
eBook - ePub
Hack the Stack
Using Snort and Ethereal to Master The 8 Layers of An Insecure Network
- 481 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Hack the Stack
Using Snort and Ethereal to Master The 8 Layers of An Insecure Network
About this book
This book looks at network security in a new and refreshing way. It guides readers step-by-step through the "stack" -- the seven layers of a network. Each chapter focuses on one layer of the stack along with the attacks, vulnerabilities, and exploits that can be found at that layer. The book even includes a chapter on the mythical eighth layer: The people layer. This book is designed to offer readers a deeper understanding of many common vulnerabilities and the ways in which attacker's exploit, manipulate, misuse, and abuse protocols and applications. The authors guide the readers through this process by using tools such as Ethereal (sniffer) and Snort (IDS). The sniffer is used to help readers understand how the protocols should work and what the various attacks are doing to break them. IDS is used to demonstrate the format of specific signatures and provide the reader with the skills needed to recognize and detect attacks when they occur. What makes this book unique is that it presents the material in a layer by layer approach which offers the readers a way to learn about exploits in a manner similar to which they most likely originally learned networking. This methodology makes this book a useful tool to not only security professionals but also for networking professionals, application programmers, and others. All of the primary protocols such as IP, ICMP, TCP are discussed but each from a security perspective. The authors convey the mindset of the attacker by examining how seemingly small flaws are often the catalyst of potential threats. The book considers the general kinds of things that may be monitored that would have alerted users of an attack.* Remember being a child and wanting to take something apart, like a phone, to see how it worked? This book is for you then as it details how specific hacker tools and techniques accomplish the things they do. * This book will not only give you knowledge of security tools but will provide you the ability to design more robust security solutions * Anyone can tell you what a tool does but this book shows you how the tool works
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Extending OSI to Network Security
Introduction
“Everything old becomes new again.” The goal of this chapter is to take the well-known Open Systems Interconnect (OSI) model and use it to present security topics in a new and unique way. While each of the subsequent chapters focuses on one individual layer, this chapter offers a high-level overview of the entire book.
Our Approach to This Book
This book is compiled of issues and concerns that security professionals must deal with on a daily basis. We look at common attack patterns and how they are made possible. Many attacks occur because of poor protocol design; others occur because of poor programming or lack of forethought when designing code. Finally, the tools that are useful for identifying and analyzing exploits and exposures are discussed—the tools you will return to time and time again.
Tools of the Trade
The following sections examine “protocol analyzers” and the Intrusion Detection Systems (IDSes), which are the two main tools used throughout this book.
Protocol Analyzers
Protocol analyzers (or sniffers) are powerful programs that work by placing the host system’s network card into promiscuous mode, thereby allowing it to receive all of the data it sees in that particular collision domain. Passive sniffing is performed when a user is on a hub. When using a hub, all traffic is sent to all ports; thus, all a security professional or attacker has to do is start the sniffer and wait for someone on the same collision domain to begin transmitting data. A collision domain is a network segment that is shared but not bridged or switched; packets collide because users are sharing the same bandwidth.
Sniffing performed on a switched network is known as active sniffing, because it switches segment traffic and knows which particular port to send traffic to. While this feature adds much needed performance, it also raises a barrier when attempting to sniff all potential switched ports. One way to overcome this impediment is to configure the switch to mirror a port. Attackers may not have this capability, so their best hope of bypassing the functionality of the switch is through poisoning and flooding (discussed in subsequent chapters).
Sniffers operate at the data link layer of the OSI model, which means they do not have to play by the same rules as the applications and services that reside further up the stack. Sniffers can capture everything on the wire and record it for later review. They allow user’s to see all of the data contained in the packet. While sniffers are still a powerful tool in the hands of an attacker, they have lost some of their mystical status as many more people are using encryption.
The sniffer used in this book is called Ethereal, which is free and works well in both a Windows and a Linux environment. (Chapter 3 provides a more in-depth review of how to install and use Ethereal.) If you’re eager to start using Ethereal, more details about the program can be found at www.ethereal.com. (Ethereal’s name has been changed to Wireshark.)
Intrusion Detection Systems
Intrusion detection systems (IDSes) play a critical role in protecting the Information Technology (IT) infrastructure. Intrusion detection involves monitoring network traffic, detecting attempts to gain unauthorized access to a system or resource, and notifying the appropriate individuals so that counteractions can be taken. The ability to analyze vulnerabilities and attacks with a sniffer and then craft a defense with an IDS is a powerful combination. The IDS system used in this book is Snort, which can be used with both Linux and Windows and has industry wide support.
