Introduction
The past two decades or so have been routinely called the Information Age. In the Information Age, names like Google, Facebook, and Twitter have become as commonplace in our vernacular as Ford, GE, and Wal-Mart. When you stop and think about it these companies don’t sell cars, refrigerators, or diapers. So what makes them relevant in these times? Information! These companies deliver services based on the collection and dissemination of information.
Information is valuable and as with any valuable asset it has to be protected. In order to properly protect an asset one needs to understand the dangers that the asset is exposed to. In the context of information as an asset this is where information security risk assessments come in to play.
In this chapter, we will be providing a primer on information security risk assessments with a focus on providing foundational knowledge regarding risk and its various components. We will then provide a high level overview of the components that make up a information security risk assessment, the major frameworks that provide guidance for conducting an assessment, and the laws and regulations that affect these assessments.
What is Risk?
All human endeavors carry some level of risk. This explains why throughout history risk has been a common topic of discussion. Strangely enough, even with all the discourse around risk it remains a very ambiguous concept. If you were to ask someone to provide you a definition of risk, they will very likely be able to provide you a reasonable answer; however, if you ask ten people, or even a hundred, you will likely receive a different definition from each person.
The ambiguity associated with defining risk is a fairly common roadblock to truly understanding risk. This is highlighted in the following statement from the Society of Risk Analysis:
“Many of you here remember that when our Society for Risk Analysis was brand new, one of the first things it did was to establish a committee to define the word “risk”. This committee labored for 4 years and then gave up, saying in its final report, that maybe it’s better not to define risk. Let each author define it in his own way, only please each should explain clearly what that way is (Kaplan, 1997).”
It is safe to say that there have been many discussions about risk but there have been few definitions provided or accepted. Of the definitions that we do have, the only thing that they share in common is the very fact that they share so little in common. This does not mean that people disagree on the meaning of ristk, it just highlights the fact that each person interprets risk, and the definition of risk, in a very different way.
It is our opinion that when defining Risk, it is important to discuss risk in the proper context. Different fields or disciplines will have different interpretations and perceptions of risk. For example, the definition of risk will vary between Information Security, Economics, Finance, Healthcare, and even within Information Technology itself. Understanding that the definition of risk will vary depending on who you are talking to will help you more effectively communicate your risk assessment within your organization.
Another key point to remember is that the information security risk assessment process you are undertaking is very likely not the only risk assessment being conducted at your organization. Usually there are multiple risk assessments occurring within your organization being driven by different departments. In a well run organization these reviews will be funneled into a centralized risk management function for consolidation and reporting. By providing a solid definition of risk in the context of your field you will be able to avoid misunderstandings when the time comes to report your conclusions to these various centralized risk management functions.
Important Definitions
So even though it gave the Society for Risk Analysis heartburn, let’s start trying to define Risk. It would be impossible to define Risk without first looking at its entomology. As with most English words, risk is likely of Greek origin; however, the earliest and possibly closest origin is from the Latin word “Riscum.” “Riscum” in turn could be the origin of various other words such as “Riscare” (Italian), and “Risque” (French), which is supposedly the origin of the English word “Risk.”
The list below shows the possible etymology of risk as well as the first definition:
• Riscum(Latin)—Danger, venture, crisis [1].
• Riscare (Italian—To hazard, to aventure, to jeaopard, to endanger [2].
• Risque(French)—Perill, jeopardie, danger, hazard, chance, aduenture (Costgrave, 1611).
• Risk (English)—Peril, jeopardy, danger, hazard, chance.
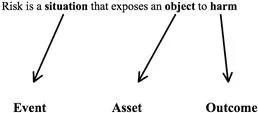
One thing that you’ll notice immediately is the commonality between the definitions associated with the word, or some derivative of the word, “Danger”—which connotes an exposure to harm. Thus it is fair to say that Risk can be defined as a situation that exposes an object to harm. This is probably one of the most common definitions of risk that you will encounter and frankly, although seemingly simple, not a bad one at all. Using this definition of risk is actually a good way to describe what you are doing to people in your organization who are not familiar with the concept of risk or risk assessments.
When you start the risk assessment process you will have to interact with other people and many of these people won’t be familiar with risk assessments and will only have a layman’s understanding of what risk is. If you start talking about the more technical concepts of risk, which we will delve into later in this chapter, you will more than likely confuse them or at the very least make them uncomfortable. Remember that not all people are familiar with risk assessments so it is always good to start off with the most basic definitions of risk when meeting with someone so that the person you are meeting with can easily relate to the topic.
As an example, when interviewing non-technical business unit representatives, one of the best ways to communicate about what you are working on is to tell them that you are assessing the exposure of the department to possible data breach or loss. This may not be entirely accurate as risk assessments are much more thorough than just that but it does provide a simple way to put your interviewee into the proper state of mind for you to ask other more detailed questions.
Going Deeper with Risk
Using the common definitions of risk would suffice; however, when we start delving into the subject, we need something more substantial. One of the most famous definitions of risk comes from Frank Knight, a renowned economist, in his work “Risk, Uncertainty, and Profit”:
Uncertainty must be taken in a sense radically distinct from the familiar notion of Risk, from which it has never been properly separated… The essential fact is that “risk” means in some cases a quantity susceptible of measurement, while at other times it is something distinctly not of this character; and there are far-reaching and crucial differences in the bearings of the phenomena depending on which of the two is really present and operating… It will appear that a measurable uncertainty, or “risk” proper, as we shall use the term, is so far different from an unmeasurable one that it is not in effect an uncertainty at all [3].
Frank Knight’s definition focuses on the difference between uncertainty and risk. Uncertainty is a state of having limited knowledge where it is impossible to exactly describe the existing state or future outcome [4]. Simply put, uncertainty is the state of not knowing.
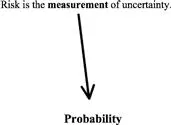
Risk on the other hand can be defined as the quantitation or measurement of uncertainty. When we start measuring uncertainty, it is at this point when it becomes risk. Thus, risk is measureable while uncertainty is not.
Though this definition does have its critics, we believe that this definition presents a simple yet elegant description of risk because of the key concept of “measurement.” Risk assessments are primarily an exercise of measurement. An organization without a risk assessment process cannot identify, much less measure, their risks and their level of exposure will remain in an uncertain state. An organization that is in an uncertain state cannot protect against possible dangers to itself until it is able to identify and measure them.
It is important to note that Knight’s definition is heavily influenced by probability theory, which during that time was just taking hold. In fact, in most common risk assessment methodologies, probability is an integral component, which now brings us to a discussion of the various components of risk.
Components of Risk
So far, we have provided high-level definitions of risk; however, you have probably heard the concept that “An entity is a sum of its parts.” Risk can be described in a very similar manner (see Figure 1.1). In order to break risk down to its individual components, let us use the definitions that we have used so far as illustrated in Figure 1.2.
Figure 1.1 Individual Components of Risk
Figure 1.2 Probability as Component of Risk
Our first definition of risk has alrea...