
Introduction to the Theories and Varieties of Modern Crime in Financial Markets
- 272 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Introduction to the Theories and Varieties of Modern Crime in Financial Markets
About this book
Introduction to the Theories and Varieties of Modern Crime in Financial Markets explores statistical methods and data mining techniques that, if used correctly, can help with crime detection and prevention. The three sections of the book present the methods, techniques, and approaches for recognizing, analyzing, and ultimately detecting and preventing financial frauds, especially complex and sophisticated crimes that characterize modern financial markets.The first two sections appeal to readers with technical backgrounds, describing data analysis and ways to manipulate markets and commit crimes. The third section gives life to the information through a series of interviews with bankers, regulators, lawyers, investigators, rogue traders, and others.The book is sharply focused on analyzing the origin of a crime from an economic perspective, showing Big Data in action, noting both the pros and cons of this approach.- Provides an analytical/empirical approach to financial crime investigation, including data sources, data manipulation, and conclusions that data can provide- Emphasizes case studies, primarily with experts, traders, and investigators worldwide- Uses R for statistical examples
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Insider Trading
Abstract
1 Background
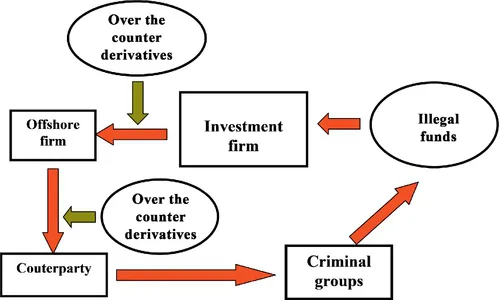
2 Overview of Insider Trading
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- Preface
- Prologue
- Acknowledgments to the First Edition
- Mr X Anonymous Interview
- Nick Leeson: Interview
- I: Short History of Financial Markets
- II: Origin of Crime on Wall Street
- III: Typologies of Crime on Financial Markets
- IV: Modern Financial Crime
- Epilogue
- Bibliography
- Index
- Sync with Jellybooks