
- 300 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
Among the features that make Noiseless Steganography: The Key to Covert Communications a first of its kind: The first to comprehensively cover Linguistic SteganographyThe first to comprehensively cover Graph SteganographyThe first to comprehensively cover Game SteganographyAlthough the goal of steganography is to prevent adversaries from suspe
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Noiseless Steganography by Abdelrahman Desoky in PDF and/or ePUB format, as well as other popular books in Business & Management. We have over one million books available in our catalogue for you to explore.
Information
1
INTRODUCTION
In this chapter, Section 1.1 briefly covers some of the fundamental concepts related to steganography, summarizes the current state of the research, and highlights the technical concerns. Section 1.2 introduces the novel Noiseless Steganography (Nostega) Paradigm. Section 1.3 summarizes the contribution. Finally, Section 1.4 details the organization of the book.
1.1 Steganography: Definition, Current State, and Concerns
Steganography is the scientific art of concealing the presence of covert communications. The origin of steganography is traced back to ancient civilizations [1,2]. The ancient Egyptians communicated covertly using the hieroglyphic language, a series of symbols representing a message. The message simply looks as if it is a drawing, although it may contain a hidden message. Hieroglyphs contained hidden information that only a legitimate person who knew what to look for could detect. After the Egyptians, the Greeks used “hidden writing,” which is the derivative of steganography [1,3].
In general, steganography approaches hide a message in a cover (e.g., text, image, audio file, etc.) in such a way that is assumed to look innocent and therefore not raise suspicion. Fundamentally, the steganographic goal is not to hinder an adversary from decoding a hidden message, but to prevent an adversary from suspecting the existence of covert communications [3]. Thus, when using any steganographic technique if suspicion is raised, the goal of steganography is defeated regardless of whether or not a plain text is revealed [4,5]. Contemporary schemes are generally categorized into text, image, or audio based on the steganographic cover type.
Textual steganography can be classified as textual format manipulation (TFM) and textual fabrication (TF) [3]. In TFM, comparing the original text with the modified text will reveal the hidden message [4,25]. On the other hand, textual fabrication techniques hide a message either by generating an entire text cover, by employing methods such as null cipher [6] and mimic functions [7,8], or manipulating an existing text using such methods as NICETEXT and SCRAMBLE [9–12], translation-based techniques [13–15]. However, the text cover that is generated by these approaches often has numerous linguistic flaws that can easily raise suspicion. Such flaws in text steganography are referred to hereafter as noise. It is argued that such noise even makes it feasible to reveal the hidden message [3,13,25,107].
On the other hand, image steganography is based on manipulating digital images to conceal a message. Such manipulation often renders the message as noise. In general, image steganography suffers from several issues, such as the potential of distortion, the significant size limitation of the messages that can be embedded, and the increased vulnerability of detection through contemporary image processing techniques [5]. Audio covers have also been pursued. Examples of audio steganography techniques include LSB [16,17], spread spectrum coding [18,19], phase coding [18,20], and echo hiding [21]. In general, these techniques are too complex, and like their image-based counterparts, are still subject to distortion and detection [5].
The inability of contemporary steganography approaches to achieve the steganographic goal can be traced back to the fact that they either introduce noise to the cover or exploit noise in hiding the data. The shortcomings of these schemes motivate the presented research in this book.
1.2 Noiseless Steganography (Nostega) Paradigm
As indicated above, contemporary steganography schemes either introduce noise to the original document used as a cover, or exploit noise in the data-hiding process. The book introduces a novel paradigm for designing steganography schemes, namely, Nostega [32,35]. Nostega opts to make the presence of the hidden data natural in the cover so that neither linguistic flaws nor peculiarities are introduced as a side effect. In addition, Nostega strives to legitimize the interaction among the communicating parties so that an adversary would not suspect the association between a sender and a receiver. To illustrate the basic concept behind Nostega, consider the following scenario.
Bob and Alice are on a spy mission. Bob and Alice must appear like any other ordinary people. To emphasize, in general, “ordinary people” have professions and personal interests. Before they go on a mission that requires them to reside in two different countries, Bob and Alice plot a strategic plan and set the rules for communicating covertly using their professions and interests as steganographic umbrellas. Bob is a professor and Alice is a student. They basically agree on concealing messages in educational documents by naturally manipulating questions and answers that legitimately occur in lecture notes, exam samples, homework, and examples, to embed data in such a way that the text cover (edu-cover) looks unsuspicious. They make sure that every time a text cover is generated it has different content and meaning, while it remains legitimate to avoid suspicion of using a steganographic tool. To make this work, Professor Bob has the right to post the text cover (e.g., lecture notes, sample exams, homework, and examples) for his students. On the other hand, Alice is one of Bob’s online students, which legitimizes her communications with Bob. When Bob wants to send a covert message to Alice, Bob either posts text cover online for authorized students to access, or sends it via email to the intended students. Covert messages concealed and transmitted in this manner will not look suspicious because the relationship between Bob and Alice is legitimate. Furthermore, Alice is not the sole recipient of Bob’s messages; other non-spy students also receive their educational documents, further warding off suspicion.
