
eBook - ePub
Foundations of Information Security Based on ISO27001 and ISO27002 - 3rd revised edition
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Foundations of Information Security Based on ISO27001 and ISO27002 - 3rd revised edition
About this book
This book is intended for everyone in an organization who wishes to have a basic understanding of information security. Knowledge about information security is important to all employees. It makes no difference if you work in a profit- or non-profit organization because the risks that organizations face are similar for all organizations.
It clearly explains the approaches that most organizations can consider and implement which helps turn Information Security management into an approachable, effective and well-understood tool. It covers:
• The quality requirements an organization may have for information;
• The risks associated with these quality requirements;
• The countermeasures that are necessary to mitigate these risks;
• Ensuring business continuity in the event of a disaster;
• When and whether to report incidents outside the organization.
The information security concepts in this revised edition are based on the ISO/IEC27001:2013 and ISO/IEC27002:2013 standards. But the text also refers to the other relevant international standards for information security.
The text is structured as follows:
• Fundamental Principles of Security and Information security and Risk management.
• Architecture, processes and information, needed for basic understanding of what information security is about.
• Business Assets are discussed.
• Measures that can be taken to protect information assets. (Physical measures, technical measures and finally the organizational measures.)
The primary objective of this book is to achieve awareness by students who want to apply for a basic information security examination. It is a source of information for the lecturer who wants to question information security students about their knowledge. Each chapter ends with a case study. In order to help with the understanding and coherence of each subject, these case studies include questions relating to the areas covered in the relevant chapters. Examples of recent events that illustrate the vulnerability of information are also included.
This book is primarily developed as a study book for anyone who wants to pass the ISFS (Information Security Foundation) exam of EXIN. In an appendix an ISFS model exam is given, with feedback to all multiple choice options, so that it can be used as a training for the 'real' ISFS exam.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Foundations of Information Security Based on ISO27001 and ISO27002 - 3rd revised edition by Jule Hintzbergen,Kees Hintzbergen,Hans Baars,André Smulders in PDF and/or ePUB format, as well as other popular books in Education & Architecture General. We have over one million books available in our catalogue for you to explore.
Information
Topic
EducationSubtopic
Architecture General
This book is intended for everyone in an organization who wishes to have a basic understanding of information security. Knowledge about information security is important to all employees. It makes no difference if you work in a profit- or non-profit organization because the risks that organizations face are similar for all.
Employees need to know why they have to adhere to security rules on a day-to-day basis. Line managers need to have this understanding as they are responsible for the security of information in their department. This basic knowledge is also important for all business people, including those self-employed without employees, as they are responsible for protecting their own information. A certain degree of knowledge is also necessary at home. And of course, this knowledge forms a good basis for those who may be considering a career as an information security specialist, whether as an IT professional or a process manager.
Everyone is involved in information security, often via security countermeasures. These countermeasures are sometimes enforced by regulatory rules and sometimes they are implemented by means of internal rules. Consider, for example, the use of a password on a computer. We often view such measures as a nuisance as these can take up our time and we do not always understand what the measures are protecting us against.
Information security is the trick to find the right balance between a number of aspects:
■ The quality requirements an organization may have for its information;
■ The risks associated with these quality requirements;
■ The countermeasures that are necessary to mitigate these risks;
■ Ensuring business continuity in the event of a disaster;
■ When and whether to report incidents outside the organization.
■ 1.1 WHAT IS QUALITY?
First you have to decide what you think quality is. At its simplest level, quality answers two questions: ‘What is wanted?’ and ‘How do we do it?’ Accordingly, quality’s stomping ground has always been the area of processes. From ISO 9000, to the heady heights of Total Quality Management (TQM), quality professionals specify, measure, improve and re-engineer processes to ensure that people get what they want. So where are we now?
There are as many definitions of quality as there are quality consultants, but commonly accepted variations include:
■ ‘Conformance to requirements’ - P.B. (Phil) Crosby (1926-2001);
■ ‘Fitness for use’ - Joseph Juran (1904 - 2008);
■ ‘The totality of characteristics of an entity that bear on its ability to satisfy stated and implied need’ - ISO 9001-2008;
■ Quality models for business, including the Deming Prize, the EFQM excellence model and the Baldrige award.
The primary objective of this book is to provide awareness for students who want to apply for a basic security examination. This book is based on the international standard ISO 27002:2013. This book is also a source of information for the lecturer who wants to question information security students about their knowledge. Many of the chapters include a case study. In order to help with the understanding and coherence of each subject, these case studies include questions relating to the areas covered in the relevant chapters. Examples of recent events that illustrate the vulnerability of information are also included.
The case study starts at a very basic level and grows during the chapters of the book. The starting point is a small bookstore with few employees and few risks. During the chapters this business grows and grows and, at the end, it is a large firm with 120 bookstores and a large web shop. The business risks faced by this bookshop run like a thread through this book.
This book is intended to explain the differences between risks and vulnerabilities and to identify how countermeasures can help to mitigate most risks. Due to its general character, this book is also suitable for awareness training or as a reference book in an awareness campaign. This book is primarily aimed at profit and non-profit organizations, but the subjects covered are also applicable to the daily home environment as well to companies that do not have dedicated information security personnel. In those situations the various information security activities would be carried out by a single person. After reading the book you will have a general understanding of the subjects that encompass information security. You will also know why these subjects are important and will gain an appreciation of the most common concepts of information security.

