
- 254 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
Data Breach Preparation and Response: Breaches are Certain, Impact is Not is the first book to provide 360 degree visibility and guidance on how to proactively prepare for and manage a data breach and limit impact. Data breaches are inevitable incidents that can disrupt business operations and carry severe reputational and financial impact, making them one of the largest risks facing organizations today. The effects of a breach can be felt across multiple departments within an organization, who will each play a role in effectively managing the breach. Kevvie Fowler has assembled a team of leading forensics, security, privacy, legal, public relations and cyber insurance experts to create the definitive breach management reference for the whole organization.
- Discusses the cyber criminals behind data breaches and the underground dark web forums they use to trade and sell stolen data
- Features never-before published techniques to qualify and discount a suspected breach or to verify and precisely scope a confirmed breach
- Helps identify your sensitive data, and the commonly overlooked data sets that, if stolen, can result in a material breach
- Defines breach response plan requirements and describes how to develop a plan tailored for effectiveness within your organization
- Explains strategies for proactively self-detecting a breach and simplifying a response
- Covers critical first-responder steps and breach management practices, including containing a breach and getting the scope right, the first time
- Shows how to leverage threat intelligence to improve breach response and management effectiveness
- Offers guidance on how to manage internal and external breach communications, restore trust, and resume business operations after a breach, including the critical steps after the breach to reduce breach-related litigation and regulatory fines
- Illustrates how to define your cyber-defensible position to improve data protection and demonstrate proper due diligence practices
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
An Overview of Data Breaches
Kevvie Fowler
Abstract
This chapter sets the common understanding of what a data Breach is, individuals' responsibility, the impact experienced by the victims, and some of the historical challenges faced by organizations in responding to Breaches. Common terms will be established in this chapter that will be referenced throughout the book.
Keywords
Data Breach; Invisible web; Sensitive data; Petty criminal; Nation state sponsored criminal; Organized criminal; Organized crime; Hacktivist; Dark web; Deep web; Underground economy
Introduction
You are at home watching television when your phone rings. It's your boss, he advises you that your company has received complaints about fraudulent activity that has been traced back to your organization. He feels that there may have been a security Breach within your systems and needs you to come into work immediately to help manage the incident. Arriving at the office and on your way to a meeting that has been called, you begin to think to yourself although you’ve managed smaller incidents such as malware outbreaks, your organization has never managed anything like this. Glancing around the meeting room at the assembled members of the public relations, legal, IT, security, and executive team, there is a common look of despair and disbelief. No one appears to be in control and at that moment you begin to get a sick feeling in your stomach as management asks the dreaded questions; How do you begin to investigate and manage the Breach? How do you recover? What will investors make of this?
Unfortunately the above scenario is an all too familiar one and as cyber criminals gain greater sophistication, the number of Breaches are increasing and many organizations are no longer questioning whether a Breach will occur but understand that they will experience one or have already experienced one and don’t yet know it. The impact of these Breaches can be catastrophic with the 2011 Breach of Sony Corporation’s online videogame services serving as an example with reported losses of over $1 billion USD.1
Proactively preparing for a Breach has been proven to significantly reduce the associated impact to an organization by 23%.2 This book can serve as both a guide to aid in the proactive preparation for a Breach to minimize impact and as a reference that can be used to reactively qualify, manage, and recover from Breaches.
What Is a Data Breach?
In this day and age, it’s difficult to ignore the fact that cyber security is on everyone’s mind. Whether it surfaces in a discussion within the Boardroom or the lunch room, the discussion doesn’t go far before cyber security and data Breaches are discussed. Often it’s about the latest organization to fall victim to a Breach or what an organization is or should be doing to protect itself. A Google search of “data Breach” will result in millions of hits, many with conflicting definitions of what a data Breach is. I will not debate which definitions are correct or which ones are not; what I will do is define key Breach-related terms that are used throughout this book to ensure proper context and clarity.
▪ Security Event: An action directed to a system, network, or human intended to alter the target’s state
▪ Security Incident: An event that violates organizational, regulatory, legislative or contractual security, or privacy policies
▪ Data Breach (“Breach”): A security incident that:
▪ Involves the intentional or unintentional access, disclosure, manipulation or destruction of data; or
▪ Meets specific definitions of a “Breach” as per state/province or federal laws or active contracts with clients, third parties or partners
Looking at our three definitions, most organizations have millions of events that occur on any given day, a subset of these events will be qualified as actual security incidents, and a subset of those incidents will be qualified as Breaches. It is good practice to treat all incidents as potential Breaches until they can be properly qualified, if not an incident not managed with the urgency and attention of a Breach, can later be qualified as one, and can expose the organization to increased lawsuits, fines, and reputational damage. We’ll talk more about this later in this chapter.