When Alice decides to send Bob a message, she does it in the same manner as Bob does, except that she uses her role as a student to do so. She posts educational documents, such as her homework solutions, if it is legitimate to do so, as well as other related documents that Bob or any student in class can access, or else she sends them via email to the professor. These educational documents conceal data. However, only Bob and Alice are able to unravel the hidden message because they know the rules of the game. Both Bob’s and Alice’s communications look legitimate and nothing is suspicious because the relationship between the communicating parties is justified. Alice and Bob are using real data from their academic field to make their covert communications legitimate. Note that even after a class is over, such relationships can still play a role, for instance, a student becoming interested in a particular topic and pursuing it as a profession (e.g., Ph.D. students). On the other hand, if Bob and Alice communicate using cipher text, suspicion can easily be raised and thus the steganographic goal will be defeated.
The above scenario shows how Nostega methodology can be effective in achieving the steganographic goal. In summary, Nostega conceals data in a steganographic cover that looks legitimate and is like any other ordinary material. The cover is then transmitted through an established covert channel such as the legitimate and innocent relationship between Bob and Alice in the above scenario.
1.2.1 The Architecture of Nostega
Nostega achieves legitimacy by basing the camouflage of both a message and its transmittal on a particular field such as education, economics, graphs, or games, as stated earlier, in the above example of Bob and Alice, using a particular profession or relationship gives legitimacy for camouflaging both a message and its transmittal. The core idea of the Nostega paradigm is basically camouflaging messages by embedding them in a form of noiseless data by employing either altered authenticated data or legitimate untraceable data, as shown in Section 1.3. The following is an overview of the Nostega architecture, which consists of five modules as shown in Figure 1.1.
1. Steganographic field determination (Module 1) determines the fields such as education, economics, graphs, or games for achieving the steganographic goal. A major selection criterion is the way the steganographic field facilitates the process of generating a noiseless cover in which the data is naturally embedded, so that the cover looks innocent raising no suspicion and, thus, the hidden message is undetectable. Note that the process of Module 1 is only involved at the stage of constructing a Nostega-based system.
2. Steganographic parameters determination (Module 2) encodes a message in an appropriate form for the camouflaging process (Module 3). The form and the component of the output of Module 1 may essentially effect how a message can be encoded. Therefore, studying and analyzing the output of Module 1 is necessary for determining the parameters that can be used by next module (Message Encoder). In other words, this module is responsible for determining which parameters can be employed in order to implement a steganographic code that can encode messages in an effective way. For instance, if the steganographic field is a graph, then the steganographic parameters may be numerical values to plot the graph cover [33]. On the other hand, if the steganographic field is chess games, then the steganographic parameters may be chess moves [30].
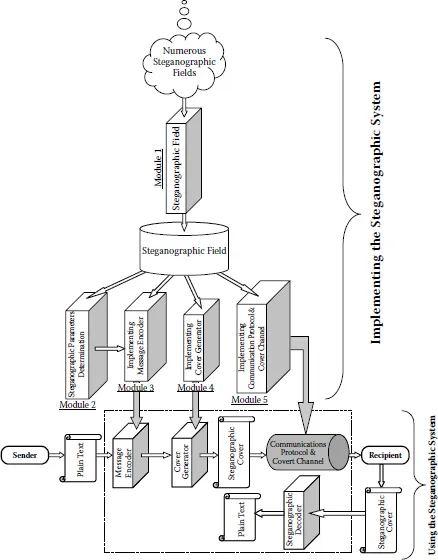
Figure 1.1 This figure Illustrates an overview of Nostega methodology. It shows the interaction of various modules required to build a Nostega system and the configurations between communication parties.
3. Implementing message encoder (Module 3) implements a message encoder that is capable of accommodating the requirements of the Nostega paradigm as stated earlier.
4. Implementing cover generator (Module 4) constructs a cover generator or uses a contemporary tool that is capable of achieving the steganographic goal. For instance, if the cover is a graph such as a chart, then employing a tool used by a wide variety of programs such as Microsoft Excel may be a good option in order to generate a steganographic cover that looks like an ordinary graph. On the other hand, if the cover is chess, then chess software such as Chessmaster [154] may legitimize the steganographic cover.
5. Implementing communications protocol and covert channel (Module 5) configures the basic protocol of how a sender and a recipient communicate covertly. It includes the covert channel for delivering a Nostega-based cover between the communicating parties, along with the decoder scheme to unravel a hidden message. A covert channel can be based on a justifiable reason as in the scenario of Bob and Alice discussed above.
