in Parts IV through VII. Figure 1.7 illustrates various aspects of multilevel secure data management.
1.5 Multilevel Secure Relational Data Models and Systems
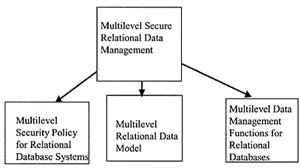
Figure 1.8 Multilevel secure relational data management
Many of the early developments especially throughout the 1980s and early 1990s were in multilevel secure relational data models and systems. For example, after the Air Force Summer Study, various prototypes based on the integrity lock approach for relational models were developed at the MITRE Corporation. Then there were the prominent multilevel secure relational database systems such as SeaView at SRI and LOCK Data Views at Honeywell Inc. In the early 1990s there was work at George Mason University on multilevel relational data models. At the same time, multilevel secure relational database systems based on a distributed systems approach were being designed at the Naval Research Laboratory.
In Part IV we discuss multilevel relational data models and the functions of a multilevel secure relational database system, as well as prototype developments and commercial products. Note that there are many commercial products, and some corporations are still maintaining their multilevel database system products. Figure 1.8 illustrates multilevel secure relational database technologies.
1.6 Inference Problem
Inference is the process of posing queries and deducing unauthorized information from the legitimate responses received. The inference problem exists for all types of database systems and has been studied extensively within the context of multilevel databases. Early developments on the inference problem focused on statistical database security. Then the focus was on security constraint processing to handle the inference problem. Researchers also used conceptual structures to design the database application and detect security violations via inferences during the design time. There are many technical challenges for the inference problem including the unsolvability and the complexity of the problem. The developments on the inference problem are illustrated in Figure 1.9. We discuss the inference problem in Part V.
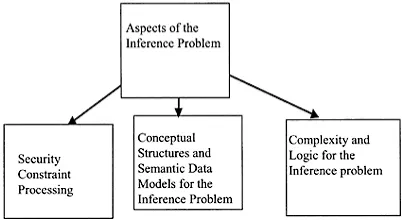
Figure 1.9 Aspects of the inference problem
Recently the inference problem is receiving much attention within the context of privacy. Technologies such as data mining are being used extensively for national security. This is causing privacy concerns. The privacy problem is a form of the inference problem where one deduces highly private information from public information. The privacy problem is discussed in Part VIII.
1.7 Secure Distributed Database Systems
Distributed database technology has a...
Table of contents
- Cover Page
- Title Page
- Copyright Page
- Dedication
- Foreword
- Preface
- Acknowledgments
- About the Author
- Chapter 1: Introduction
- I: Supporting Technologies for Database and Applications Security
- II: Discretionary Security for Database Systems
- III: Mandatory Security for Database Systems
- IV: Multilevel Secure Relational Database Systems
- V: The Inference Problem
- VI: Secure Distributed and Heterogeneous Database Systems
- VII: Secure Object and Multimedia Systems
- VIII: Data Warehousing, Data Mining, Security, and Privacy
- IX: Secure Web Data and Information Management Tcchnologies
- X: Emerging Secure Data Management Technologies and Applications
- Appendix A: Data Management Systems: Developments and Trends
- Appendix B: Suggested Reading: Books in Database Systems and Information Security
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Database and Applications Security by Bhavani Thuraisingham in PDF and/or ePUB format, as well as other popular books in Computer Science & Cyber Security. We have over one million books available in our catalogue for you to explore.