
- 224 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Managing the Risks of IT Outsourcing
About this book
This book shows IT managers how to identify, mitigate and manage risks in an IT outsourcing exercise. The book explores current trends and highlights key issues and changes that are taking place within outsourcing. Attention is given to identifying the drivers and related risks of outsourcing by examining recently published and existing concepts of IT outsourcing.
Founded on academic theory and empirical and quantitative information, this book:
* Incorporates the complete risk identification and mitigation life cycle
* Highlights the concept of core competency
* Looks at motivating factors and working relationships of the buyer and supplier
* Provides background to understand the risks as a result of 'human factors' as defined by the agency theory
* Reviews the areas of risk that influence the decision to outsource the IT function
* Examines the forces that determine the equilibrium in the risk profiles for the buyer and supplier
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Managing the Risks of IT Outsourcing by Ian Tho in PDF and/or ePUB format, as well as other popular books in Business & Business General. We have over one million books available in our catalogue for you to explore.
Information
Section II
Measuring and understanding IT outsourcing risks
3
Measuring risks in IT outsourcing
Without measureless and perpetual uncertainty the drama of human life would be destroyed.
Winston Churchill (1874–1965), British prime minister
Risks in IT outsourcing (ITO) are often the effects of a combination of activities and events. These events can arise both at different times and in different geographical locations. For example, an event in the Head Office in Singapore last month could have very significant effects on another event in Sydney, Australia, today and affect another activity in San Francisco the following week. Various methods and tools are used to help measure and quantify these activities and events. The risk dimension signature (RDS) instrument proposed in this chapter allows measurements to be made from the various risk perspectives, and then graphically illustrates the risk exposure values (or measured quantities) at different points in time. The risk profiles that are depicted in the RDS then become an essential part of overall risk management methodology that allows the manager to understand risks more completely and make informed decisions. RDS transforms risk management from an academic or mathematical exercise into an essential and practical tool.
Risks involve events that are characterized by probability and uncertainty. They also stem from possibilities and indeterminate paths as a result of random events. We know that ITO is characterized by:
• multiple variations in outsourcing models (Chapter 1); and
• the two very special roles that the IT function plays in an organization (Chapter 2).
This, combined with the complexities of both the buyer and supplier organizations in a synergistic, long-term relationship, creates an environment that is full of events and ‘risk fertile’, or full of risks.
Measurement activity to capture these risks is more complex than ever before, partly as a result of the intricacies involved with available options and volumes of information flows that power today’s fast-moving organizational processes. The probability of an event happening, whether with good or bad consequences, is never predictable to any degree of certainty. In fact, uncertainty in the economy, in technology, in business and in politics has made forecasting based on probabilities quite futile and, sometimes, even counter-productive.
In order to understand risks, however, detailed observation and measurement is mandatory. So the first step in the process is to be able to take measurements and to illustrate the results in a way that is meaningful to the ITO manager or practitioner. If the risk characteristics that are expressed in the specific ITO assignment can be measured, activities to mitigate the risks can be put into place for selected risks. A simplified step methodology involving three basic steps, Measure, Understand and Mitigate (MUM), as illustrated in Figure 3.1, is used to show the three fundamental phases that are used to address risks before a more comprehensive risk management method is used.
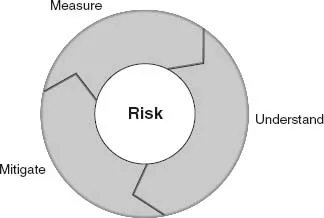
Figure 3.1 Managing risks in an IT outsourcing environment
Obviously a complete risk management methodology is comprehensive but the MUM method addresses the need to quickly depict and address urgent risks and allows plans to be effective as critical risks will need to be addressed urgently. Therefore more detailed risk management methods should be used in conjunction with the three phases proposed. This approach is designed to be short, and to be as practicable as possible for easy use. Given these assumptions, it should also be used in conjunction with organizational communications that include policy making, suitable controls and the promotion of risk awareness programmes (see also samples of widely accepted risk management models in Figures 3.5 and Figure 3.6). These items or activities form part of the overall risk management plan (see Chapter 6).
