
- 296 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
How to Build a Cyber-Resilient Organization
About this book
This book presents a standard methodology approach to cyber-resilience. Readers will learn how to design a cyber-resilient architecture for a given organization as well as how to maintain a state of cyber-resilience in its day-to-day operation. Readers will know how to establish a state of systematic cyber-resilience within this structure and how to evolve the protection to correctly address the threat environment. This revolves around the steps to perform strategic cyber-resilience planning, implementation and evolution. Readers will know how to perform the necessary activities to identify, prioritize and deploy targeted controls and maintain a persistent and reliable reporting system.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access How to Build a Cyber-Resilient Organization by Dan Shoemaker,Anne Kohnke,Ken Sigler in PDF and/or ePUB format, as well as other popular books in Computer Science & Cyber Security. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
It’s Time for a New Paradigm
Following this chapter, the reader will understand
- the role and importance of cyber resilience in protecting organizations;
- the differences between cybersecurity and cyber resilience;
- the standard steps of the cyber-resilient approach;
- the concerns and issues associated with our cybersecurity;
- the general structure and intent of a cyber-resilient architecture;
- the large steps to implement formal cyber-resilient processes.
Introduction to the Book
Two decades of data make it clear that conventional cybersecurity doesn’t work (Symantec, 2014; Trend-Micro, 2015; PRC, 2016). Hence, this book offers an entirely new and different approach, one that is both resource efficient and one which ensures that the organization will continue to survive, no matter how destructive the attack. We call this approach “cyber resilience.” Cyber resilience is not the same thing as cybersecurity. Cyber resilience ensures the absolute protection of just those functions that are vital to the organization’s survival.
This chapter will introduce the general principles and concepts of cyber resilience as well as the standard methodology and contextual activities that guide the implementation of a strategically sound cyber-resilient architecture. We will detail the fundamental phases involved and the best practices that must be implemented in each of the phases of a classic cyber resilience process. These phases build upon each other in a collective fashion and proper execution of each is integral to the assurance of organizational resiliency.
Organizational resilience is important because the increasing presence of advanced cyber threats makes it inevitable that every organization will ultimately be targeted (OAS, 2015). Cyber resilience recognizes that there are too many cutting-edge hacking tools to prevent sophisticated attackers from finding the cracks in even the most robust cybersecurity perimeter (Lois, 2015). Thus, there is a need for a new paradigm.
Cyber resilience requires the organization to spend whatever it takes to develop a well-defined and explicit set of controls to ensure the survival of just those critical elements that cannot be subjected to compromise. The controls must assure provable protection of core functionality and the various interdependencies in the enterprise’s ecosystem (EY, 2014). The concept of cyber resilience goes far beyond the classic boundaries of better access controls (EY, 2014). Instead, organizations establish a “cyber resilience strategy and architecture” that give them the ability to withstand and recover rapidly from disruptive events (EY, 2014).
Practically speaking, the best argument for cyber resilience is that it concentrates resources where they will make the most difference. This is particularly germane to national security in that any attack on an infrastructure element threatens a lot more than simple business processes (Conklin, Shoemaker, Kohnke, 2017). Thus, cyber resilience is a particularly significant aspect of ensuring survival and easing recovery of the critical systems that underwrite our way of life.
In general, it is our belief that very little substantive thinking has taken place when it comes to devising a specific and generally reliable approach to protecting the nation’s critical infrastructure. This is partly because there is no practical process that explicitly dictates how to reliably protect critical infrastructure components. The ideas presented here are a start toward eventually overcoming this lack of planning.
Readers will understand the ultimate reasons why cyber resilience provides more robust assurance for the organization. They will also discover the role that conventional strategic management plays in the creation and maintenance of an effective cyber-resilient architecture. Finally, the last chapter of this book will describe the practical means for operating an organization in a cyber-resilient state.
