
Managing Security Services in Heterogenous Networks
Confidentiality, Integrity, Availability, Authentication, and Access Control
- 182 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Managing Security Services in Heterogenous Networks
Confidentiality, Integrity, Availability, Authentication, and Access Control
About this book
A heterogeneous network is a network which connects computers and other devices with different operating systems, protocols, or access technologies. By definition, managing heterogenous networks is more difficult that homogenous networks. Confidentiality, integrity, availability (CIA) remain the foundation of security. This book sheds light upon security threats, defenses, and remediation on various networking and data processing domains, including wired networks, wireless networks, mobile ad-hoc networks, wireless sensor networks, and social networks through the prisms of confidentiality, integrity, availability, authentication, and access control.
The book is broken into different chapters that explore central subjects and themes in the development of the heterogenous networks we see today. The chapters look at:
- Access control methods in cloud-enabled Internet of Things
- Secure routing algorithms for mobile ad-hoc networks
- Building security trust in mobile ad-hoc networks using soft computing methods
- The use and development of Blockchain technology, with a particular focus on the nonce-free hash generation in Blockchain
- Password authentication and keystroke biometrics
- Health care data analytics over Big Data
- Bluetooth: and its open issues for managing security services in heterogenous networks
Managing Security Services in Heterogenous Networks will be a valuable resource for a whole host of undergraduate and postgraduate students studying related topics, as well as career professionals who have to effectively manage heterogenous networks in the workplace.
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app.
Information
1
Access Control Methods in the Cloud-Enabled Internet of Things
Department of Computer Science and Engineering, Vasavi College of Engineering, Hyderabad, Telangana
Department of Computer Science and Engineering, Indian Institute of Information Technology Dharwad, Karnataka
1.1 Introduction
1.1.1 The Network of Things
- Sensors that measure the physical parameters that are of interest such as temperature, humidity, pressure, weight, etc.
- Aggregators that convert the raw data into processed or aggregated data.
- Communication channel that allows data transmission among the entities involved.
- External utilities include external components required for the computation.
- Decision triggera are predicates that have true values used to initiate a command or action.
- Sensing Layer – Acts as an interface between the physical world and cyber world, sensing and collecting data with the help of sensors, cameras, radio frequency identification (RFID), etc.
- Networking Layer – Provides networking support for data transmission and collection and control applications.
- Service Layer – Acts as middleware to support business logic and service integration.
- Interface Layer – Provides an interface to seamlessly integrate the service layer with end users.
1.2 The IoT Application Domain
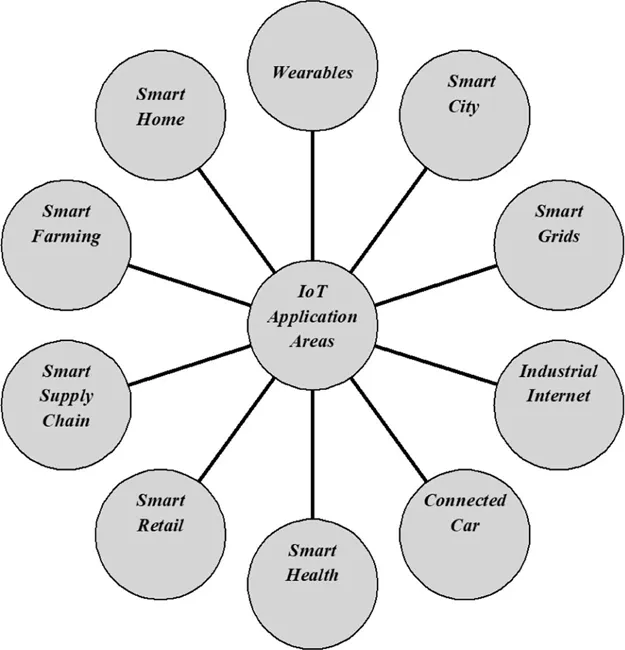
1.3 Cloud Computing
1.3.1 Essential Characteristics
1.3.2 Deployment Models
1.3.3 Service Models
1.4 Motivation
1.5 Preliminaries
1.5.1 Role-Based Access Control
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Contents
- Chapter 1 Access Control Methods in the Cloud-Enabled Internet of Things
- Chapter 2 an Intelligent Weighted Fuzzy Cluster-Based Secure Routing Algorithm for Mobile ad-hoc Networks
- Chapter 3 Ensuring Security through Trust in Mobile ad-hoc Networks Using Soft Computing Methods
- Chapter 4 Proof of Virtue: Nonce-Free Hash Generation in Blockchain
- Chapter 5 Password Authentication Using Keystroke Biometric
- Chapter 6 Healthcare Data Analytics over Big Data
- Chapter 7 Bluetooth: State of the Art, Taxonomy, and Open Issues for Managing Security Services in Heterogeneous Networks
- Index