
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
We live in an age saturated with surveillance. Our personal and public lives are increasingly on display for governments, merchants, employers, hackers—and the merely curious—to see. In Windows into the Soul, Gary T. Marx, a central figure in the rapidly expanding field of surveillance studies, argues that surveillance itself is neither good nor bad, but that context and comportment make it so.
In this landmark book, Marx sums up a lifetime of work on issues of surveillance and social control by disentangling and parsing the empirical richness of watching and being watched. Using fictional narratives as well as the findings of social science, Marx draws on decades of studies of covert policing, computer profiling, location and work monitoring, drug testing, caller identification, and much more, Marx gives us a conceptual language to understand the new realities and his work clearly emphasizes the paradoxes, trade-offs, and confusion enveloping the field. Windows into the Soul shows how surveillance can penetrate our social and personal lives in profound, and sometimes harrowing, ways. Ultimately, Marx argues, recognizing complexity and asking the right questions is essential to bringing light and accountability to the darker, more iniquitous corners of our emerging surveillance society.
For more information, please see www.garymarx.net.
In this landmark book, Marx sums up a lifetime of work on issues of surveillance and social control by disentangling and parsing the empirical richness of watching and being watched. Using fictional narratives as well as the findings of social science, Marx draws on decades of studies of covert policing, computer profiling, location and work monitoring, drug testing, caller identification, and much more, Marx gives us a conceptual language to understand the new realities and his work clearly emphasizes the paradoxes, trade-offs, and confusion enveloping the field. Windows into the Soul shows how surveillance can penetrate our social and personal lives in profound, and sometimes harrowing, ways. Ultimately, Marx argues, recognizing complexity and asking the right questions is essential to bringing light and accountability to the darker, more iniquitous corners of our emerging surveillance society.
For more information, please see www.garymarx.net.
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription.
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn more here.
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes! You can use the Perlego app on both iOS or Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Yes, you can access Windows into the Soul by Gary T. Marx in PDF and/or ePUB format, as well as other popular books in Social Sciences & Science & Technology Law. We have over one million books available in our catalogue for you to explore.
Information
Publisher
University of Chicago PressYear
2016Print ISBN
9780226285917, 9780226285887eBook ISBN
9780226286075Part I
Concepts: The Need for a Modest but Persistent Analyticity
Frango ut Patefaciam.
PALEONTOLOGICAL SOCIETY MOTTO
The translation of that phrase—“I break in order to reveal,” describes the intention of the next four chapters, which break surveillance into major components and offer varieties of rearrangement. These chapters also do some crosscutting along analytic dimensions to unite seemingly dissimilar phenomena and separate seemingly similar ones—for example, identifying both enemy spies and loving parents as surveillance agents, or making a clear distinction between a drug test categorically applied to transportation workers and to applicants for college loans.
My goals in classification are to define and organize the empirical patterns; to assess what is new about the new surveillance and the extent to which it is new; to specify the variation across time periods, settings, and methods that theory needs to account for; and to offer a systematic way for grounding (and comparing) ethical and policy judgments about particular tactics and practices.
Having identified ways of classifying the phenomena of interest, the analyst can then construct still-broader types by combining and reconfiguring the variables.1 The social scientist may next seek to generalize across cases by linking concepts in the form of empirically assessable hypotheses and then testing them. As we move from naming, to hypothesizing, to testing, the task becomes more difficult. There is a division of labor by task, skills, and interests of the researcher and time period. The first need is for improved tools of classification. But even without the steps of hypothesizing and testing, the systematic identification of variation can inform citizens and policy makers.
In offering general concepts, I hope to help define the fragmented field of surveillance studies and contribute to the broader field of the sociology of information. Scholars are often so busy tending their small gardens that they miss activity in adjacent fields, let alone plant history. Species diversity with its genius for niche finding need not preclude cross-pollination. Intellectual anarchy and the absence of central direction may have their virtues, given the not-infrequent tilt of authority toward self-perpetuation, parochialism, and corruption. However, as a field matures, there is need for cumulative scholarship and integration. Concept development of the kind suggested here can contribute to this by offering a common language and foundation.2
Chapter 1 deals with basic definitions. Chapter 2 identifies the attributes of surveillance tools. Chapter 3 is concerned with the many goals the tools can serve, and chapter 4 identifies the kinds of data they can gather. In these chapters on the social structures of surveillance, I have sought, as Erving Goffman advised, to contribute to the development of sociological concepts and to conceptual frameworks appropriate for both clothing the children and tenting the congregation.3
1
Defining the Terms of Surveillance Studies
We are at any moment those who separate the connected or connect the separate.