Why Cyber Resilience Is Critically Important
Count on it—the next world war is going to start with the click of a mouse, not a wave of bombers. The attacker will send a command to the computers that control key elements of our critical infrastructure, and most of our way of life will be blasted back to the 18th century. Could this really happen? Two decades of data say that it is not only possible, but that it will indeed take place. In fact, we have struggled with this problem almost from the beginning of the internet. But the trend is always in one direction: “One massive hack after another” (Gamer, 2015). Worse, data indicates that conventional cybersecurity approaches will never be able to successfully protect us (Symantec, 2014; Trend-Micro, 2015, PRC, 2016).
Cyberspace is full of adversaries. Potential actors range from state-sponsored groups through criminal enterprises to any wacko with an internet link. So, cyberattacks on the various elements of the U.S. critical infrastructure are a daily fact of life. For instance, the Industrial Control Systems-Computer Emergency Response Team (ICS-CERT) reports that U.S. industrial control systems were attacked at least 245 times over a 12-month period (OAS, 2015). “While China, the U.S. and Russia lead the world in cyber-attacks, virtually every government engages in such attacks, and nearly every country has its share of computer hackers” (Wagner, 2017). So, forget aircraft carriers, the ability to launch a successful cyberattack makes every nation-state into a potential superpower (Wagner, 2017).
So far, the problems have been elsewhere. Perhaps the most egregious example comes from Ukraine. In December 2015, a presumed Russian cyberattacker successfully seized control of the Prykarpattyaoblenergo Control Center (PCC) in the Ivano-Frankivsk region of Western Ukraine (Wagner, 2017). The attack marked the first time that a concerted cyberattack was successfully launched against a nation’s power grid (Wagner, 2017). However, Stuxnet, in 2010, might be the first instance of “a nation enforcing policy through other means,” to paraphrase Von Clausewitz (Clausewitz, Chapter 1, Section 4, 1976).
Worse, the perpetrators of the Ukrainian attack were observed conducting similar exploits against the U.S. energy sector (Brasso, 2016). Although there was never any actual disruption, many experts believe that those activities were a probe for future moves on the U.S. infrastructure (Brasso, 2016). Consequently, in the larger sense, the key question is “could a catastrophic cyberattack in the U.S. infrastructure ever occur?” The National Security Agency’s former Director, Mike Rodgers, made his own evaluation of the possibility of a successful attack against critical infrastructure when he said: “it’s a matter of, when, not if” (Smith, 2014).
Power grids are the most frequently mentioned targets (Wagner, 2016; Brasso, 2016; Smith, 2014). This is because the interconnectedness of power grids opens them up to “cascading failures.” That is, as nearby grids take up the slack for a failed grid system, they overload and fail themselves and cause a chain reaction. Rogers says that such attacks are part of “coming trends” in which so-called zero-day vulnerabilities in U.S. cyber systems are exploited (Smith, 2014).
The reason why the protection of our national infrastructure is so critically important is that a major exploit, like a successful cyberattack on the electrical grid, could leave the U.S. cloaked in darkness, unable to communicate and without any form of 21st century transport. It would likely kill many thousands of citizens, perhaps millions, either through civil unrest, failure of public systems, or mass starvation (Brasso, 2016; Maynor and Graham, 2006).
Many experts believe that the cyberwar began in 2003 (Wagner, 2017). This was when the Northeast (U.S.) blackout occurred and caused 11 deaths and an estimated $6 billion in economic damages (Wagner, 2017). After that attack, SCADA (supervisory control and data acquisition) attacks occurred in the UK, Italy, and Malta, among others. According to Dell’s 2015 Annual Security Report, cyberattacks against infrastructure systems doubled in 2014 to more than 160,000 (Wagner, 2017).
