![]()
Chapter 1
Client-Side Attacks Defined
Information in this chapter:
Client-Side Attacks: An Overview
Types of Client-Side Attacks
One of the bigger threats that users will face today is client-side attacks that expose the vulnerability of the end user and his or her system. Over the last five years the amount of client-side attacks has increased dramatically leading to a statement by the SANS Institute that this type of attack represents historically one of the most critical Internet security vulnerabilities in existence.
In the past attackers wishing to cause harm, damage, or expose sensitive data would generally go after the servers themselves using a class of attacks known collectively as server-side attacks. These attacks were successful because in the past, the servers themselves were not as well defended as they are today. With new security advances, methodologies and processes, this is no longer the case. The server-side attack is now severely limited by security professionals putting an enhanced focus on edge security, securing the network and vendors of products writing and producing better products for safeguarding key systems. Because the attack vector has been protected, hackers and attackers had to find a new route in.
Since the server-side (and in adversely the network-side) became the focus and were better protected, the applications used on the servers and the systems in which use the applications became the new target. In sum, applications that exist on the server-side and the vulnerabilities associated with them are better understood and defended, so attackers have shifted their focus to the desktop environment and the weaknesses found there.
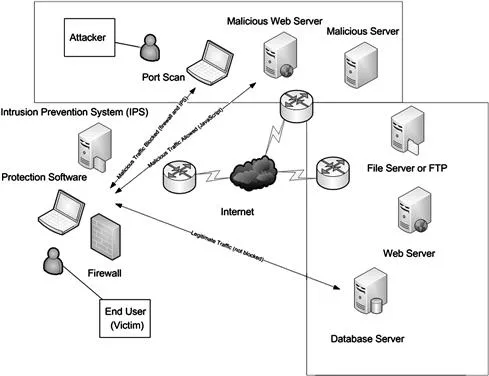
Whereas server-side attacks seek to compromise and breach the data and applications that are present on a server, client-side attacks specifically target the software on the desktop itself. Applications such as web browsers, media players, email clients, office suites, and other such applications are all prime targets for an attacker. This also does not encompass many of the in-house developed applications that are widely used in many organizations worldwide. Home-grown or applications built in-house add other items to the mix due to the fact that applications that fit into this category may not undergo any sort of formal security testing. It also doesn’t take into account that a server system is easier to patch, protect and monitor then the many clients that attach to it as well as the even more diverse operating systems that are used. Multiply that by the amount of different applications used and you can see that the problem grows exponentially making this a difficult problem to solve. The wide and diverse range of software present on the desktop in an organization presents a large target for attackers and a major concern for the security professional. In fact for the security professional overlooking the client-side attack is an easy way to miss one of the single most dangerous mechanisms for impacting security in an organization. Figure 1.1 shows an example of a typical client-side attack.
Figure 1.1 An Example of a Typical Client-Side Attack
Note
Servers in the context of this text will refer to the environment that is hosted on a specialized system designed to service users and respond to requests of various types. The server environment can and does include server based applications such as those that provide streaming audio and video, serve documents, and perform ecommerce functions to name just a few. While servers will be covered in this text at various points they are not the main focus of this text as our intention is to focus on attacks on the client-side. The server-side environment represents a tremendous level of complexity and other issues that exceed the scope of this book and therefore will only be covered as they relate to client-side attacks.
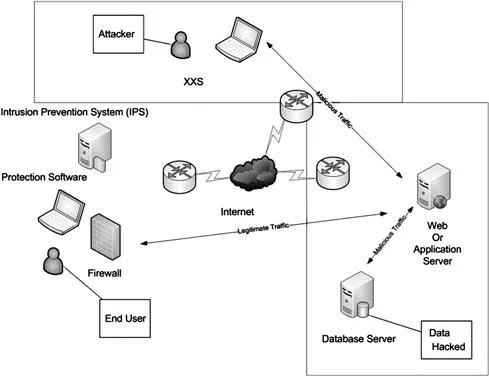
In this book we will examine what constitutes a client-side attack, the different types of attacks, how they work, and how to defend against them in the real world. While every type of attack that is available cannot be covered in this text, we will review the most common. In advanced chapters we will highlight more complex attacks. By learning about the most common and more complex attacks, you will gain a better understanding of how these attacks work and in turn be able to protect against them more effectively in the future. It is also important to note that new security flaws are found each day as more and more applications are upgraded, rolled out and created (see Figure 1.2).
Figure 1.2 An Example of a Cross-Site Scripting (XSS)
Note
In this text we will use both terms “client” and “user” to refer to the recipient on the other side of the connection from the server. In the context of this book “client” shall refer to the system itself to include the carbon-based element operating it while “user” will refer to the individual alone that is operating the computer system. While both the “client” and “user” can be and are victims of attacks both can be targeted in different ways which will be illustrated throughout this text.
