
Corporate Security Organizational Structure, Cost of Services and Staffing Benchmark
Research Report
- 76 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Corporate Security Organizational Structure, Cost of Services and Staffing Benchmark
Research Report
About this book
This research report presents the findings of a broad survey of corporate security programs conducted by the Security Executive Council's Security Leadership Research Institute (SLRI). The researchers' objective was to benchmark the state of the security industry in terms of organizational structure, budget, staff resources, board-level risk concerns, program drivers, and services provided. The level of responsibility each respondent reported for a list of 30 security programs or services is also compared across several organizational categories.This report can be used by security professionals for introspective analysis of the security team within their organizations, external review of the ways in which other organizations approach risk management, internal justification of security budgets and initiatives, and for performance metrics.Corporate Security Organizational Structure, Cost of Services and Staffing Benchmarkis a part of Elsevier's Security Executive Council Risk Management Portfolio, a collection of real world solutions and "how-to" guidelines that equip executives, practitioners, and educators with proven information for successful security and risk management programs.- Summarizes the key findings of a large survey on security programs conducted by the Security Executive Council's Security Leadership Research Institute (SLRI)- Breaks down survey responses by organization size, scope of responsibility, industry, and more in easy-to-read charts and tables- Provides invaluable insight into other organizations' existing security programs and services
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Survey Results
Section I: Organizational Demographics
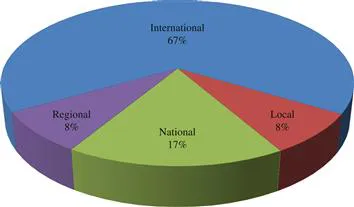
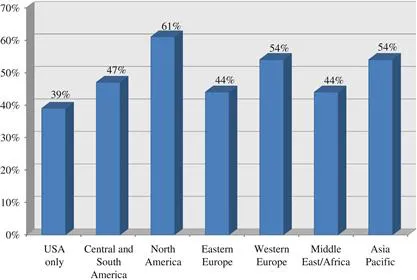
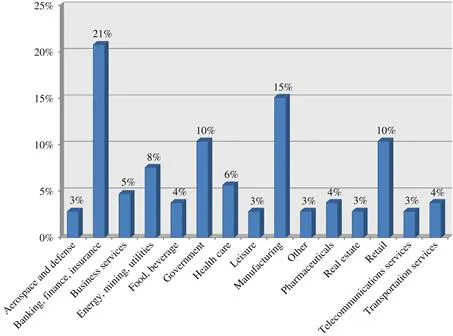
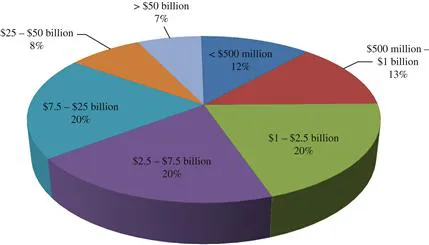
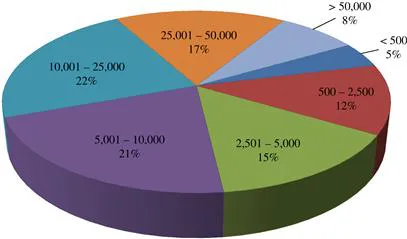
Section II: Respondent Demographics
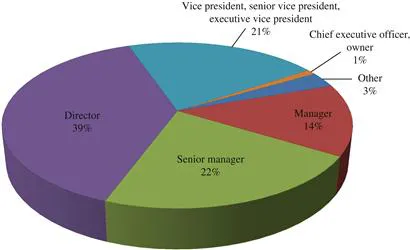
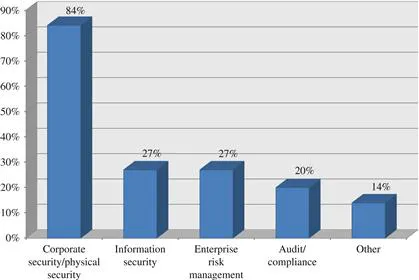
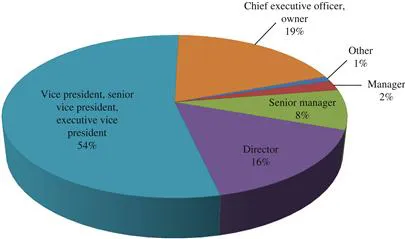
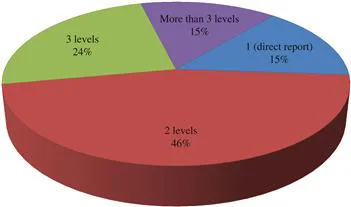
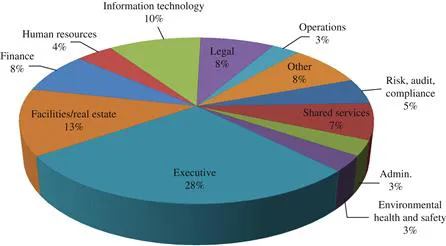
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- Executive Summary
- Survey Results
- Appendix A. Board-Level Risk Categories
- Appendix B. Data Cleansing
- Reference
- About the Authors
- About Elsevier’s Security Executive Council Risk Management Portfolio