Infrastructure Is the Target
Infrastructure systems are diverse. This diversity and the criticality of the sensors and controllers that comprise a typical infrastructure system make them tempting targets for attack. Therefore, there have been long-standing concerns about the overall digital infrastructure being vulnerable to cyberwarfare and cyberterrorism attacks (Eisenhauer et al., 2006; Nat-Geo, 2017). Nevertheless, notwithstanding the disastrous nature of cyberattacks on digital targets, none of the industries in our current national infrastructure have developed coherent plans or effective strategies to protect themselves (Brasso, 2016). This is the reason why there is increasing interest in a coherent model for defending the critical infrastructure against cyberattack (Symantec, 2014; EY, 2014).
The approach we are going to discuss here is particularly suited to ensuring the continuing survivability of infrastructure systems. This is because the focus is on maintaining core functionality rather than protecting data. The idea is to only lightly defend less critical or peripheral elements while ensuring the survival of the system. This strict emphasis on survivability versus data protection is the reason why cyber resilience, versus cybersecurity, is the approach of choice for critical systems.
A New Paradigm for Ensuring Our Way of Life
This book offers an entirely new and different paradigm. Cyber resilience ensures the absolute security and reliability of just those critical functions, which the organization needs to continue to survive and carry out its mission. Carl von Clausewitz sums up the role of strategy in this way: “Strategy is the necessary response to the inescapable reality of limited resources” (Clausewitz, 1989). In short, no General ever has the luxury of overwhelming numbers or unlimited resources. So, s/he needs to adopt an approach that is likely to succeed, given the assets that are available at the time of battle. In this respect, Clausewitz posits that a successful strategy finds the most advantageous point to concentrate all the resources necessary to achieve the primary goal, which is to win the battle even if some of the lesser objectives are not achieved (Clausewitz, 1989).
Cybersecurity is the inheritor of the old information assurance mission. Accordingly, cybersecurity is still based around creating and ensuring a protection perimeter. This perimeter is shaped by assuring all logical points of access to the protected space that lies within that boundary. Since the protection perimeter of even a small organization can involve numerous points of access, electronic, physical and human, that task normally requires an extensive resource commitment to be even be remotely successful.
Whereas, cyber resilience only ensures those organization elements that are deemed critical to system survival. The requirement to maintain the functioning of a few critical components is less resource intensive than the need to ensure the confidentiality, integrity, and availability of all assets within secure space. Therefore, cyber resilience is much more resource efficient. The narrowing of scope allows protection measures to be concentrated onto a far smaller attack surface, which notionally ensures more effective protection for the things that simply can’t be allowed to fail.
Operationalizing Cyber Resilience: Saltzer and Schroeder’s Principles
Cyber resilience is founded on classification, prioritization, and comprehensive strategic policy-based deployment of a rigorous set of real-world security controls (Symantec, 2014). Cyber resilience requires the creation of a set of well-defined processes, which react to penetrations of the organizational perimeter by locking down the asset they are designed to protect (US-CERT, 2016). These protection processes are both electronic and behavioral in focus and they are designed to protect key assets as well as ensure optimum recovery of the overall system in the event of successful attack (Symantec, 2014).
Saltzer and Schroeder arguably laid down the basis for cybersecurity design in their founding principles (Saltzer, 1974). The concept of cyber resilience hinges on four of Saltzer and Schroeder’s lesser-known principles. Most people in cybersecurity know about and practice design concepts such as Least Privilege, Complete Mediation, Separation of Duties, and Psychological Acceptability. Figure 1.1 lists four principles that are generally not as prevalent and underlie the cyber resilience approach (Saltzer, 1974):
- Economy of mechanism: Keep the design as simple and small as possible.
- Work factor: The cost must be greater than the potential attacker is willing to commit.
- Least common mechanism: Minimize the amount of mechanism common to all users.
- Compromise recording: Reliably record the actions of a compromise.
Economy of mechanism advises the construction of simple strongpoints around critical assets rather than basing the protection on the complexities of comprehensive perimeter access control. In conventional military tactics, a strongpoint is a key position, which is very difficult to overrun or avoid. With respect to illustrating the difference between cyber resilience and cybersecurity, perhaps the best practical example would be that a strongpoint is like locking critical assets in a safe rather than protecting them by assuring access to the building they are in, which is perimeter access control.