1.2.2 Advantages of Nostega
Nostega promotes both the camouflaging of a message and its transmittal. Nostega neither hides data in a noise (errors), nor produces noise rendering the generated cover noiseless. Instead, it conceals messages in a form of noiseless dada in the generated cover using either unaltered authenticated data or untraceable data, thus avoiding wide varieties of attacks. If text is used as a steganographic carrier, the concealment process of Nostega has no effect on the linguistics of the generated cover, rendering such text cover legitimate. Unlike other approaches such as translation-based methods, Nostega can be applied to all languages. For steganographic carriers, Nostega uses materials such as graphs, text, or games, all of which have plenty of room for concealing data. The implemented metrologies based on the Nostega paradigm are keyless schemes. Yet, Nostega is a public paradigm, which implies that it is resilient even when an adversary is very familiar with this new paradigm. It is observed that a steganographic system based on Nostega is capable of fooling both machine and human examinations.
1.3 Summary of the Contributions
The key contribution of this book is the introduction of the novel Noiseless Steganography (Nostega) Paradigm [32,35]. In addition, a number of Nostega-based steganography methodologies are developed. The following highlights the basics of the individual methodologies:
• Graph Steganography Methodology (Graphstega) is the science and art of avoiding the arousal of suspicion in covert communications by concealing a message in a novel cover type, namely graph cover [33]. Following the Nostega paradigm, Graphstega does not embed a message as a noise in a cover. Instead, a message is camouflaged as plotted data. Graph covers can be applied to a wide variety of domains rendering it a suitable Nostega-based carrier. The popular usage of graphs in business, education, and news, and the availability of a tremendous number of graphs in electronic and non-electronic format make the investigation and detection of a hidden message extremely difficult.
• Chess Steganography Methodology (Chestega) exploits popular games such as chess, checkers, crosswords, dominoes, etc., to embed data in steganographic game cover [30]. Chestega conceals messages in the related data of games including instructional material, game analysis, and news articles, by employing intrinsically authenticated or untraceable innocent data in the generated cover, which renders it noiseless.
• Education-Centric Steganography Methodology (Edustega) camouflages data in educational documents primarily by manipulating questions and answers (e.g., multiple-choice, true-or-false, fill-in-the-blank, matching) of exams, examples, puzzles, and competitions in order to embed data without generating any suspicious pattern [22]. For instance, multiple-choice questions can conceal data in the correct answers by placing the correct answers where they represent a steganographic code of a message, e.g., choices from “A” to “D” can represent binary numbers from “00” to “11”. In addition, wrong answers (wrong choices) can also conceal data. While these choices must be wrong, there is no real constraint on embedding the data.
• Summarization-Based Steganography Methodology (Sumstega) takes advantage of recent advances in automatic summarization techniques to generate a text cover [23,34]. Sumstega does not exploit noise (errors) to embed a message nor produce a detectable noise. Instead, it pursues the variations among the outputs of auto-summarization techniques to conceal data. Basically, Sumstega manipulates the parameters of automatic summarization tools, e.g., frequency weights of words in the sentence selection, and employs other contemporary techniques such as paraphrasing and reordering to generate summary cover that looks legitimate. The popular use of text summaries in business, science, and education renders summary an attractive steganographic carrier and averts an adversary’s suspicion.
• Mature Linguistic Steganography Methodology (Matlist) employs natural language generation (NLG) and template techniques along with random series (RS) values (e.g., binary, decimal, hexadecimal, octal, alphabetic, and alphanumeric) of a Domain-Specific Subject (DSS) to generate noiseless text cover [27,107]. This type of DSS (e.g., financial, medical, mathematical, scientific, and economical) has plenty of room to conceal data. It allows communicating parties to establish a covert channel, such as a relationship based on the profession of the communication parties, to transmit a text cover. Matlist embeds data in a form of RS values, functions of RS, related semantics of RS, or a combination of these.
• Normal Linguistic Steganography Methodology (NORMALS) takes advantage of recent advances in automatic Natural Language Generation (NLG) techniques to generate noiseless (flawless) and legitimate text cover by manipulating the input parameters of an NLG system in order to camouflage data in the generated text [26]. As a result, NORMALS is capable of fooling both human and machine examinations. Unlike Matlist, NORMALS is capable of handling non-random series domains.
• Email-Headers-Based Steganography Methodology (Headstega) takes advantage of the frequent exchange of emails by a wide variety of people who gener...
Table of contents
- Cover
- Title Page
- Copyright
- Dedication
- Contents
- Foreword
- Acknowledgments
- About the Author
- Chapter 1: Introduction
- Chapter 2: Related Work
- Chapter 3: Graph Steganography Methodology
- Chapter 4: Chess Steganography Methodology
- Chapter 5: Education-Centric Steganography Methodology
- Chapter 6: Summarization-Based Steganography Methodology
- Chapter 7: Mature Linguistic Steganography Methodology
- Chapter 8: Normal Linguistic Steganography Methodology
- Chapter 9: Steganography Methodology
- Chapter 10: Automatic Joke Generation-Based Steganography Methodology
- Chapter 11: Steganography Methodology
- Chapter 12: Steganography Methodology
- Chapter 13: Steganalysis Validation
- Chapter 14: Conclusion and Future Work
- Bibliography
- Index