GEORG SIMMEL
Getting to my conceptual planet, country, region, neighborhood, house and room involves a series of permeable, moveable Russian dolls within dolls.
ROBERT K. CONJURETSKY
Whether in academic or popular discussions the term surveillance is often used in a vague, imprecise and, seemingly, self-evident fashion. That is also the case for accompanying terms such as privacy, publicity, secrecy, confidentiality, anonymity, identifiability, and borders, which can simply describe outcomes of surveillance practices or may involve rules designed to ensure or avoid such outcomes. This chapter first considers definitions of these terms. It then turns to a second set of concepts useful for analyzing the organization and structure of surveillance settings which produce such outcomes (e.g., the role played as an agent or subject of surveillance).
Two major forms of studying the topic can be noted: the surveillance essay and the focused empirical inquiry. The surveillance essay grows out of the theoretical traditions of political economy, social control, law and society, and criminology. Such essays tend to draw on and extend the work of Michel Foucault (although he was writing about earlier centuries); and further in the background the ideas of Frederick W. Taylor, Weber, Nietzsche, Marx, Bentham, Rousseau, and Hobbes; and even further back the watchful and potentially wrathful eye of the biblical God of the Old Testament.1 (The ancient of course can be combined with the most modern; see the warning in a church’s parking lot in fig. 1.1.)
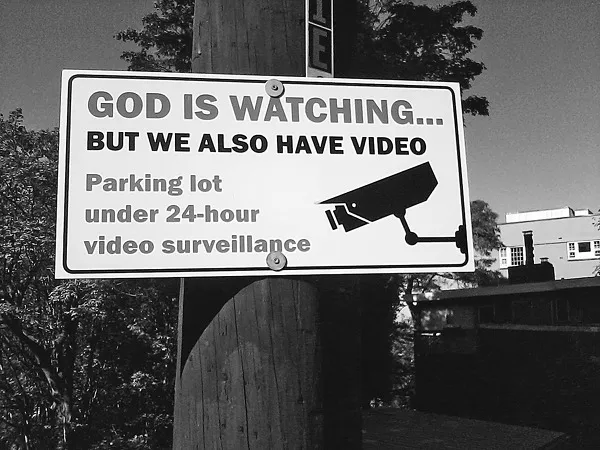
Figure 1.1. Church parking lot: You are not alone.
The surveillance essay seeks to capture the appearance of a new kind of society but without enough specificity to take us beyond very general statements. (See chap. 2, table 2.1). It generally does not begin by offering an inclusive definition of surveillance, nor does it identify components that would systematically permit differentiating the new from the old forms, making comparisons within and across these, or seeing what is universal in human societies.
If the theoretical essays tend to be too broad, the focused empirical inquiries are often too narrowing, divorced from larger questions and too often unaware of research in nearby fields. Many empirical studies focus on only one technology, such as databases, work, communication and location monitoring, drug testing, or video (the most frequently written-about forms). This is often done within a single institutional context such as employment, education, or law enforcement, rather than across contexts. The occasional studies that are more comparative, looking across technologies or settings, generally do so with a single disciplinary focus or method. The work of some journalists and text writers is an exception, although their emphasis is usually on summarizing the literature, rather than extending it.
The numerous strands of theory and research in geographically and academically diverse areas indicate a boom, yet there is a lack of integration (and even awareness) among literatures. They do not adequately build on each other. There are relatively few middle-range approaches involving systematic empirical inquiry guided by an effort to assess ideas using standard terms or measures. There is a need for increased communication between fields, improved definition and operationalization of concepts, and nuanced abstractions filled with systematic empirical content. There’s too much confusion, duplication, and people talking past each other as they impute different meanings to the same words. There must be some way out of here (as the joker said to the thief). An important first step in overcoming these limitations is to develop better definitions of concepts and a clearer picture of how they connect. We begin with surveillance and the concepts that encircle and cut through it.