■ 2.1 INTRODUCTION
To understand the theory in this book, it will be helpful to translate it to a practical situation. In most situations the reader gets a better understanding of the theory when it is illustrated by a practical case study.
In this case study, used throughout all chapters of this book, questions are included that relate to lessons learned in each chapter.

Figure 2.1 Springbooks’ London headquarters
This chapter gives an explanatory introduction to the case study. The establishment of the bookstore, the history and the years of growing into an international company are all described.
Springbooks was founded in 1901. During its expansion into an international organization operating within Europe the company has to change and to adjust to its environment. A major part of this is the huge change over the last 50 years in supplying information. As one might imagine there is a big difference in process control between the time Springbooks was founded in 1901, with the emergence of Information and Communication Techniques (ICT) during the 1960s and 1970s, through to the ever increasing dependence on ICT nowadays. ICT has become one of the most important tools for Springbooks.
■ 2.2 SPRINGBOOKS
Springbooks Ltd. (SB) is a European operating bookstore. SB is an organization with 120 bookshops, most of which are run on a franchise basis. In total, 50 of the shops are owned by SB itself.
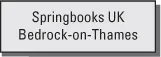
Figure 2.2 Organizational chart Springbooks 1901-1931
SB was founded in 1901 when Henry Spring opened a small shop in Bedrock-on-Thames, UK.
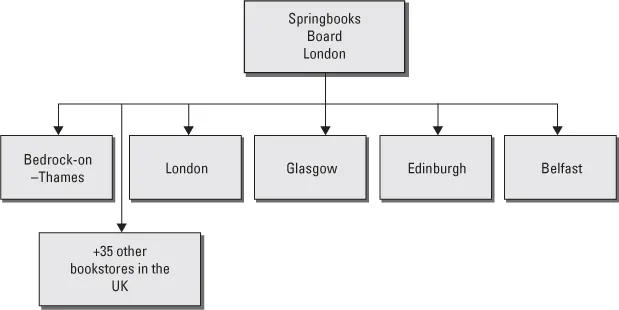
Figure 2.3 Organization of Springbooks 1938
Over time 36 shops were established in all major cities in the UK. Immediately after the end of World War 2 SB established bookshops in Amsterdam, Copenhagen, Stockholm, Bonn, Berlin and Paris.
Nowadays SB has shops in all major cities in the EU. The Board of Directors is based at offices in London. European headquarters are in Amsterdam and every country has a central office. All bookstores are accountable to their national office. The national office is accountable to the European Headquarters in Amsterdam. The European headquarters are ultimately accountable to the Board of Directors in London.
In 2000 plans were made to expand the international business into the USA, Canada, Australia and New Zealand. However, because of the banking crisis, these plans were not carried out, until spring 2015 when the ideas have been published to expand to Australia and New Zealand.
The banking crisis has had a serious effect upon the worth of SB shares. The fact is that one of the first things people economize on are books, newspapers and magazines. All these are core businesses of SB. This resulted in a temporary halt on the plans to expand the overseas market. Investment plans in new stores are frozen and a search for new markets has resulted in new plans.
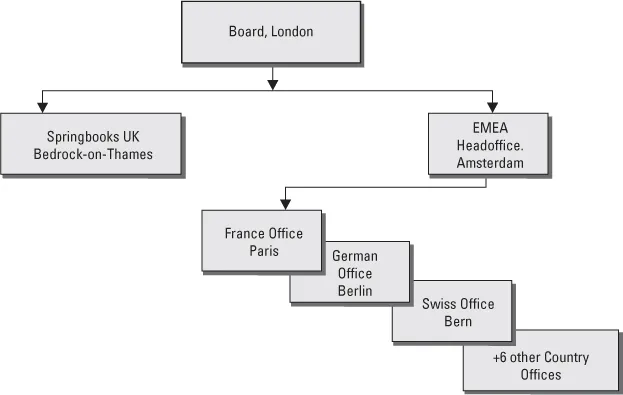
Figure 2.4 Organization of Springbooks 1946-2010
The board of directors has adopted an old fashioned approach to business for a long time. The Internet was not their way of doing business.
An independent consultancy group has advised that SB should launch stores in Australia and New Zealand to expand in combin...
Table of contents
- Cover
- Title
- Copyright
- Preface
- Preface by the Authors
- Acknowledgements for second edition
- Contents
- 1 Introduction
- 2 Case study: Springbooks – an international bookstore
- 3 Definitions and security concepts
- 4 Context of the organization
- 5 Information security policies
- 6 Organization of information security
- 7 Human resource security
- 8 Asset management
- 9 Access control
- 10 Cryptography
- 11 Physical and environmental security
- 12 Operations security
- 13 Communications security
- 14 System acquisition, development and maintenance
- 15 Supplier relationships
- 16 Information security incident management
- 17 Information security aspects of business continuity management
- 18 Compliance
- Appendix A Glossary
- Appendix B Overview of family of ISO 27000 standards
- Appendix C.1 Example exam
- Appendix C.2 Answer Key
- Appendix C.3 Evaluation
- Appendix D About the authors
- Index