
- 664 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Dynamic Web Programming and HTML5
About this book
With organizations and individuals increasingly dependent on the Web, the need for competent, well-trained Web developers and maintainers is growing. Helping readers master Web development, Dynamic Web Programming and HTML5 covers specific Web programming languages, APIs, and coding techniques and provides an in-depth understanding of the underlyin
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
The Web: An Overview
Ever since its beginning in the early 1980s, the Web has been evolving and maturing. Today, the Web’s impact on how industries, governments, institutions, and individuals conduct business and socialize, is ever expanding. It is not surprising that the need for well-trained people to develop and program websites is increasing at a rapid pace.
The Web involves networking, protocols, servers, clients as well as languages, services, and user interfaces. Thus, the Web is a rather complicated arena, and mastering Web development involves in-depth understanding and working experience with all the involved technologies and how to combine them for specific functions and effects.
Even for people who will not become Web professionals, a good understanding of the Web, how it relates to the Internet, and what makes it tick will be valuable in many a workplace.
The overview in this chapter sets up the scene and the context within which to study and apply the specific languages and programming techniques for building well-developed and dynamic websites.
1.1 Web Is Part of the Internet
For the vast majority of computer users, getting online means browsing the Web. That is how important the Web has become in our daily lives. But of course the Web is just one among many services available on the Internet. These include email, file transfer, remote login, audio and video streaming, and many more.
The Internet spans the globe by connecting computer networks together. Such networks include local area networks (LANs) in office buildings, college campuses, and homes, as well as wide area networks (WANs) that cover whole cities or even countries. The Internet enables each connected computer, called a host, to communicate with any other hosts.
In addition to host computers, the network infrastructure itself involves dedicated computers that perform network functions: hubs, switches, bridges, routers, and gateways. For programs and computers from different vendors, under different operating systems, to communicate on a network, a detailed set of rules and conventions must be established for all parties to follow. Such rules are known as networking protocols. We use different networking services for different purposes; therefore, each network service defines its own protocol that adds specific features to existing, more general, underlying protocols. Protocols govern such details as
• Address format of hosts and processes
• Data format
• Manner of data transmission
• Sequencing and addressing of messages
• Initiating and terminating connections
• Establishing services
• Accessing services
• Data integrity, privacy, and security
Thus, for a program on one host to communicate with another program on a different host, both programs must follow the same protocol. The Open System Interconnect (OSI) Reference Model (Figure 1.1) provides a standard layered view of networking protocols and their interdependence. The corresponding layers on different hosts, and inside the network infrastructure, perform complementary tasks to make the connection between the communicating processes (
P1 and P2 in Figure 1.1).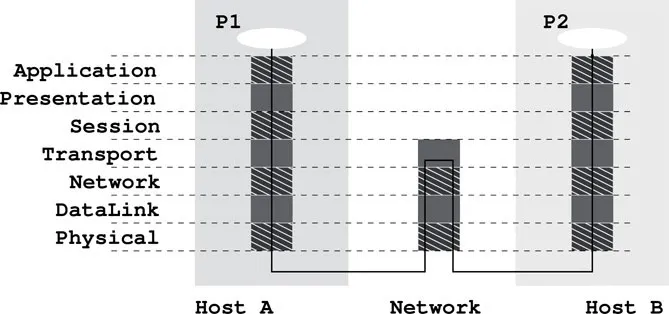
The Internet uses the Internet Protocol Suite. The basic IP (Internet Protocol ) is a network layer protocol. The TCP (Transport Control Protocol ) and UDP (User Datagram Protocol ) are at the transport layer. The Web is a service that uses an application layer protocol known as HTTP (the Hypertext Transfer Protocol; Section 1.16).
Networking protocols are no mystery. Think about the protocol for making a telephone call. You (a client process) must pick up the phone, listen for the dial tone, dial a valid telephone number, and wait for the other side (the server process) to pick up the phone. Then you must say “hello,” identify yourself, and so on. This is a protocol from which you cannot deviate if you want the call to be made successfully through the telephone network, and it is clear why such a protocol is needed. The same is true of a computer program attempting to talk to another computer program through a computer network. The design of efficient and effective networking protocols for different network services is an important area in computer science.