Snort is a freeware IDS developed by Martin Roesch and Brian Caswell. It’s a lightweight, network-based IDS that can be set up on a Linux or Windows host. While the core program uses a Command Line Interface (CLI), graphical user interfaces (GUIs) can also be used. Snort operates as a network sniffer and logs activity that matches predefined signatures. Signatures can be designed for a wide range of traffic, including Internet Protocol (IP), Transmission Control Protocol (TCP), User Datagram Protocol (UDP), and Internet Control Message Protocol (ICMP).
Snort consists of two basic parts:
■ Header Where the rules “actions” are identified
■ Options Where the rules “alert messages” are identified
To learn more about Snort, go to www.Snort.org.
Organization of This Book
This book is arranged in the same manner as the layers of the OSI model, which was developed to provide organization and structure to the world of networking. In 1983, the International Organization for Standardization (ISO) and the International Telegraph and Telephone Consultative Committee (CCITT) merged documents and developed the OSI model, which is based on a specific hierarchy where each layer builds on the output of each adjacent layer (see ISO 7498). Today, it is widely used as a guide for describing the operation of a networking environment, and also serves as a teaching model for hacks, attacks, and defenses.
The OSI model is a protocol stack where the lower layers deal primarily with hardware, and the upper layers deal primarily with software. The OSI model’s seven layers are designed so that control is passed down from layer to layer. The seven layers of the OSI model are shown in Table 1.1
Table 1.1
The Seven-Layer OSI Model
| Layer | Responsibility |
| Application | Application support such as File Transfer Protocol (FTP), Telnet, and Hypertext Transfer Protocol (HTTP) |
| Presentation | Encryption, Server Message Block (SMB), American Standard Code for Information Interchange (ASCII), and formatting |
| Session | Data flow control, startup, shutdown, and error detection/correction |
| Transport | End-to-end communications, UDP and TCP services |
| Network | Routing and routable protocols such as IP and Open Shortest Path First (OSPF). Path control and best effort at delivery |
| Data link | Network interface cards, Media Access Control (MAC) addresses, framing, formatting, and organizing data |
| Physical | Transmission media such as twisted-pair cabling, wireless systems, and fiber-optic cable |
The OSI model functions as follows:
1. Information is introduced into the application layer and passed down until it ends up at the physical layer.
2. Next, it is transmitted over the physical medium (i.e., wire, coax, or wireless) and sent to the target device.
3. Once at the target device, it proceeds back up the stack to the application layer.
For this book, an eighth layer has been added to the OSI model that is called the “people” layer (or “social” layer). Figure 1.1 shows the eight layers and interprets the services of each.
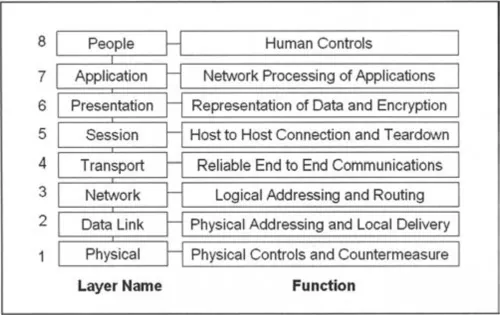
Figure 1.1 Hack the Stack’s Eight Layers
The People Layer
Layer 8 is known as the people layer, and while not an official layer of the OSI model, it is an important consideration; therefore, it...
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright page
- Acknowledgments
- Lead Author
- Contributing Authors
- Technical Editor
- Foreword
- Chapter 1: Extending OSI to Network Security
- Chapter 2: Layer 1: The Physical Layer
- Chapter 3: Layer 2: The Data Link Layer
- Chapter 4: Layer 3: The Network Layer
- Chapter 5: Layer 4: The Transport Layer
- Chapter 6: Layer 5: The Session Layer
- Chapter 7: Layer 6: The Presentation Layer
- Chapter 8: Layer 7: The Application Layer
- Chapter 9: Layer 8: The People Layer
- Appendix A: Risk Mitigation: Securing the Stack
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Hack the Stack by Stephen Watkins,George Mays,Ronald M. Bandes,Brandon Franklin,Michael Gregg,Chris Ries in PDF and/or ePUB format, as well as other popular books in Informatica & Sicurezza informatica. We have over one million books available in our catalogue for you to explore.