Client-Side Attacks: An Overview
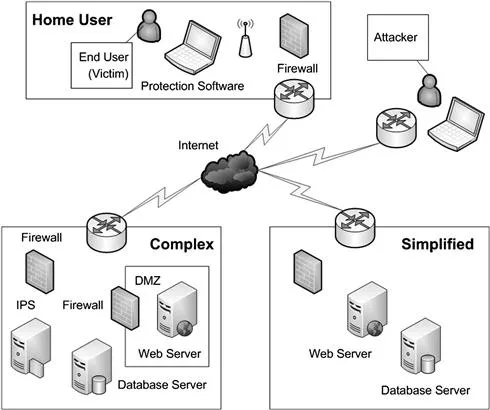
While we will cover more about what constitutes a client-side attack in Chapter 2, Chapter 1 provides a basic overview. We will then move on to cover attacks in more detail in later chapters. Later chapters will explain more in depth why the client is susceptible to attacks and how the attacker is able to manipulate the system so easily, whether it be a code flaw or lack of security applied to the operating system as example. It is important for us to first take a high level look at these classes of attacks and what makes them possible. In order to better understand client-side attacks it is worthwhile where applicable to compare and contrast them with their well-known cousins known as server-side attacks (see Figure 1.3).
Figure 1.3 Basic Security Architecture
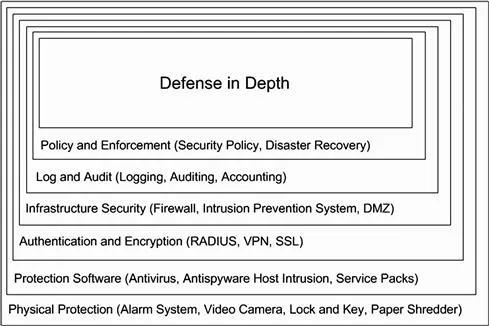
As mentioned previously attackers have traditionally concentrated their attacks on the server-side and the applications, data, and services hosted there. During normal operation a server-side application and the server itself will expose several types of services that will vary depending on the intended role of the server (i.e. document management or streaming video). Each service that a server exposes to the world is one more potential target that an attacker can exploit for whatever purpose they may have in mind. Even with a simple web-server that hosts static content the possibility of attack is present as there are services running that can be exploited. Add to a web-server the ability to host dynamic content such as Java Server Pages (JSP), Active Server Pages (ASP), or even Hypertext Preprocessor (PHP) and the situation gets even worse as even more services with their potential vulnerabilities are layered upon one another. These server-side scripting languages are often used provide dynamic content are generally embedded directly into the HTML code used to produce the pages you view, which also run scripts that could execute commands as an example (see Figure 1.4).
Figure 1.4 Defense in Depth
Note
Remember that even though this book focuses on the client-side attacks it is important to note that server-side attacks are still of strategic value and depending on their desired outcome an attacker may opt to use server-side attacks instead. For example, attacks such as format string, input validation and others may yield useful info from a victim that client-side attacks cannot achieve successfully. Other attacks such as the well-known SQL injection have client-side counterparts that are similar in nature, but achieve different results depending on whether the target is a client or server. Additionally modern technologies such as Google Gears and HTML 5 have not only made the web a more exciting place, but they have also made previous attacks more dangerous and likely.
Never forget that an attacker will typically have multiple tricks in their toolkit and will use whatever is perceived to get the best results at a given time. It is for this reason that you must always properly assess your vulnerabilities and put measures in place to mitigate the risk accordingly.
The list of potential vulnerabilities available on a server and its services is a long one, but some of the more common ones are:
• Malicious HTTP requests: This includes improperly formed or what are known as illegal arguments in an HTTP request. These are generally executed to trick an end user into thinking they are accessing legitimate code, which in reality malicious code (malcode) is being “smuggled” into the equation. HTTP Request Smuggling (or HRS) is used between a client and an application server and commonly executed when there is a proxy system in between.
• Buffer overflows: Vulnerabilities of this type are common in software and regularly exploited by savvy attackers. These are generally executed to produce a Denial-of-Service (DoS) attack to prevent legitimate connections from taking place by flooding buffers with bogus requests.
• Scripting errors and attacks: As will be introduced chapter 2, scripting errors take advantage of handling or coding errors to enact an attack against a client. This can be done via scripting languages such as JavaScript, VBScript, Flash scripting, and others. Cross-site scripting (XSS) is commonly used to bypass security controls by injecting the harmful content on the client-side or end user’s web browser.
• CGI errors and attacks: CGI or Common Gateway Interface programs run on ...