
eBook - ePub
Information Security Policies and Procedures
A Practitioner's Reference, Second Edition
- 408 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Information Security Policies and Procedures
A Practitioner's Reference, Second Edition
About this book
Information Security Policies and Procedures: A Practitioner's Reference, Second Edition illustrates how policies and procedures support the efficient running of an organization. This book is divided into two parts, an overview of security policies and procedures, and an information security reference guide. This volume points out how securi
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part 1
Information Security Policies and Procedures
Years ago, I saw a cartoon in magazine that showed a huge construction project in downtown Manhattan. There was this massive hole and the crews were busy excavating even deeper, there was a great deal of activity, and in the foreground two men were reviewing the blueprints when one began to yell, “The prints are upside down!” I had that cartoon up in my office for a number of years as a way to remind me that the goal of writing policies and procedures is to provide a clear “blueprint” on how tasks are to be done.
The following material is a blueprint on how to begin to develop policies and procedures. My goal is to provide readers with enough information and examples so that they can be successful. The old adage, “Give a person a fish and they can eat today; teach a person to fish and they can eat for a lifetime” is the direction this document takes. While it is important to provide examples, it is more important to explain why and how things are done. This book was written with the goal of transferring knowledge to the reader. No two organizations are exactly alike, so no two sets of policies and procedures are going to be exactly alike. Knowing what to do and how to present the material is the best method for success.
Being charged with developing policies and procedures might seem to be an overwhelming task. So take the material and examine the examples and modify them to meet the needs and culture of your organization. Use the discussion material provided in this information security reference guide to help sell the concepts. Above all, have fun. You are going to learn more about your organization than just about anyone. Once you have completed a policy or two, you will have the courage to take on even more tasks. The skills needed to write policies and procedures will assist you in all other areas of your professional and private life.
You will be able to express an idea in a clear and concise manner. You will be organized and will be able to work to a deadline. You will be able to create a project plan and manage the work of others. Above all, you will have the satisfaction of knowing that you have created something that will still be in effect after you have moved on.
Chapter 1
Introduction
As security professionals, we often take the view that the overall objective of an information security program is to protect the integrity, confidentiality, and availability of that information. Although this is true from a security perspective, it is not the organization objective. Information is an asset and is the property of the organization. As it is an asset, management is expected to ensure that appropriate levels of control are in place to protect this resource.
An information protection program should be part of any organization’s overall asset protection program. This program is not established to meet security needs or audit requirements; it is a business process that provides management with the processes needed to perform the fiduciary responsibility. Management is charged with a trust to ensure that adequate controls are in place to protect the assets of the enterprise. An information security program that includes policies, standards, and procedures will allow management to demonstrate a standard of care.
As information security professionals, it is our responsibility to implement policies that reflect the business and mission needs of the enterprise. This chapter examines the reasons why information security policies are needed and how they fit into all elements of the organization. The development of information security policies is neither an information technology or audit responsibility, nor do these policies remain solely in these areas. The concept of information security must permeate through all of the organization’s policies.
In this chapter, we discuss 11 organizationwide policies and, at a minimum, what each should have with reference to information security. The policies that we initially discuss are high-level (Tier 1) organization-wide policies and include the following:
- • Employment Practices
- • Employee Standards of Conduct
- • Conflict of Interest
- • Performance Management
- • Employee Discipline
- • Information Security
- • Corporate Communications
- • Procurement and Contracts
- • Records Management
- • Asset Classification
- • Workplace Security
- • Business Continuity Planning
We discuss the different levels of policies — Tier 2 policies (topic specific) and Tier 3 policies (application specific) — throughout the remainder of the book.
1 CORPORATE POLICIES
Most organizations have a standard set of policies that govern the way they perform their business (see Figure 1). There are at least 11 Tier 1 policies; this means that a policy is implemented to support the entire business or mission of the enterprise. There are also Tier 2 policies; these are topic-specific policies and address issues related to specific subject matter. Tier 3 policies address the requirements for using and supporting specific applications. Later in the book we present examples of a number of each of these policies; for now, we present the Tier 1 policy title and a brief description of what each policy encompasses.
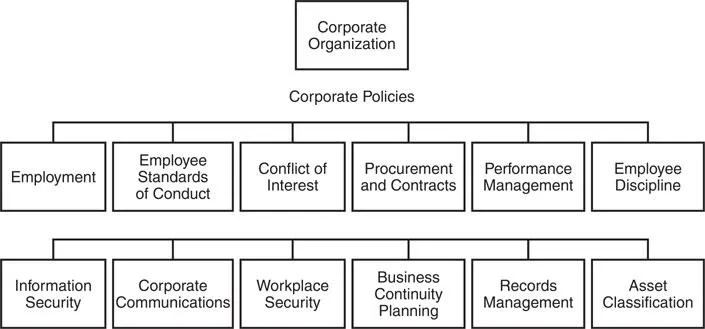
2 ORGANIZATIONWIDE (TIER 1) POLICIES1
Employment Practices. This is the policy that describes the processes required to ensure that all candidates get an equal opportunity when seeking a position with the organization. This policy discusses the organization’s hiring practices and new employee orientation. It is during the orientation phase that new employees should receive their first introduction to the information security requirements. Included in this process is a Non-Disclosure Agreement or Confidentiality Agreement. These agreements require the signatory to keep confidential information secret and generally remain in effect even after the employee leaves the organization.
The employment policies should also include condition-of-employment requirements such as background checks for key management levels or certain jobs. A side part to the Employment policy and the Performance policy is the publication of job descriptions for every job level. These descriptions should include what is expected of employees regarding information security requirements.
Standards of Conduct. This policy addresses what is expected of employees and how they are to conduct themselves when on company property or when representing the organization. This policy normally discusses examples of unacceptable behavior (dishonesty, sleeping on the job, substance abuse, introduction of unauthorized software into company systems) and the penalties for infractions. Also included in this policy is a statement that “Company management has the responsibility to manage enterprise information, personnel, and physical properties relevant to their business operations, as well as the right to monitor the actual utilization of these enterprise assets.”
Information security should also address confidential information: “Employees shall also maintain the confidentiality o...
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Dedication
- Table of Contents
- Acknowledgments
- About the Author
- Introduction
- Part 1 Information Security Policies and Procedures
- Part 2 Information Security Reference Guide
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Information Security Policies and Procedures by Thomas R. Peltier in PDF and/or ePUB format, as well as other popular books in Business & Cyber Security. We have over one million books available in our catalogue for you to explore.