![]()
Dedication 1
This book is dedicated to my wonderful wife. Her support in giving me the opportunity to write this book cannot be expressed in simple words. For her continuous patience, encouragement, and for those times sacrifice. For her inspiration and incredible love for reading and editing, even when the subject matter may not have been of interest to her.
To my dear, loving wife Erin, you make me complete.
Thank you for tirelessly standing by my side and supporting me every step of the way. There are many times in one’s life where the task may seem too difficult, but having someone like you there as a guiding arm to encourage and to consult has been a blessing.
You have always been there when the times were challenging. It is with great honor to share this accomplishment with you.
To my wife, with love.
![]()
Dedication 2
In memory of Ron Knode.
Ron was a gift that left an impression of a smile, kind words, encouragement, and a unique way to make one think and see in a different perspective. I feel extremely honored to have had the opportunity to know and be mentored by Ron.
Ron, you have left an impression on many that will never be forgotten.
![]()
About the Author
Matthew Metheny, PMP, CISSP, CAP, CISA, CSSLP, CRISC, CCSK, is the founder of One Enterprise Consulting Group, LLC (1ECG), a privately held consulting firm that specializes in providing professional services that include cloud strategy and architecture, cloud security assessments, cloud migration, and cloud computing training. Mr. Metheny is a member of the Board of Directors for the Cloud Security Alliance (CSA) Washington, DC Metro Chapter, the CloudTrust Protocol (CTP) Working Group Co-Chair, and is a CSA-certified instructor for the Certificate of Cloud Security Knowledge (CCSK). Prior to 1ECG, Mr. Metheny held senior-level program management and executive-level positions with various consulting firms supporting both the federal government and the private sector with a focus on governance, risk management, emerging technologies, and security compliance. In addition, he is the founder of FedRAMP.net, which is focused on supporting cloud service providers and federal agencies with addressing the requirements of the Federal Risk and Authorization Management Program (FedRAMP). Mr. Metheny holds a Master of Science degree in Information Assurance from the University of Maryland University College (UMUC) and multiple internationally recognized certifications.
![]()
About the Technical Editor
Janis Orsino is an IT security consultant with more than two decades experience delivering technology and business consulting services for the U.S. federal government, in both civilian and defense sectors. She is presently a Senior Managing Consultant with IBM Global Business Services’, U.S. Federal Cybersecurity and Privacy Consulting Practice.
From 2009 to 2011, during a contract assignment with the Defense-wide Information Assurance Program, Janis helped to shape the Federal Risk and Authorization Management Program (FedRAMP) from its inception as a key advisor to the DoD Joint Authorization Board. She was also engaged in the cloud computing security guidance development efforts of the Federal CIO Council’s Information Security and Identity Management Committee, Network and Infrastructure Security Subcommittee.
Janis holds a Bachelor of Science degree in Social Psychology from Park University, a Graduate Certificate in Legal Studies from The George Washington University, and a string of industry certifications, including Certified Information Systems Security Professional (CISSP), Certified Information Systems Manager (CISM), Certified in Risk and Information Systems Control (CRISC), GIAC Security Leadership Certification (GSLC) and the Certificate of Cloud Security Knowledge (CCSK).
![]()
Foreword by William Corrington
In recent years “cloud computing” has emerged as a model for providing IT infrastructure, resources and services that has the potential to drive significant value to organizations through increased IT efficiency, agility and innovation. However, Federal agencies who were early adopters of cloud computing have learned that there are many challenges and risks that must be addressed in order to realize these benefits.
These early adopters have learned that the use of a Cloud Service Provider (CSP) represents a fundamental shift in how IT assets are deployed and delivered on a day-to-day basis. Successful adoption of cloud computing requires a change in approach to (among other things) security, privacy, end-user support, operations, acquisition and contract management. Challenges exist for CSPs as well. Many players in this emerging marketplace are new to doing business with the Federal government. As a result, they not only need to learn the nuances of the Federal acquisition processes, they must also address a myriad of security, privacy and certification requirements that are specific to Federal customers.
In order to mitigate these challenges and to catalyze the adoption of cloud computing within the Federal government, the Federal Cloud Computing Strategy was released on February 8, 2011. The National Institute of Standards and Technology (NIST) and the General Services Administration (GSA) have key roles in the implementation of this “Cloud First” strategy. NIST has developed a number of Special Publications that provide definitions, architectural standards and roadmaps for cloud computing. GSA has developed the Federal Risk and Authorization Management Program (FedRAMP) to define security, auditing, continuous monitoring and other operational requirements for Federal agency use of cloud computing.
I admire the groundbreaking initiatives that have been spearheaded by NIST and GSA. And yet, these efforts have created a new landscape with its own set of twists and turns that must be navigated by both Federal agencies and CSPs wishing to serve the Federal marketplace. What has been missing so far is a definitive reference guide that will allow anyone with a stake in Federal IT to quickly ascend the learning curve associated with the goals, objectives, implementation and operational aspects of the Federal Cloud Computing Strategy. Mr. Metheny’s book fills this gap by providing a comprehensive view of how and where cloud computing fits in the Federal government and how the critical components of the Cloud First strategy will work together in a complementary fashion.