1.2 IP Addresses and Domain Names
On the Internet, each host has a unique IP address, represented by a 32-bit number (four bytes). For example,
tiger, a host at Kent State, has the IP address 131.123.38.172 (Figure 1.2). This dot notation (or quad notation) gives the decimal value (0 to 255) of each byte.1 Similar to a telephone number, the leading digits of an IP address are like country codes and area codes while the trailing digits are like local numbers. A host may be configured with a fixed IP or may obtain an IP address assigned to it on-the-fly as it boots up and attempts to connect to the network initially.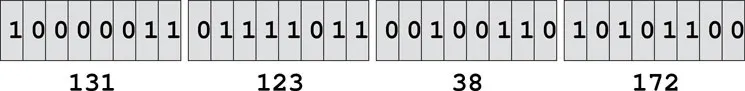
Because of their numerical nature, the dot notation is easy on machines but hard on users. Therefore, each host also has a unique domain-based name composed of words, rather like a postal address. For example, the domain name for
tiger is tiger.cs.kent.edu (at Department of Computer Science, Kent State University). And the domain name for the author’s IT consulting website is sofpower.com where the companion website for this text book (sofpower.com/dwp, the DWP website) is located.With the domain names, the entire Internet host namespace is recursively divided into disjoint domains. The address for
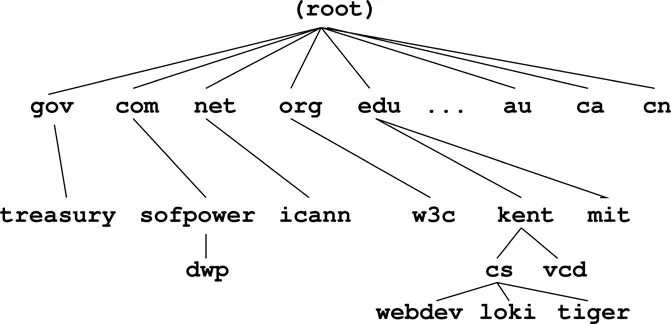
tiger puts it in the kent subdomain within edu, the generic top-level domain (generic TLD) for educational institutions. Other generic TLDs include org (nonprofit organizations), gov (government offices), mil (military installations), com (commercial outfits), net (network service providers), info (information sources), name (individuals), uk, (United Kingdom), cn (China), and so forth. In June 2011, the Internet Corporation for Assigned Names and Numbers (ICANN) began to allow the registration of user-owned TLDs by corporations and governments; such private TLDs are expensive to register and maintain.Within a local domain (e.g.,
cs.kent.edu), you can refer to computers by their host name alone (e.g., loki, dragon, tiger), but the full address must be used for hosts outside.Figure 1.3 shows the Internet domain name hierarchy. Each node of the DNS tree has a name (case insensitive) and the name of the root node is a single period (
.). A full domain name is formed by connecting all names leading from the host name to the root of the DNS tree. Following are some example full domain names:tiger.cs.kent.edu.
dwp.sofpower.com.
Often, the trailing period (
.) can ...Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Table of Contents
- Preface
- Introduction
- 1 The Web: An Overview
- 2 Webpage Markup with HTML5
- 3 Audio, Video, and More HTML5
- 4 Styling with CSS
- 5 Forms, PHP, and Form Processing
- 6 Dynamic User Interface with JavaScript
- 7 HTML5 DOM and APIs
- 8 Server-Side Programming with PHP
- 9 Database-Driven Websites
- 10 Web Hosting: Apache, PHP, and MySQL
- 11 XML, AJAX, and Web Services
- 12 SVG and MathML
- 13 HTML5 and Mobile Websites
- Appendices Online
- Website and Online Examples
- Bibliography
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Dynamic Web Programming and HTML5 by Paul S. Wang in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Science General. We have over one million books available in our catalogue for you to explore.