![]()
Section II
Emerging Trends
The first section of the book addressed the growing problem of the APT. With the APT, an organization’s focus needs to shift from dealing with the cyber common cold to cyber cancer. Based on the stealthy, targeted and data focused method of the adversary, many traditional security architectures are not effective against the new threat. New challenges require new solutions.
The second section of the book will focus on emerging trends that organizations who want to properly defend against the APT need to start doing. The following are the chapters that will be covered in section II:
Chapter 5: Protecting Your Data
Chapter 6: Prevention is Ideal but Detection is a Must
Chapter 7: Respond and Recover
Chapter 8: Technologies for Success
Traditional threats were more forgiving than the APT, which allowed organizations to make mistakes, overlook critical principles and not focus in on what is important. While the APT is not an insurmountable problem, it is if organizations do not change their approach to security. The chapters in this section redefine how to approach security to properly defend an organization against the next generation of advanced threats.
![]()
Chapter 5
Protecting Your Data
Introduction
With everything going on in the world of cyber-attacks and organizations not always prepared to deal with the APT, it is easy to lose sight of what is important. The one fundamental truth of cyber security, it is and has always been about understanding, managing, and mitigating risk to an organization’s critical information. While saying that statement is easy, understanding that statement is harder, but implementing it is even more difficult. We have many customers we work with who will nod their head in agreement when we state that security is all about your data or critical information. However, when we ask a simple question, what is your most critical information, they cannot always answer the question.
You cannot protect an organization, if you do not know what you are protecting. The first question is whether you can write down your organization’s most critical information. If you can write down the list of your organization’s most critical information, the next question is where does it reside and who has access to it. This was never an easy question but today it is much harder because our networks are more porous and our data is more portable. In the past, all information resided on a set of servers that were typically tightly controlled. All of the data resided on those servers and all access control was applied to the data residing on those servers. Today data might centrally be stored on a set of key servers but it quickly gets moved to other devices. Cloud and mobility are gaining a lot of attention on the security side because it changes the entire paradigm. Now information is available in many locations by many people and controlling access can be quite difficult. In addition, new information can be created instantly by anyone who has a portable device or any electronic equipment. The problem is in many organizations talking about data protection is futile at best, because they do not have a good handle of what their organization’s most critical information is and where it resides.
The bottom line is you cannot protect information if you do not know what it is, where it is, and who has access to it. Therefore, data discovery and asset management is a critical component of protecting against the APT. Being on the offense is always easier than the defense. Even though that will always be the case, the unfortunate part today is that we have made it even easier for attackers. By having information on many devices (i.e. bring your own device—BYOD) and in many locations (i.e. cloud) means we have given the attacker many options to steal information. Since the APT is so effective at reconnaissance and scanning, the exploiting piece is almost trivial. The reason is that with the proper open source searching and intelligence, an adversary can locate and find most of the information they need publicly or at least identify the people who have it. Once this is done it takes a targeted attack to compromise and break into the organization. Once inside, since many organizations do not do a great job of data protection, the attacker just needs to find and extract the critical information they are after. Many organizations still take the M&M approach to security. They have a hard outer shell or perimeter but a soft gooey center. When DMZ systems were being targeted this approach had some merit, creating a robust strong perimeter. Today where the internal user is being targeted and the attacker can easily get inside, the gooey center means the house of cards collapses pretty quickly. By more strictly controlling information and limiting where it resides, can make it much harder for the attacker.
The other important misconception to point on when talking about data protection is the word data theft. Every organization is concerned with theft of their information but theft is not the right word. Theft implies someone stealing an object and you no longer have the benefit or use of that object. For example, theft of a car implies that someone took your car and you no longer have access to it. With traditional theft you can visibly tell that your car has been stolen. It is easy to detect and know that it happened. The problem with data theft is it is not theft, it is really data copying. In most cases when someone steals your information, they copy your information but it is still available to you. The good news is that you did not lose use of that information, like you would with traditional theft. The bad news is that you have no easy way to tell that your information has been stolen. This is one of the reasons why the APT can be so stealthy. The threat is data focused, but once it identifies the critical information, it makes a copy and leaves. Since there is nothing visible, it is hard for organizations to detect that anything is happening or did happen. Remember our key rule, prevention is ideal but detection is a must. We also have to remember that attackers will often use encryption to bypass our traditional detection measures so behavior patterns, not signatures need to be examined to detect data theft.
Data Discovery
While it sounds like a painful exercise, understanding, discovering, and controlling your data is a critical component to properly defend against the APT. When I was growing up there where no cell phones or pagers and when you left your house for the evening there was minimal communication with your parents. To help promote child protection and safety, there would be commercials run in the evening that would come on and show the current time and then state it is 10:05 do you know where your children are. Today with mobile computing and the cloud, they should start running similar commercials; it is 10:05 do you know where your data is. The scary part is most organizations do not. We have focused so much on availability of information, allowing it to be accessible from any location, we forgot about least privilege tied with need to know which requires only giving people the access they need to do their job, when they need it and all other access should be cut off.
If you are not convinced that this is a problem, identify a user in your organization and determine what information they need access to in order to perform their job. Once that is done, take their laptop and list all of the information that is contained on their laptop. I will almost guarantee that there is at least 40% more information on their laptop than what is needed for them to be effective. All of the extra information is just an accident waiting to happen.