Our Breach definition is holistic in nature and covers most known Breach scenarios. Popular examples that fit this definition include a cyber criminal breaking into a computer to steal data; a malicious insider who abuses personal access to systems and alters or discloses data to unauthorized users; or an employee or third party who inadvertently losses data contained on a backup tape, USB key, or other forms of storage media.
Breaches are not singular events that can be solved by bringing a few technologically savvy team members into a room. Breaches are one of the most complex challenges a business can face and require proper preparation in order to ensure they are managed throughout their entire lifecycle.
Lifecycle of a Breach
Cyber security for decades has been viewed by many primarily as a technology issue. This narrow view unfortunately has extended to Breach management resulting in Breach response plans being developed focusing squarely on technological response. With this focus, they often center around how to quickly identify and remove a compromised server or laptop from a network in order to limit impact to business operations. Technological response, however, is just one phase of a series of events a Breached organization will need to go through in order to recover. This series of events is referred to as a Breach lifecycle. The lifecycle begins before the Breach is detected and ends long after the Breach has vanished from the headlines and business operations have resumed. We will refer to this entire process as the data Breach lifecycle which is illustrated in Fig. 1.1.
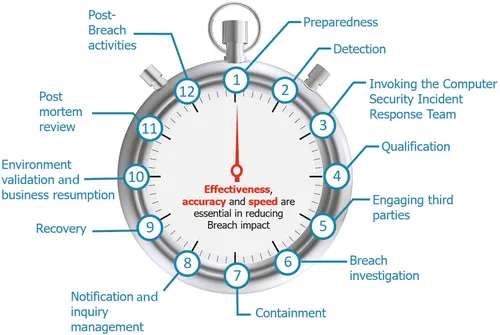
In-line with other business and technology lifecycles, there are outliers which may not traverse the Breach lifecycle in their entirety or in the same order as captured (Table 1.1). This Breach lifecycle, however, does encompass a wide range of Breaches and will be used as the basis of structured proactive Breach readiness within this book. Understanding the Breach lifecycle is a critical step in ensuring holistic Breach prevention planning for an organization.
Table 1.1
Data Breach Lifecycle Phases
| Phase | Description | Chapter Reference | |
| 1 | Preparedness | The steps an organization takes in advance of a Breach to identify sensitive information, implement cyber defenses and detection capabilities, and to develop and test a Computer Security Incident Response (CSIR) Plan to manage an incident. Most organizations that suffer a material security incident have gone through this phase and have operated under the impression they were covered to an acceptable level. However, often errors in asset identification, security strategies, and incident response capabilities are quickly highlighted during and after management of an incident and organizations will almost always revisit this step after an incident to further improve preparedness including bolstering cyber security controls and response capabilities based on lessons learned. This phase is the beginning and the end of the management of any material incident | Chapters 2, 3, and 8 |
| 2 | Detection | The moment an organization is alerted about a security incident. Whether the incident was detected by organizational security controls, staff or by a third party organization or individual. After the detection of an incident, it is critical that it is escalated appropriately to invoke the CSIR Plan. Several industry Breaches have resulted in increased impact to the victim organization due to the miss-handling of detection events which were ignored or not properly routed to the organization’s CSIR Team... |
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- About the Author
- About the Contributors
- Acknowledgments
- Chapter 1: An Overview of Data Breaches
- Chapter 2: Preparing to Develop a Computer Security Incident Response Plan
- Chapter 3: Developing a Computer Security Incident Response Plan
- Chapter 4: Qualifying and Investigating a Breach
- Chapter 5: Containing a Breach
- Chapter 6: Precisely Determining the Scope of a Breach
- Chapter 7: Communicating Before, During and After a Breach
- Chapter 8: Restoring Trust and Business Services After a Breach
- Chapter 9: Preparing for Breach Litigation
- Appendix
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Data Breach Preparation and Response by Kevvie Fowler in PDF and/or ePUB format, as well as other popular books in Business & Information Management. We have over one million books available in our catalogue for you to explore.