
- 50 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Meeting People via WiFi and Bluetooth
About this book
Meeting People via WiFi and Bluetooth will contain an overview of how to track people using Wireless 802.11 Radio Frequencies (Wi-Fi) and Bluetooth 802.15 Radio Frequencies. The content contained here came from research and materials originally presented at Defcon Wireless CTF Village in August 2015 entitled "Meeting People Via Wi-Fi".
The book will go over the hardware and software needed in order to do this tracking, how to use these particular tools in order to do attribution, and tips for protecting yourself from being attributed via those signals.
- Offers an overview of how to track people using WiFi and Bluetooth technologies
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Overview
Scanning for Device Association
Abstract
Every day people use all kinds of devices that emit radio frequencies (RFs) that provide identifying information about them. The devices used every day to make common data communications allow us to connect to the Internet or internal networks in our home, work, or car. Many of these help us be more productive, safer, and stay in touch with those we know and love. However, with every connection we make, there exists the opportunity for something called RF signal leakage. This chapter briefly discusses how data can be intercepted using RFs.
Keywords
Radio frequencies; RF signal leakage; smartphone; Internet; data
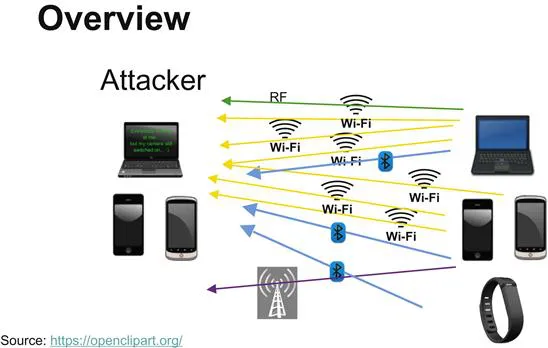
Every day people use all kinds of devices that emit radio frequencies (RFs) that provide identifying information about them. Over the years, governments, private investigators, and radio enthusiasts have designed and created techniques to triangulate and identify individuals for the purpose of catching illegals, finding missing persons, shutting down radio interference, as well as intercepting communications.
The devices used every day to make common data communications allow us to connect to the Internet or internal networks in our home, work, or car. Many of these help us be more productive, safer, and stay in touch with those we know and love. However, with every connection we make, there exists the opportunity for something called RF signal leakage.
RF signal leakage occurs when someone other than the intended recipient receives a RF. This may be attacker related, such as running a scanner or interceptor, or accidental like when a cordless phone or radio picks up another cordless phone using the same channel. Either way this gives someone with nefarious intentions an opportunity to profile and track their target’s daily movements and, in some cases, the possibility to intercept their communication.
RF signal leakage is not limited to audio transmissions, it can affect data and video too. If High-Definition Multimedia Interface (HDMI) cables or external keyboards used in a target’s home or business consist of unshielded cables, then RF signal leakage could present a problem. An attacker could listen to and decode to keys typed or replay and decode images transmitted via the HDMI cable. This is why many keyboards, such as the Logitech, now encrypt their communications with encryption standards such as AES (Logitech, Inc., 2015). Even with encryption though, some of the underlying technology indicators like device type and distance from the sniffer or scanner could be determined, as these factors present themselves in order to establish the connection.
Another example, the smartphone, presents the opportunity for several vectors of profiling. Some, but not all, would include cell phone signal transmitting via Global System for Mobile (GSM) or Code division multiple access (CDMA), the probing for Wi-Fi hotspots to save on data rates or Bluetooth to connect to external peripherals. All of these different RF signals can essentially be used to identify a person in a given space.
This can be accomplished through the unique identifiers that tell the network, be it cell towers, Wi-FI, or point to point (P2P) Bluetooth, which allow the device to send and receive the communications. For example, each SIM card contains a unique identifier that tells the tower who you are so the provider can know what phone number and data allowance to give your device with a given number. The same is true with Bluetooth and Wireless communications, except those two technologies normally use Media Access Control (MAC) address.
All communication devices possess a Federal Communications Commission issued device MAC address. This identifier allows devices to communicate and prevents collisions and preserves the uniqueness of a device on a network. Bluetooth also has UUID codes that it displays during point-to-point association searches that are unique per device and could assist in profiling.
There may be additional IDs and signatures that can be associated but all Wi-Fi, Bluetooth, Cell Phone Radio Frequencies, or some other similar connections, it will have a MAC address in the form of XX:XX:XX:XX:XX:XX, where the XX’s will be replaced with a given unique MAC consisting of hex characters. The format for Wi-FI and Bluetooth consists of a format of XX:XX:XX:AA:BB:BB, where the first three hexadecimals are set aside for the device manufacturer who purchased the license to create the device, and the last three hexadecimals represent the ID that the manufacturer assigned to that device. We will show later how this can be used to create a comprehensive target profile. This allows an attacker to create a profile, or database key, every time they see communication from that device as well as giving them a format to lookup device type in online databases provided by the FCC and other network companies.
It is important to note (according to a recent article www.arstechnica.com) that iPhones with iOS 8.0 and above have started to spoof MAC addresses. Based on a variety of factors, the most notable of which is a reboot of the phone forces, this protection technique has to be triggered. Further research shows a MAC address from an iPhone incrementing its address by one hex digit via Wi-Fi probes when searching for an access point.
Also, when attempting to find some device types, the manufacturer code sometimes replied as Private or Unknown which means that they are either protected from disclosure by the FCC (in the interest of National Security), or may be protected under development laws for the interest of protecting patents or new technologies, as explained by John Abraham, the creator of the Android Bluetooth scanning tool BlueScan.
Before we continue, let’s clarify that all of this profiling can be done by means coined under the term of “War Driving,” a term first established by Peter Shipley to mean “to go out and search for open wireless LANS.” The act of war driving...
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- About the Authors
- Overview
- Chapter 1. Overview: Scanning for Device Association
- Chapter 2. Hardware and Software Needed
- Conclusion
- References
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Meeting People via WiFi and Bluetooth by Henry Dalziel,Joshua Schroeder in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.