I believe that this book will prove to be an invaluable resource to anyone who needs to successfully navigate the brave new world of Federal cloud computing. Cloud Service Providers (CSPs) will gain an understanding of the security and operational requirements that must be met in order to provide cloud-based services to Federal agencies. Cloud auditors who wish to provide services to Federal agencies or CSPs will learn the detailed requirements for becoming a Third Party Assessment Organization (3PAO). Federal agency CIOs, CTOs and CISOs will benefit from greater clarity regarding the impacts that the move to cloud computing will have on their existing IT strategy and operations.
The Cloud First strategy is a critical component of broader efforts that are underway to transform Federal IT in the 21st century. This book will provide excellent guidance to everyone who wishes to undertake that journey.
William Corrington
Founder and Chief Cloud Strategist
Stony Point Enterprises
(Former Chief Technology Officer at the U.S. Department of Interior)
![]()
Foreword by Jim Reavis
Cloud computing is an epochal change in the use of technology by mankind. Broadly considered, it represents the transition towards the use of compute as a utility, with profound implications. Just as when nations became electrified, the dawn of new industries, reorganization of societies and other unexpected outcomes are surely at our doorstep. Access to supercomputer capabilities, previously only available to small groups of people with millions of dollars, is now available to all.
The ability for individuals, small businesses and large enterprises to have “on demand” access to a virtually unlimited supply of compute power and storage challenges our ability to innovate. From discovering new drugs to unlocking the mysteries of the universe to finding better solutions for the human condition, we are only limited by our imagination.
Governments are no different than any other organization in their propensity to be impacted by, and leverage the cloud. The very largest problems facing governments have the potential to be solved in large part by the cloud. Cloud will also force government agencies to be more transparent and collaborative with the information that forms the backbone of their services. At the same time, a rush to adopt cloud computing without a sound understanding of its potential and risks could prove a devastating setback. This book, “Federal Cloud Computing: The Definitive Guide for Cloud Service Providers” is a timely addition to our shared knowledge of what cloud computing is, the inherent risks, regulatory requirements and the ecosystem of standards and best practices.
Cloud Security Alliance is a not-for-profit organization that is the leading global force in building trust within cloud computing. We congratulate author and CSA member Matthew Metheny for his excellent contribution to the topic of cloud computing within the US Federal government. We feel this book is must reading for anyone interested in information technology within our government. Both government consumers and providers must understand the regulatory requirements, the processes for making cloud services available and best practices to mitigate risks and operate cloud systems securely.
Cloud computing is not only in our future, but is here today. Whatever role you play in this topic, you have a mandate to find strategies to securely adopt cloud in an agile manner. “Federal Cloud Computing: The Definitive Guide for Cloud Service Providers” is an excellent coach to help define those strategies.
Best,
Jim Reavis
Executive Director, Cloud Security Alliance
![]()
Chapter 1
Introduction to the Federal Cloud Computing Strategy
Information in this chapter:
• Introduction
• A Historical View of Federal IT
• Cloud Computing: Drivers in Federal IT Transformation
• Decision Framework for Cloud Migration
Introduction
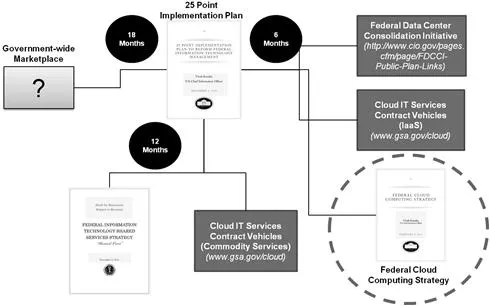
In February of 2011, the former US Chief Information Officer (CIO), Vivek Kundra, published the Federal Cloud Computing Strategy, herein referred to as the “Cloud Strategy.”1 The Cloud Strategy, as illustrated in Figure 1.1, was one of six major components of the US CIO’s roadmap to the cloud as defined in the 25 Point Implementation Plan to Reform Federal Information Technology Management.
Figure 1.1 25 Point Implementation IT Reform Plan—“Roadmap to the Cloud”
In the Cloud Strategy, the federal government’s strategic approach for the adoption of cloud computing technologies was described, including the potential benefits, considerations, and trade-offs [1]. The strategy also provided a decision framework for federal agencies to use in outlining their plan for using cloud computing to improve their efficient use of information technology (IT) investments to support their missions by leveraging shared infrastructures and economies of scale. This framework focused on changing how the government approaches IT and how it could effectively integrate cloud services into its existing IT portfolio.
The Cloud Strategy established a set of basic principles and guidelines through which decision-makers within federal agencies could use it to accelerate their secure adoption of cloud services. Through the strategy, ...