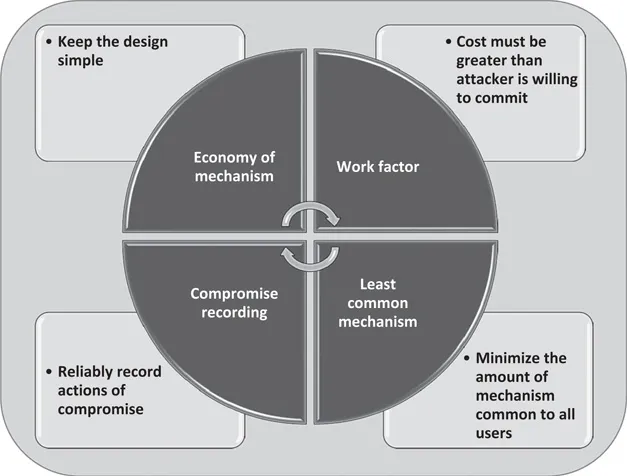
Figure 1.1 Saltzer and Schroeder’s lesser-known cyber principles.
In military doctrine, strongpoints are arrayed in mutually supporting, defense-in-depth mesh arrangements, called hedgehogs, rather than formed into a contiguous line of increasingly rigorous perimeter access controls. The hedgehog arrangement implements the principle of least common mechanism in that strongpoint defenses are tailored to just the threats affecting the protection target. This allows for very straightforward simplicity in the design. It also allows the organization to maximize security resources by building up the capabilities of only the protection for the critical features rather than diffusing the investment by attempting to protect everything.
Most importantly, if the strongpoint protecting the critical assets are robust enough, they will be too expensive for the attacker to assault. So, the attacker will be shepherded to more vulnerable targets and that brings us to the work factor principle in operation.
Work factor also serves to maximize the defender’s rapid response capability. In effect, organizations will be able to rapidly concentrate their resources at the point of attack, knowing that the essential functions are protected. Since the critical system protection, e.g., strongpoint positions, will be bypassed due to their impossibly high work factor rate, the organization will be able to concentrate its resources on the recovery of noncritical functions and information.
Finally, the organization will be able to deploy and conduct the most effective recovery possible because information from prior incidents will be available to planners and responders to help optimize the response. This is the intent of the compromise recording principle. The effect of an attack on a nonessential resource can be minimized through lessons learned from prior attacks. Additionally, the road to recovery can be planned because the execution and outcomes of the attack have been recorded for study.
Tactics One and Two: Economy of Mechanism and Work Factor
Cyber resilience involves the formulation of well-defined strategies and the implementation of rigorous strongpoint countermeasures, which are designed to inflict unsustainable work factor requirements on an attacker. Consequently, the most important thing the organization needs to know is: “Exactly how many strongpoints will I need to build and exactly how much investment will be required to make each strongpoint infeasible to attack?” It should be possible to identify all those organizational functions that are too critical for the organization to lose and still stay in business. This involves a strategic planning process and accordingly, the organization should then concentrate sufficient resources to ensure that those specific protection targets always demand too great an investment on the attacker’s part. Thus, cyber-resilient architectures are founded on making decisions about what that or...
Table of contents
- Cover
- Half Title
- Series Page
- Title Page
- Copyright Page
- Table of Contents
- Foreword
- Preface
- Authors
- 1 It’s Time for a New Paradigm
- 2 Asset Identification and Classification
- 3 Establishing the Risk Status of the Corporate Infrastructure
- 4 Prioritization of Assets and Establishing a Plan for Resilient Change
- 5 Control Design and Deployment
- 6 Control Assessment and Assurance
- 7 Recovering the Non-Priority Assets
- 8 Ensuring a Continuously Cyber-Resilient Organization
- Index