3.1 Risk definition
For simplicity, many scholars and researchers agree to define risk in an ITO scenario simply as the possibility of loss or injury. Risks begin as a direct consequence of negative outcomes. Risks are also formed as an extension of factors leading to negative outcomes. Risks refer either directly to:
• negative outcomes; or
• factors that lead to the negative outcomes.
Negative outcomes include shortfalls in systems performance. For example, in the case of a software development project, poor systems performance could take the form of disruption of service to a customer that depends on IT to support a particular business process function. In an ITO exercise, hidden costs (described in Chapter 2) and loss in innovative capacity would constitute examples of poor systems performance. Factors that lead to these negative outcomes include, for example, a continuing stream of requirement changes or personnel shortfalls in a systems development context. In an ITO project, lack of upper management commitment to the exercise or inexperienced staff and business uncertainty are clearly factors that lead to negative outcomes. The existence of vague links between the outcomes and contributory factors does not make the understanding of risks any easier or measurement more straightforward.
Risks can be quantified as expected potential loss. To do this, the expected potential loss from outsourcing is reckoned as the product of two variables, the magnitude of the exposure and the probability of loss.
3.2 Investigating risk
Risks are classified as either speculative or pure risks. Speculative risks (e.g. gambling) offer both the potential for gain and the potential for loss, for example in investment in stocks. Pure risks, the kind that occur in an ITO exercise, do not necessarily result in losses, but they never result in gains and are, for the most part, unwanted.
To reduce the loss or mitigate risks, efforts are focused on reducing the probability of the undesirable event itself through, for example, the use of penalties compensating for delays in system delivery. The probability of occurrence of an undesirable outcome is estimated on the basis of historical data. Probabilities are often, however, difficult to determine merely on the basis of past performance. In the case study example in Chapter 8, it is obvious that the probabilities estimated by the ITO team represent quantitative data based on collective experience.
Intrusive factors (exogenous and endogenous risks)
Further, a distinction that could be made in risk types is the classification of endogenous and exogenous risk. A risk is classified exogenous when an undesirable event occurs beyond any form of control and is not affected directly by any actions. Examples are earthquakes or typhoons. Endogenous risks are those that are dependent directly on people actions. An automobile accident is an example of risk where a large portion of the risk is endogenous. The probability of a virus attack is significantly influenced by the user’s behaviour and software use (endogenous). The PC user controls part of this risk by deciding to expose corporate networks through unwanted links on the network. To mitigate this risk, users are informed of the areas they can control and are advised on more restrictive practices to adopt when surfing the Internet and performing downloads.
In a business environment, the dynamics of risk exposure can be, and are, influenced by many variables. The magnitude of these variables, in singular or group form, collectively determines their relevance. For example, the effects of risk on the finances of an organization can be influenced by its shareholder structure, the business environment (which determines the amount of investment), the technology environment (which determines the capability of performing selected functions) and the competitive environment (which determines its products, delivery and organizational structure). These factors ‘intrude’ into the outsourcing environment. It has been shown that these ‘intrusive factors’ contribute to the risk profile of the outsourced operation.
Risk dimensions are affected at different levels by external (exogenous) influences of ‘intrusive factors’ discussed earlier as well as internal (endogenous) influences. An example of the influences impinging on risk factors is illustrated in Figure 3.2. Environmental and business risk in the case study (see Chapter 8) for example, derives from external influences, discussed in detail here. The organization’s strategic, legal and informational risk profiles are influenced most significantly by a mix of both internal and external influences.
