
Securing Intellectual Property
Protecting Trade Secrets and Other Information Assets
- 288 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Securing Intellectual Property
Protecting Trade Secrets and Other Information Assets
About this book
Most employeers are astounded at how easily and quickly their proprietary information can get out of their control. In a large number of cases, theft of trade secrets often involves employees leaving a company to start their own business or work for a direct competitor.Nearly all books that address the topic of trade secrets have the "spy vs. spy perspective. The author approaches the topic from a practical business perspective and not simply creating "paranoia for paranoia's sake. The material for this book comes from the author's extensive work experience as a computer forensics consultant and manager on numerous theft of trade secrets cases.- No-nonsense solutions to the most common intellectual property problems facing security managers, computer security professionals, corporate legal counsel, and human resource managers- Sample agreements and forms that address specific business needs- Coverage of threats ranging from physical security lapses to hackers to social engineering
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
Chapter 1. Elements of a Holistic Program
Introduction
False Memes Lead People the Wrong Way
From the Industrial Age to the Information Age
Figure 1.1. Personnel, Physical, and Information Security Mitigate the Scope of Risks and Threats
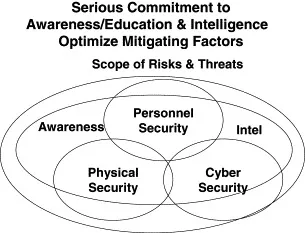
Figure 1.2. Integrating Physical, Personnel, and Cyber Security

Figure 1.3. Serious Commitment to Awareness/Education and Intelligence Optimize Mitigating Factors
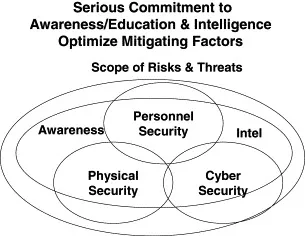
- Organization: Where security reports within an organization is perhaps the most vital issue of all. Consider appointing a Chief Security Officer (CSO), who reports to either the Chief Executive Office (CEO) or the Chief Financial Officer (CFO). This person should hold the reins of personnel security, physical security, and information security, and should not be a stranger to the boardroom.
- Awareness and Education: Educate your workforce on an ongoing basis about the threats of economic espionage, intellectual property theft, counterfeiting, and piracy. Help them understand your expectation that they will protect the enterprise's intellectual property, and by extension, their own livelihood. Provide general education for the entire workforce, and specialized education for executives, managers, technical personnel, among others.
- Personnel Security: Implement a “Personnel Security” program that includes both background investigations and termination procedures. You need policies that establish checks and balances, and you need to enforce them. Know the people you are going to hire. Don't lose touch with them while they work for you. Consciously manage the termination process if and when they leave the enterprise.
- Information Security: Recruit certified information security professionals (e.g., CISSP, CISM, etc.). Adopt best practices, and establish a baseline. Utilize appropriate information security technologies, such as fire...
Table of contents
- Brief Table of Contents
- Table of Contents
- Copyright
- Preface
- Chapter 1. Elements of a Holistic Program
- Chapter 2. Trade Secrets and Nondisclosure Agreements
- Chapter 3. Confidentiality, Rights Transfer, and Noncompetition Agreements for Employees
- Chapter 4. IT Services—Development, Outsourcing, and Consulting
- Chapter 5. How to Sell Your Intellectual Property Protection Program
- Chapter 6. Case Study
- Chapter 7. When Insiders and/or Competitors Target a Business's Intellectual Property
- Chapter 8. When Piracy, Counterfeiting, and Organized Crime Target a Business's Intellectual Property
- Chapter 9. Physical Security
- Chapter 10. Protecting Intellectual Property in a Crisis Situation
- Chapter 11. Top Ten Ways to Shut Down Hackers
- Appendix 1. Mutual Non-Disclosure Agreement
- Appendix 2. Evaluation Agreement (Pro-Recipient)
- Appendix 3. Employee Agreement
- Appendix 4. Software Development Agreement
- Appendix 5. Software Consulting Agreement (Favors Consultant)
- Appendix 6. Software Consulting Agreement (Favors Customer)
- Appendix 7. Web Site Development Agreement
- Appendix 8. Web Hosting Agreement
- Appendix 9. U.S. Department of Justice Checklist for Reporting a Theft of Trade Secrets Offense
- Index