Perhaps you’re an IT executive who has been working in the field for a number of years. You have a reasonably good idea of how security works in the traditional data center, and you’ve begun to wrap your head around the particulars of security as it’s applied to virtual servers and storage appliances. When it comes to the cloud, though, you heard early on that security was a problem and you haven’t really been able to dive into the subject deeply enough to decide whether that impression is correct or just convenient. Now, your users and the rest of the management team is bringing up the cloud every time an IT problem is mentioned. You’ve decided that you need to get a handle on just how secure your data would be in the cloud, but you don’t know where to start.
We even wrote this book for you
A reasonable person could reasonably ask how we intend to make one book meet the needs of all these different people. The answer is that we take the position that everyone reading this book is smart and curious. Everyone reading this book has some basic knowledge about computers and networks. And everyone reading this book deserves to have the information laid out in terms that use jargon as little as possible and build on basic concepts until we’ve conveyed what you need to know about security of, by, and for the cloud. Now, it’s also important for you to understand what this book won’t do for you.
If you’re looking for a book that contains a lot of programming examples and configuration files that can be copied into routers and firewalls, then you really should expand your search. If you’re looking for a book that prepares you for a particular certification exam, with specific answers and practice exams, then there are other titles that will better suit your needs. If, on the other hand, you’d like to know what some of the leading experts in the field think about the current state of cloud computing security and its likely future; if you’re looking for something that will let you hold your own in a discussion of cloud computing security; or if you want to be able to fine-tune the level of your nonsense detector when people are coming at you with cloud security claims, then sit back, settle in, and grab your favorite beverage. It’s time to get started on the book that is absolutely the right one for you.
Companies and organizations care so deeply about cloud security because they are adopting the cloud in large and growing numbers. What kind of numbers? According to a report by Cisco®,2 by 2014, more than half of all data loads (and in this case we’re talking about business information processing) will be processed in cloud computing centers, and only a minority will be processed in traditional data centers. If companies are going to move a growing percentage of their processing to a cloud computing architecture, it makes sense that their interest in securing the data that lives outside their traditional data center would increase apace.
Among the reasons given for a reluctance to go to the cloud, security concerns frequently top the list. As cloud deployments have expanded, cloud storage and applications have become part of infrastructures that fall under regulatory control, leading many IT professionals to wonder how, or if, the cloud can be considered sufficiently secure to meet regulatory compliance muster. If cloud computing were still experimental rather than a part of mainstream enterprise IT, this reticence would have little overall impact. As it is, though, individuals who have an incomplete or mistaken understanding of the security issues within cloud computing may find themselves placing their organizations at a competitive disadvantage because of a reluctance to embrace a computing model that could have significant advantages in their business situation.
Cloud computing is moving out of experimental and niche deployments to play a significant role in the everyday run-of-business IT infrastructure of a growing number of mainstream businesses.
From another perspective, advances in cloud applications have led to a growing number of businesses that are eager to use cloud capabilities as part of their security infrastructure, protecting both data center and mobile platforms from their remote point of view.
This book takes the position that cloud security is an extension of recognized, established security principles into cloud-based deployments. Exploring how those principles can be put into practice in protecting the cloud, protecting the traditional infrastructure from the cloud, or a hybrid of the two is what we intend to do in the remainder of this book.
In times of rapid change, both of the organization and its customers/ partners/suppliers, the ability to rapidly change the scale and capability of the IT infrastructure is critical to success. Cloud computing is, in many ways, perfect for the times in which business now finds itself.
Flexibility is inherent in the cloud model of computing. Computing resources, whether processor cycles or storage capacity, are treated as nearly infinitely flexible commodities, deployed or released as demand requires. This is perfect for matching IT services to the needs of the business and is unlikely to be supplanted as a model until something even more flexible replaces it.
Unfortunately, cloud computing is evolving so rapidly that regulations and security technology have not necessarily been able to keep pace. This means that IT professionals are frequently left to force fit pre-existing models and technologies onto new infrastructures and architectures for which they may be very poor fits, indeed. This book will look at the way those “square peg/round hole” matings are being implemented and suggest ways in which the pegs, the holes, or both may be adjusted for a more perfect fit.
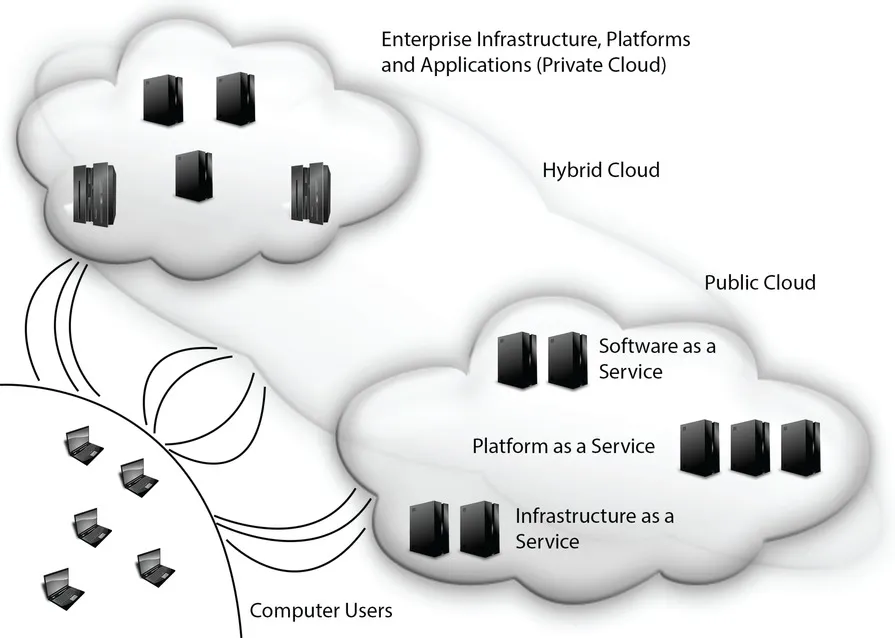
One of the important reasons for this book is that the area covered by the word “cloud” has increased significantly in the last five years. Where cloud computing once meant straightforward services obtained under contract from a public cloud provider, there are now clouds that incorporate a wide variety of services and applications—services that may be hosted on a public cloud infrastructure, on a company’s own servers, or on a combination of both types of servers.
Public cloud services are still what most people mean when they speak of the cloud, and they remain the focal point of security efforts. Quite a bit of this focus comes from the simple fact that vital enterprise data is stored or processed on systems owned by another company—systems that are accessed via the Internet. Knowing what is possible in protecting cloud-stored data is critical, but by itself, it misses a major facet of cloud security. A cloud architecture allows for a view from outside the protected data and processing infrastructure. This protection from “the high ground” is, in many ways, consistent with traditional military strategy. Although the analogy to physical defense can be stretched only so far without breaking, there are elements that provide a useful illustration of critical points, as you’ll see a bit later in the book.