In a perfect world, we would want to track and control all information. However, this is not practical so when we discuss data discovery we let threat drive the train just like we did with calculating risk. What is the information that, if it was compromised, would cause significant damage to your organization? Once that information is identified, all locations in which it resides need to be identified. If it is sensitive information, hopefully all of the location are internal, but external and mobile devices should also be checked to make sure there is a full understanding of the exposure. Once a list of all of the locations the information resides is created, create a list of where it should reside based on risk. Compare the two lists and identify any location where the information represents too great an exposure. In a perfect world, we would remove the information from those locations. However, in the real world there could be situations where the information needs to reside in a certain location even though it is too high a risk. In those cases, proper risk mitigation measures should be put in place to minimize the exposure to an acceptable level.
The bigger problem with data discovery is removing information from locations where it should not be stored. Simply deleting it off of a server is not enough, backups and local storage also have to be considered. The more difficult piece is sensitive information that is found on the Internet. Depending on where it is stored, in some cases it is almost impossible to remove information from the Internet. Therefore an organization should remove what it can but more importantly determine how it got there and put a process in place to make sure it does not occur again in the future. Even if the information cannot be fully removed, understanding that sensitive information is exposed allows an organization to put together an appropriate defensive response. Knowledge is power and knowing about a problem is better than thinking everything is fine and not realizing how exposed you really are.
Protected Enclaves
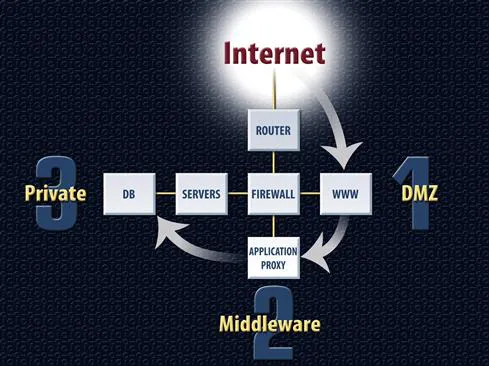
Many organizations have focused a lot of energy in security on implementing network security products, but they have not focused as much energy on building a secure network architecture that can withstand an attack and minimize data exposure. From an Internet perspective, many organizations have done a good job with data segmentation limiting exposure from the Internet, see Figure 5.1.
Figure 5.1 Creating a Network Architecture with Proper Segmentation is Required to Protect Critical Data
From a traditional threat perspective, the focus primarily has been on protecting information on servers from compromise from the Internet. This model is effective if the organization follows three critical rules:
1. Any systems accessible from the Internet reside on the DMZ and DMZ systems never contain sensitive information. DMZ systems should be considered high risk and low trust based on their exposure and potential chance of being compromised.
2. Any systems with sensitive data should reside on the private network and private network systems are never accessible from the Internet. Based on their limited access and separation from high-risk networks, private network systems are considered to be high trust and low risk.
3. The only way DMZ systems can communicate with private network systems is by going through an application proxy on a middleware tier. While DMZ systems do need to access information from the private network, you never want a high-risk systems directly communicating with a low-risk system. By going through an application proxy that makes two separate connections, this can be accomplished.
This architecture is called a n-tier architecture. While the number of tiers can be expanded, Figure 5.1 shows a traditional three-tier architecture, which is the minimal number of tiers you always want to use. This is the starting point for building out a secure infrastructure that allows services to be offered from the Internet. It is also important to point out that a three-tier architecture is a starting point. You can add more tiers but you should never go with less. If the risk is to great of only having one level of protection between the untrusted and trusted networks, additional middleware tiers can be added in. This would create a four-, five-, or six-tier architecture. You can add in more tiers to increase the overall security. The balance is that the more tiers there are, the more security and the more complexity. The goal is to have as few tiers as possible (without going below three) but have the maximum number of tiers for a proper level of protection.
Creating and building this infrastructure is critical to protect our servers but the problem is the threat approach has changed. However, it is critical to still keep a robust infrastructure with regard to Internet facing systems since attackers will utilize whatever works. One of the reasons why not as many attacks go after DMZ systems is because of the amount of time that has been invested in securing these systems. They are harder to break into for most organizations. While the APT will still target servers utilization zero-day attacks, typically the easier way into an organization is the client.
One of the main reasons that the client is targeted is because it resides on the private network and many private networks are fairly flat and open. This gives the attacker direct access to the information they need. By compromising a system on the private network, this gives the attacker a pivot point to extract information and create a command and control channel within the victim organization. As a simple check, pick any client on your network and see how many servers they have access to. Compare this to the list of servers they need access to do to their job. If you are like most organizations, internal users or anyone with a node on the private network can access more information than they should. Attackers recognize and take advantage of this weakness.
Once critical data is discovered, it needs to be protected with secure enclaves. If you go back to Figure 5.1, the three-tier architecture was created to protect the data when DMZ systems were being attacked. This was created out of necessity when an organizations Internet facing systems started to be targeted. Today the target is now the end user and the same architecture needs to be created to protect the new targets, the client. Using Figure 5.1 as a guide, replace the DMZ with the user enclave. Based on the APT, the client is now the target and your critical information needs to be protected from them. All client systems need to be put on a client segment which is high risk and low trust. All critical systems based on data discovery need to be put on a separate segment which is high trust and low risk. The only way users should be able to communicate with critical data is through an application proxy on a private middleware tier. By doing this if a user system gets compromised it can be controlled and contained. In addition to the three rules we have for servers on the DMZ, the three rules we have for clients when dealing with the APT are:
1. All client workstations and laptops should be on a private client network and client systems should contain a minimal amount of information. Utilizing thin clients or virtual machines can help contain and minimize the amount of information stored on the client system. For extra protection, the client workstation network enclave can be further subdivided to minimize overall exposure. For example if 10,000 clients are on one network and it gets compromised, the malware can take over all 10,000 systems. If we put 100 systems each on separate firewalled segments, the amount of damage will be controlled. Finally, it is a good idea to put tablet systems and smartphones on separate s...