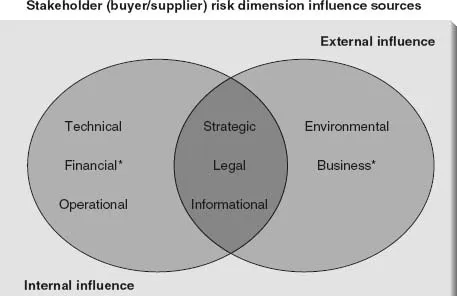
Figure 3.2 Example of mapping internal (endogenous) and external (exogenous) influences with risk dimensions (Tho, 2004)
Operational and relationship risks
There are two main angles from which risk that is inherent in an ITO arrangement is viewed. The first is the operational risk that involves undesirable consequences deriving from the operations of IT in the organization. The second form of risk stems from the relationship between the buyer and supplier in the form of opportunistic behaviour by the supplier who takes advantage of a long-term and ambiguous contract (see also Agency Theory in Chapter 4). Both these risk types are illustrated in Figure 3.3. A significant portion of the operational risk is passed on to the supplier as the IT function is outsourced while the relationship risk remains with the buyer. Unlike operations risk, the relationship risk is ‘bi-directional’. In this instance, the risk exposure relating to the relationship can be passed back and forth depending on the situation and the ‘bargaining power’ of both the contracting parties at that time. The relationship risk shifts from buyer to supplier and vice versa.
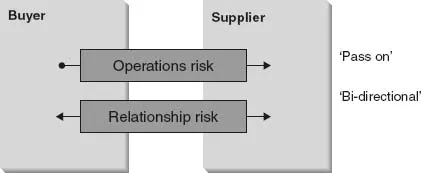
Figure 3.3 Operations and relationship risk (Tho, 2003)
Further relationship risk exposure from the outsourcing deal includes some common areas such as:
• misaligned incentives between supplier and buyer;
• insufficient investments from the participants;
• market failures from private information not shared;
• ineffective bidding mechanisms;
• inappropriate use of confidential information;
• supplier hold-up, expropriation and loss of bargaining power; and
• supplier’s private information about its capabilities.
This list above contains many of the salient features but is by no means exhaustive. In order to examine the risks inherent in an organization that is considering outsourcing its IT function, the elements that contribute to the risk in the ITO environment need to be explored. (See also Agency Theory and the Winner’s Curse phenomenon in Chapter 4.)
The scope of outsourcing includes strategic IT functions together with value activities that differentiate the organization from its suppliers. As suppliers provide competence in new technologies and access to better IT professionals, these elements contribute strategically to the buyer’s organizational value chain. The expanded role of outsourcing relationships includes relatively better services and financial performance, and new lines of business. Elements of the e-commerce value chain, including strategy, systems development and integration, payment processing, market design, advertising and customer management, as well as development of the physical network and web-hosting, are outsourced.
In the ITO scenario, risk carries functions of multiple variables, mathematically expressed as:
Risk = fn(governance, (un)certainty, competitive environment, organizational interconnectedness)
In a ‘cause and effect’ situation, risks also play a role in the effects of activities engendered by the outsourcing of the IT function. Risks in this instance are concerned with the effect of governance, uncertainty, competitive environment and organizational interconnectedness (Clemons, 2000). The point raised here is that risks in the ITO exercise appear to have a direct relationship with a set of causes. It is argued that, while some arguments for ITO are intuitively appealing at an analytical and general level, they remain simplistic in practice because they do not account for the complexities that permeate the management of information resources and risks (Earl, 1996). Some different models are examined in the following sections.
3.3 IT outsourcing risks (causes and effects)
A primary driver or determinant of risk originates from the lack of information (information asymmetry) in the precontract phase, followed by an inherent inability to accurat...
Table of contents
- Cover
- Halftitle
- Title
- Copyright
- Contents
- Dedication
- About the author
- Preface
- Section I: Language of IT Outsourcing (ITO)
- Section II: Measuring and understanding IT outsourcing risks
- Section III: Mitigating (& managing) risks in IT outsourcing
- References
- Index