Surveillance, Traditional Surveillance, and the New Surveillance
Prepare the table, watch in the watchtower . . . anoint the shield. . . . Go, set a watchman, let him declare what he seeth!
ISAIAH: 21:5, 6
The English noun surveillance comes from the French verb surveillir. It is related to the Latin term vigilare with its hint that something vaguely sinister or threatening lurks beyond the watchtower and town walls. Still, the threat might be successfully warded off by the vigilant. This ancient meaning is reflected in the narrow association many persons still make of surveillance with the activities of police and national security agencies. Yet in contemporary society the term has a far wider meaning. What is surveillance? Dictionary, thesaurus, and popular usage suggest a set of related activities: look, observe, watch, supervise, control, gaze, stare, view, shadow, scrutinize, examine, check out, scan, screen, inspect, survey, glean, scope, monitor, track, follow, tail, bug, spy, eavesdrop, test, guard. While some of these are more inclusive than others and can be logically linked (e.g., moving from looking to monitoring), and while we might tease out subtle and distinctive meanings for each involving a particular sense, activity, or function, they all reflect what the philosopher Ludwig Wittgenstein calls a family of meanings within the broader concept.
At the most general level, surveillance of humans (often, but not necessarily synonymous with human surveillance) can be defined as regard for or attendance to a person or factors presumed to be associated with a person. A central feature is gathering some form of data connectable to an individual (whether uniquely identified or as a member of a category). Gathering is a many-splendored thing.
In his analysis of “the look” Sartre illustrates a basic distinction. He describes a situation in which an observer is listening from behind a closed door while peeking through a keyhole when “all of a sudden I hear footsteps in the hall” (1993). He becomes aware that he himself will now be observed. In both cases he is involved in acts of surveillance, but these are very different forms. In the latter case he simply responds and draws a conclusion from a state of awareness. In the former he has taken the initiative, actively and purposively using his senses.
Surveillance can simply mean the routine, autopilot, semiconscious, and often even instinctual awareness in which our sense receptors are at the ready, constantly receiving inputs from whatever is in perceptual range. Hearing a noise that might or might not be a car’s backfire and looking before crossing the street are surveillance examples. Drawing conclusions about the gender, age, appearance, and location of those walking toward us as pedestrians (and the need to appropriately orient ourselves so that we don’t collide) can be included, as would overhearing a cell phone or restaurant conversation. A census, an opinion or public health survey, an informer’s activities, a pacemaker’s readings, a poker player interpreting opponents’ expressions, a uranium miner being monitored for radio activity, and a computer mining data from credit card use all fit the definition as well.
Within this broad definition, the degree of self-conscious awareness of the act, intentionality, and effort vary greatly, as well as do subsequent efforts that may include trying to block out or avoid what is taken in, as well as trying to magnify it.
Thus, we can identify one form of surveillance as attentiveness or wakefulness in which an agent, with minimal malice or benign aforethought, consumes data from a subject without directly seeking it. This involves a passive, nonreflective and reactive response to the environment. This can be called nonstrategic surveillance. The natural world simply serves up data to the unaided senses.
This contrasts with cases of strategic surveillance. Strategic surveillance often involves an adversarial context in which the subject withholds (or at least does not offer) information. Thus, the surveillance may have an inquisitorial, discovery component. In turn, the subject may engage in information protection and other practices designed to shape what an agent discovers. Or the surveillance may involve information that is waiting to be discovered, unveiled, located, created, collected, or collated, or it may involve information that is known but needs to be validated.
Within the strategic form—which to varying degrees ferrets out what is not freely offered—we can distinguish two mechanisms intended to create (or prohibit) conditions of visibility and legibility—material tools that enhance (or block) the senses and rules about the surveillance itself. While these are independent of each other, they show common linkages, as with rules requiring reporting when there are no available tools for discovery or rules about the conditions of use for tools that are available. A...
Table of contents
- Cover
- Title Page
- Copyright Page
- Contents
- Preface
- Acknowledgments
- Introduction
- PART I: Concepts: The Need for a Modest but Persistent Analyticity
- PART II: Social Processes
- PART III: Culture and Contexts
- PART IV: Ethics and Policy
- Appendix: A Note on Values: Neither Technophobe nor Technophile
- Notes
- References
- Index